Method for realizing data fusion and data privacy protection based on Hash algorithm and session control
A technology of session control and data fusion, applied in digital data protection, database indexing, data processing applications, etc., can solve the problems of provider data value decline and highly sensitive information leakage, so as to ensure data privacy and data security, avoid data Depreciation, the effect of avoiding leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
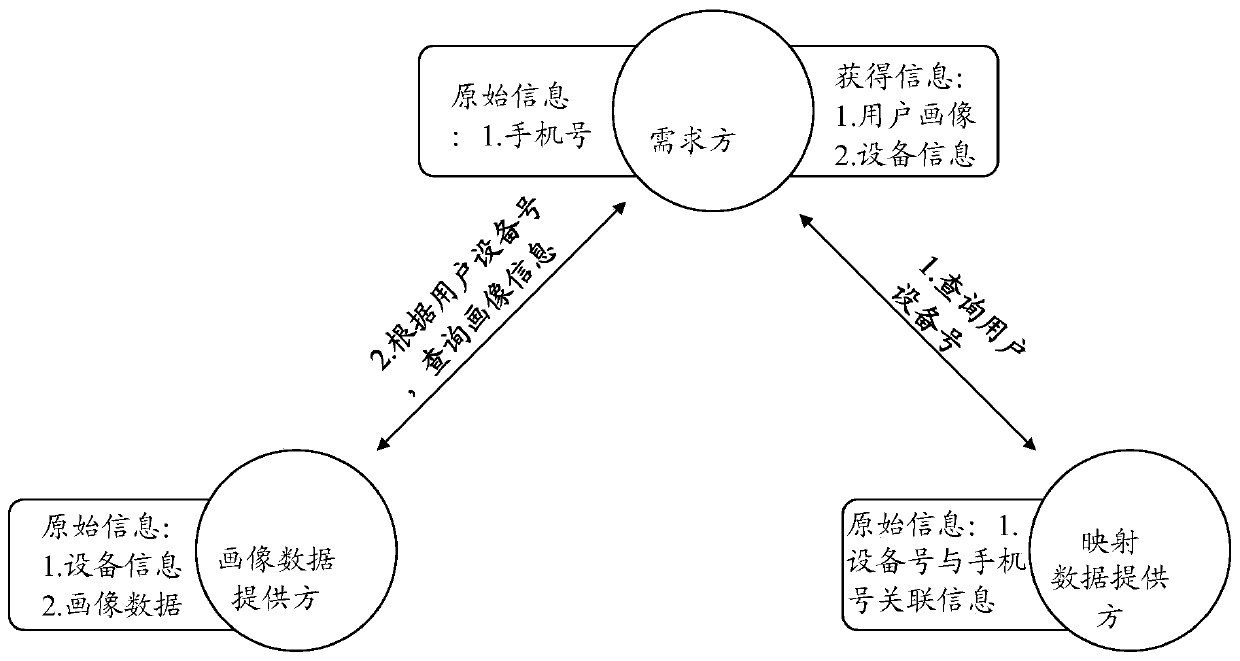
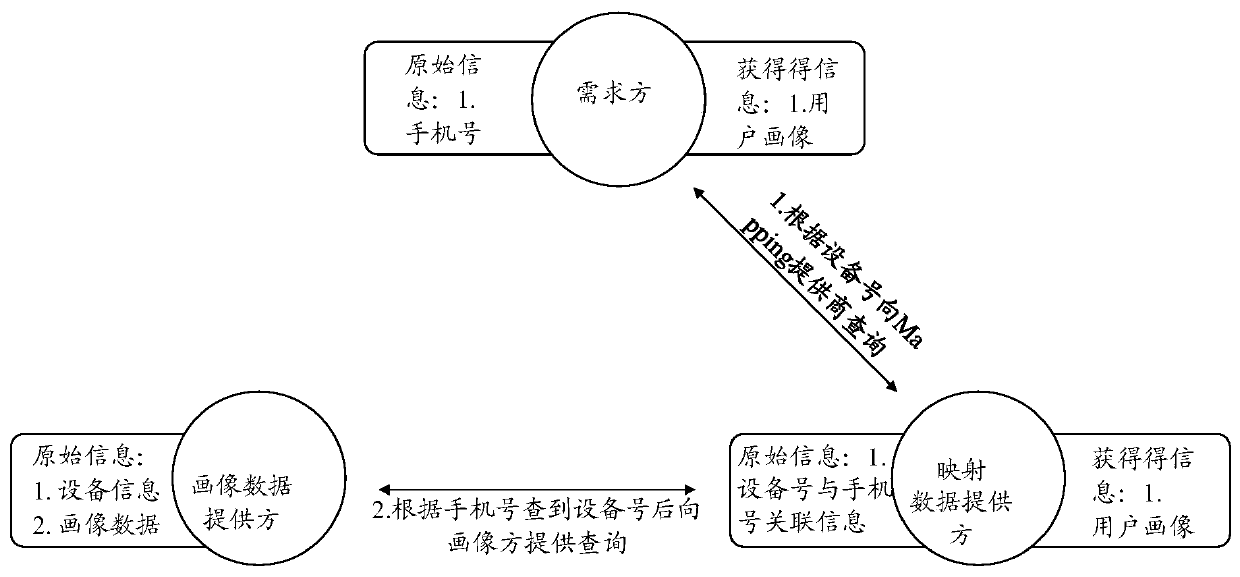
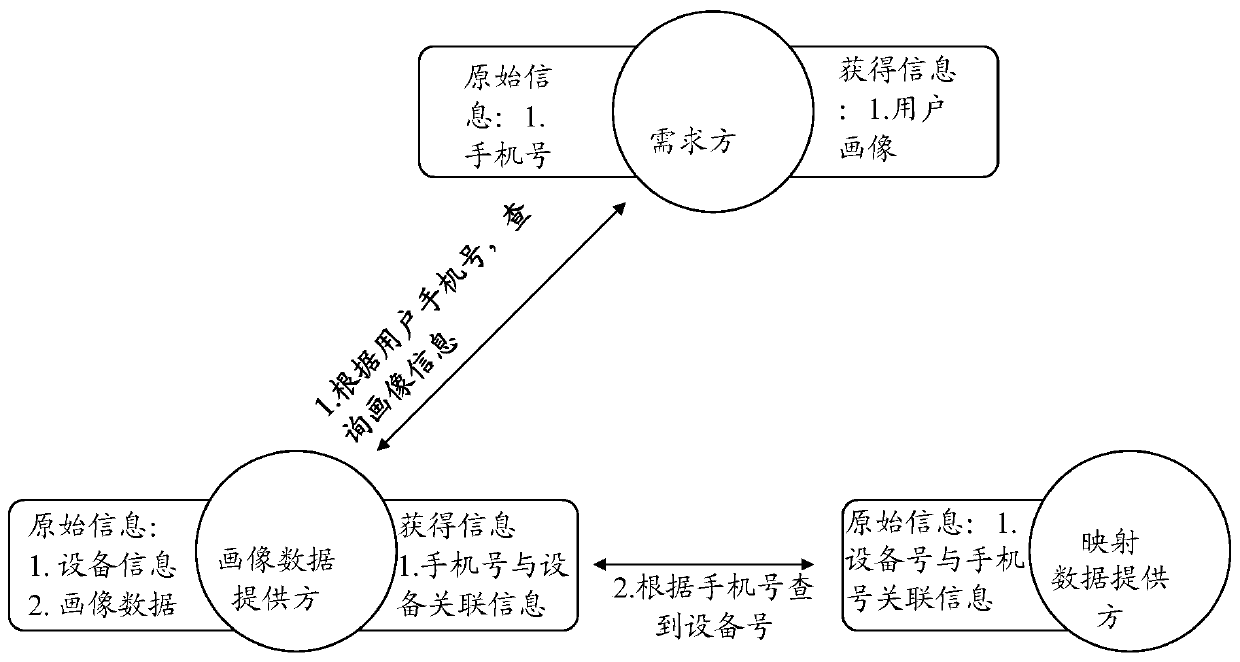
[0043] The method for realizing data fusion and data privacy protection based on hash algorithm and session control of the present invention comprises the following steps:
[0044] (1) The demand module sends a query request for the hash value of the mobile phone number to the mapping data providing module;
[0045] (2) The mapping data providing module queries whether there is the same mobile phone number hash data, and if it exists, returns the result to the demand module; otherwise, does not return the result;
[0046] (2.1) Query the corresponding mapping data according to the requested hash value;
[0047] (2.2) If there is corresponding mapping data, return the corresponding device number of the mobile phone to the demand module, and take the first n digits after hash calculation, and create a meetin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com