Fraud number identification method based on graph embedding
A recognition method and graph embedding technology, applied in the information field, can solve the problems of little effect, loss of fraudulent activities, inability to restore fraudulent patterns, etc., and achieve the effect of accurate recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
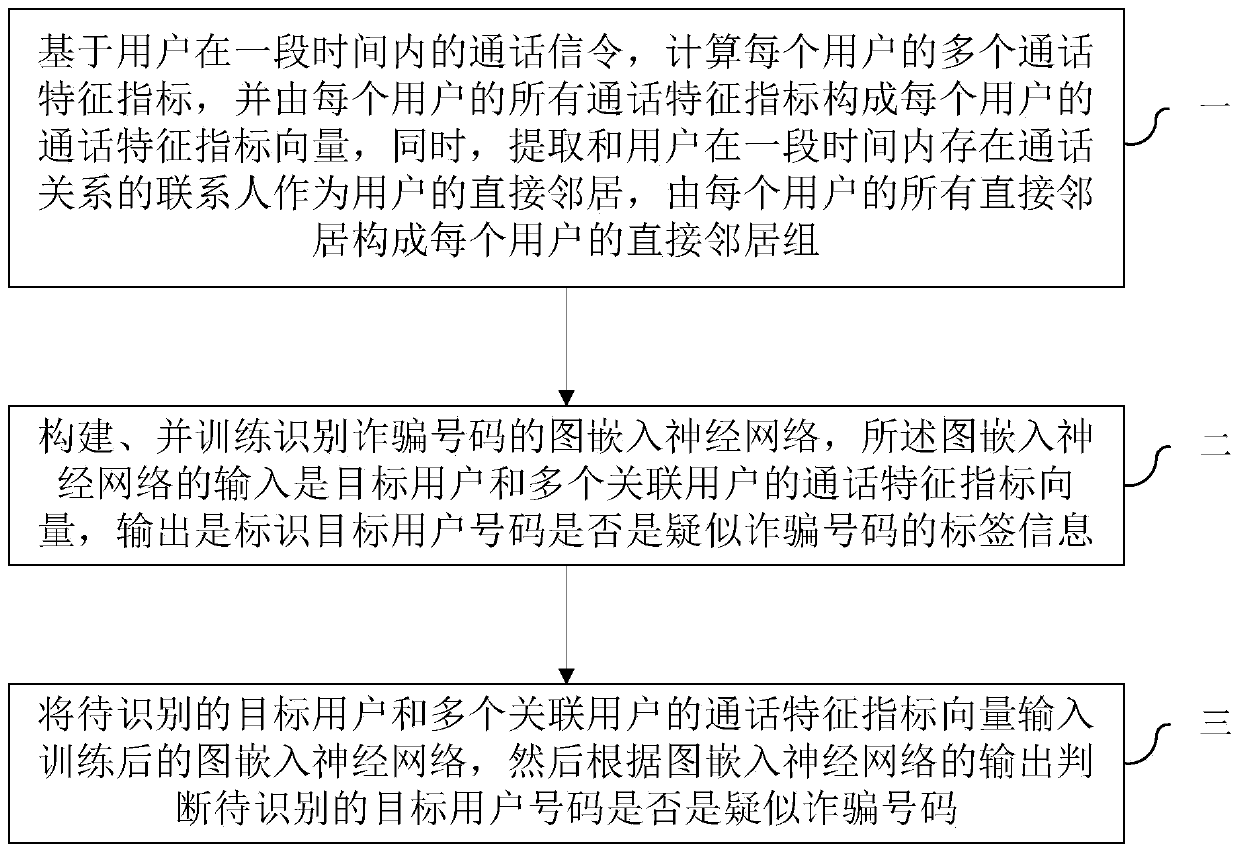
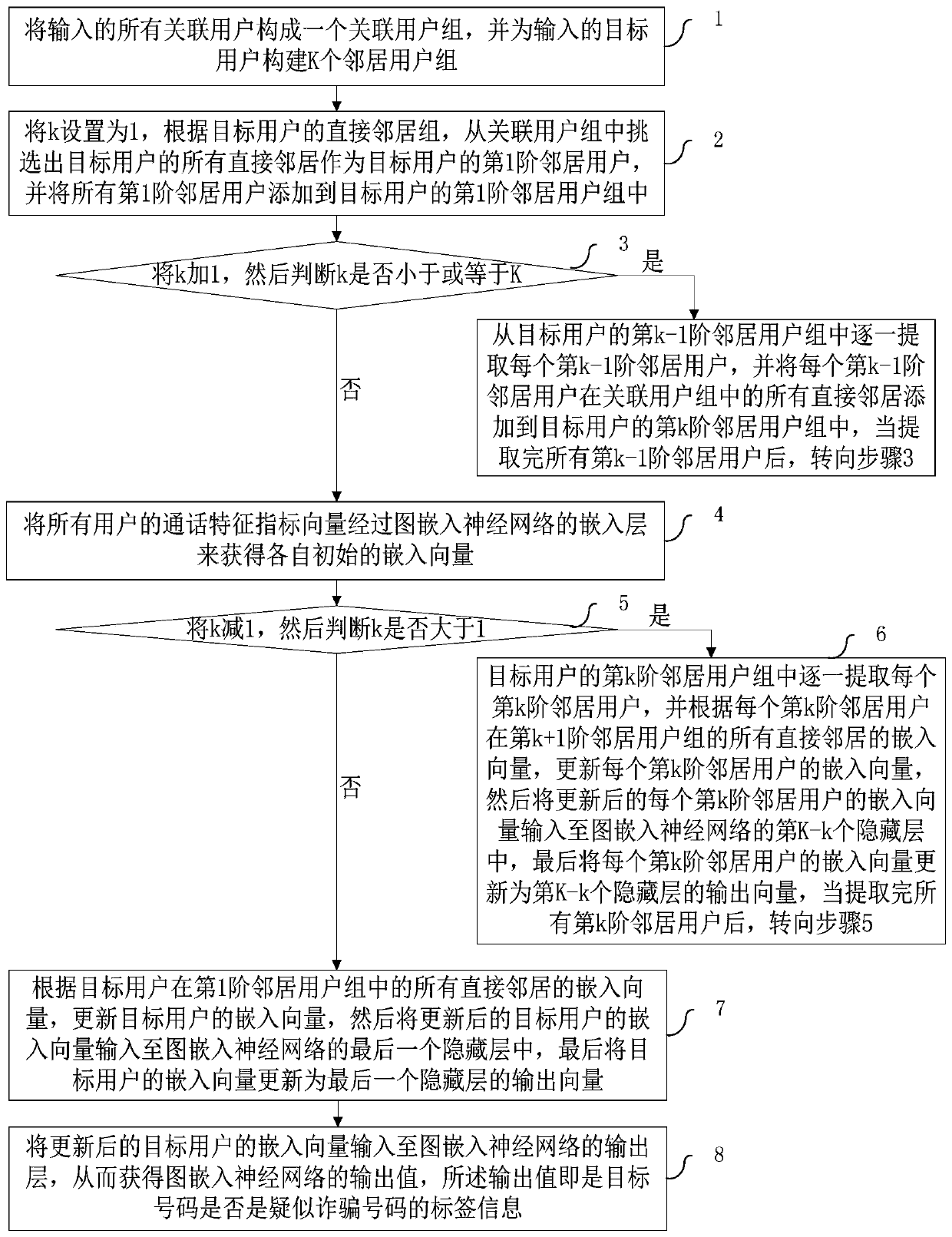
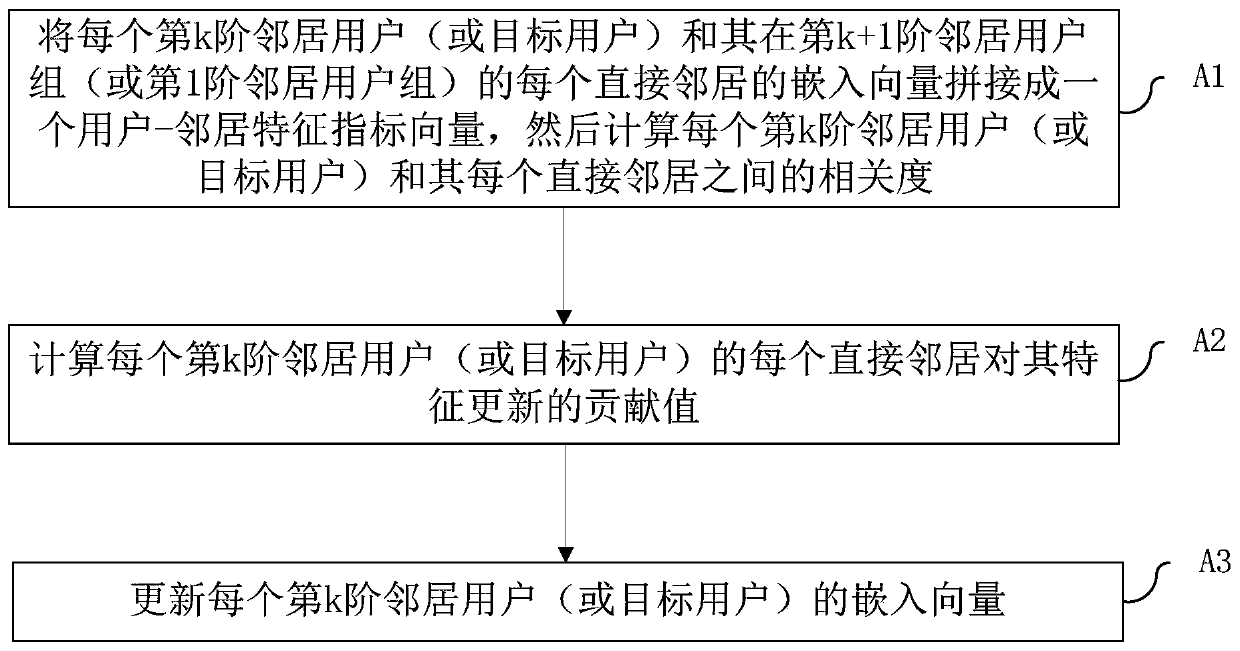
[0014] Such as figure 1 As shown, a kind of fraud number identification method based on graph embedding of the present invention comprises:
[0015] Step 1. Based on the user's call signaling within a period of time, calculate multiple call feature indicators for each user, and form a call feature index vector for each user from all call feature indicators of each user. At the same time, extract and user Contacts who have a call relationship within a period of time are regarded as the direct neighbors of the user, and all the direct neighbors of each user form the direct neighbor group of each user;
[0016] The call feature indicators in step 1 may include but not limited to: call frequency, number of called numbers, dispersion, busy hour rate, average call inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com