Improvement method for traditional ddos firewall syn flood protection in industrial network
A DDOS and industrial network technology, applied in transmission systems, electrical components, etc., can solve problems such as denial of service, insufficient CPU processing speed, and small memory capacity of SYNFlood attack targets, and achieve the effect of reducing memory usage time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, so that those skilled in the art can better understand the present invention and implement it, but the examples given are not intended to limit the present invention.
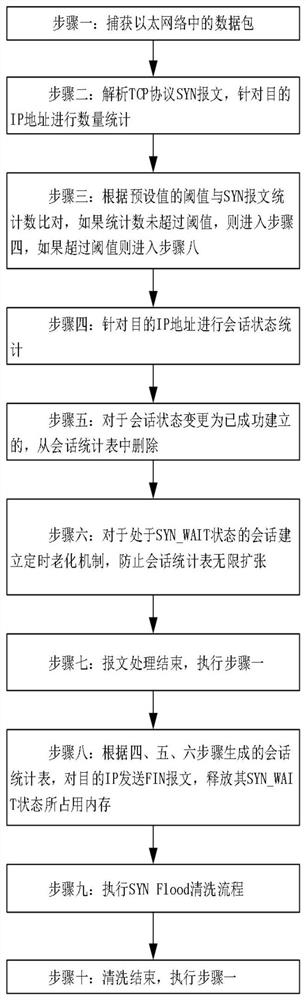
[0025] figure 1 It is a flow chart of the present invention, comprising the steps:
[0026] Step 1: Capture packets in the Ethernet network.
[0027] Step 2: Analyze the TCP protocol SYN message, and perform quantity statistics for the destination IP address.
[0028] Step 3: compare the preset threshold with the statistical number of SYN packets, if the statistical number does not exceed the threshold, go to step 4, and if it exceeds the threshold, go to step 8.
[0029] Step 4: Perform session state statistics for the destination IP address.
[0030] Step 5: If the session state is changed to successfully established, delete it from the statistical table.
[0031] Step 6: Es...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com