Data aggregation method for smart grid security and privacy protection based on fog computing
A smart grid and privacy protection technology, applied in the field of information security, can solve problems such as inability to obtain user privacy information, key escrow, and complex certificate management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The specific embodiments of the present invention will be described in further detail below with reference to the accompanying drawings.
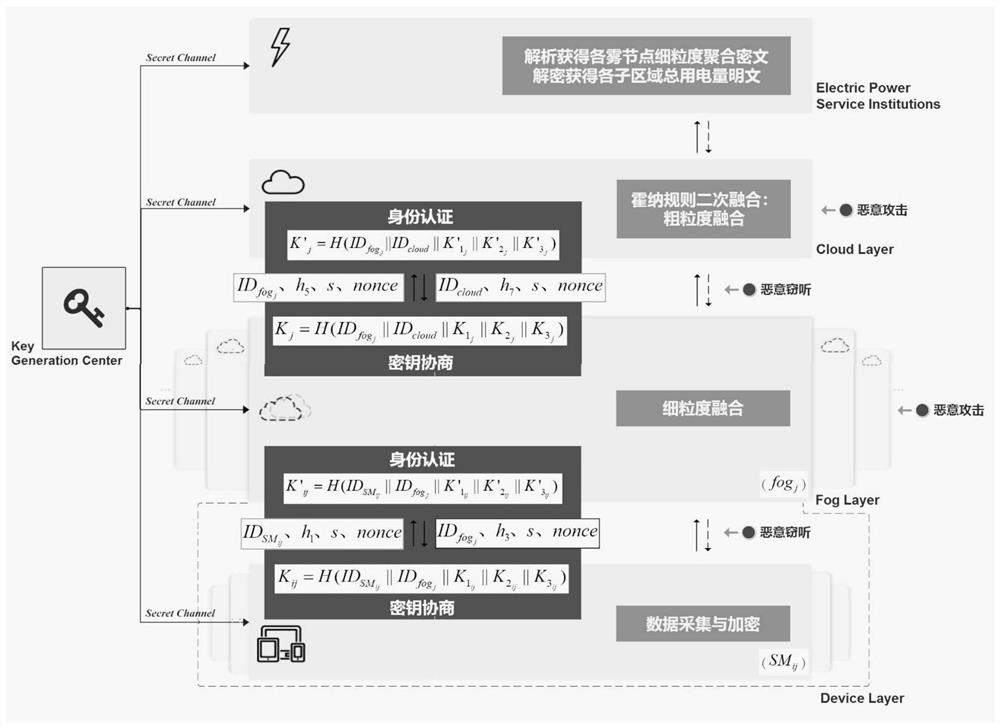
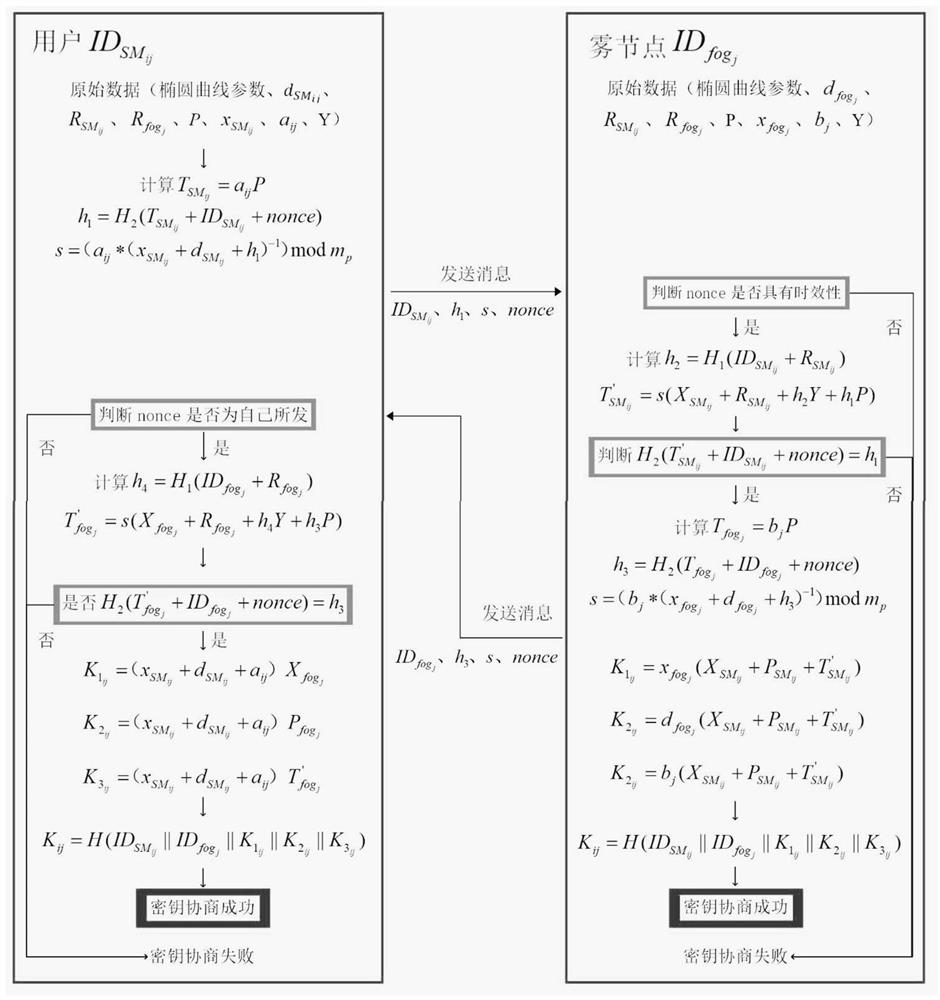
[0049] like figure 1 and figure 2 As shown, the present invention designs a data aggregation method for smart grid security and privacy protection based on fog computing. In the actual application process, the fog computing network consists of the device layer (smart meter), the fog layer, the cloud layer, the power service organization and the key generation center KGC. Consists of five parts. User smart meters collect, encrypt, and periodically upload user power consumption data reports. The fog layer nodes are responsible for fine-grained aggregation and relaying, and the cloud layer nodes are responsible for coarse-grained aggregation and re-relaying. Finally, the power service agency collects the coarse-grained aggregated data and transmits it. Process analysis. The smart grid security and privacy protection data aggregation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com