A vision-attribute-based method for identifying contraband in X-ray security inspection
A recognition method and X-ray technology, applied in the field of computer vision, can solve the problems of low efficiency, fatigue, and consumption of manpower and material resources in security inspection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0073] In order to make the object, technical scheme and advantages of the present invention clearer, below in conjunction with embodiment, specifically as figure 1 The shown algorithm flow chart further describes the present invention in detail. It should be understood that the specific embodiments described here are only used to explain the present invention, but not to limit the present invention.
[0074] Step 1: Collect target samples and make a data set. The specific description is as follows: the collected X-ray security images are divided into high-energy images and low-energy images. The present invention uses these two types of images to generate a new image as a training data set , the specific implementation is as follows:
[0075] (1) The present invention creates a new image layer, and each pixel of the image layer is calculated and offset by the high-energy map and the low-energy map, and its definition is as follows:
[0076]
[0077] Among them, w, h repr...
specific Embodiment approach
[0120] figure 1 It is the realization flowchart of the present invention, and the specific implementation mode is as follows:
[0121] 1. Preprocess the original image of X-ray security inspection to obtain a new 16-bit color image based on visual-attribute as a data set;
[0122] 2. Input the training set image into the darknet-53 network for feature extraction to obtain the feature layer;
[0123] 3. Input the feature layer into the yolo layer for candidate frame parameter extraction
[0124] 4. Send the candidate frame parameters to the loss calculation layer, and use the gradient descent algorithm to backpropagate to optimize the network parameters
[0125] 5. Input the test set image into the trained model for testing
[0126] 6. Calculate the model mAP value according to the test results and evaluate the model performance
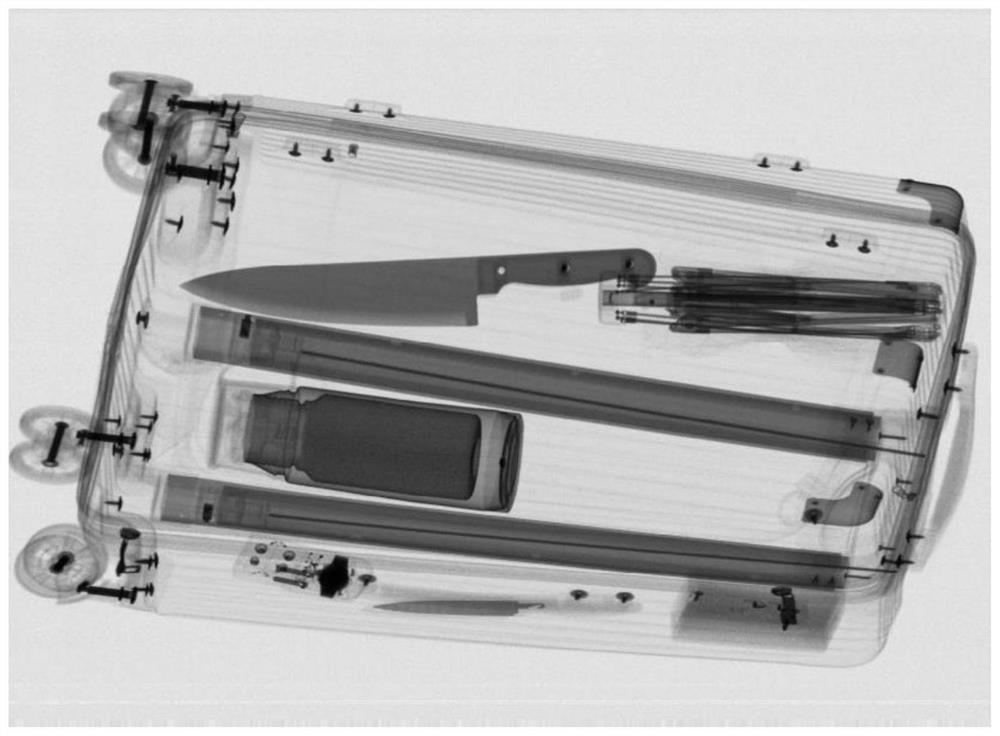
[0127] figure 2 : The embodiment synthesizes 16 three-channel images (grayscale display)
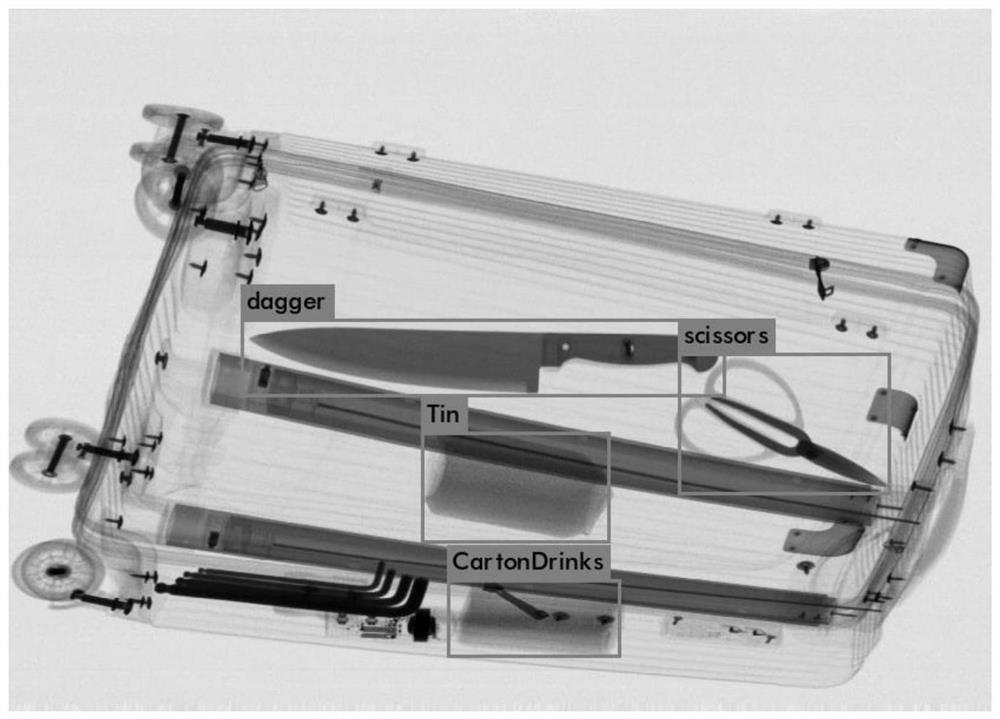
[0128] image 3 : Output image of contraband detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com