Method for detecting game plug-in based on URI (Universal Resource Identifier) characteristic of HTTP (Hyper Text Transfer Protocol) flow
A detection method and game technology, applied in indoor games, video games, sports accessories, etc., to achieve the effect of improving detection ability, improving accuracy, and increasing the difficulty of anti-detection and anti-monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings.
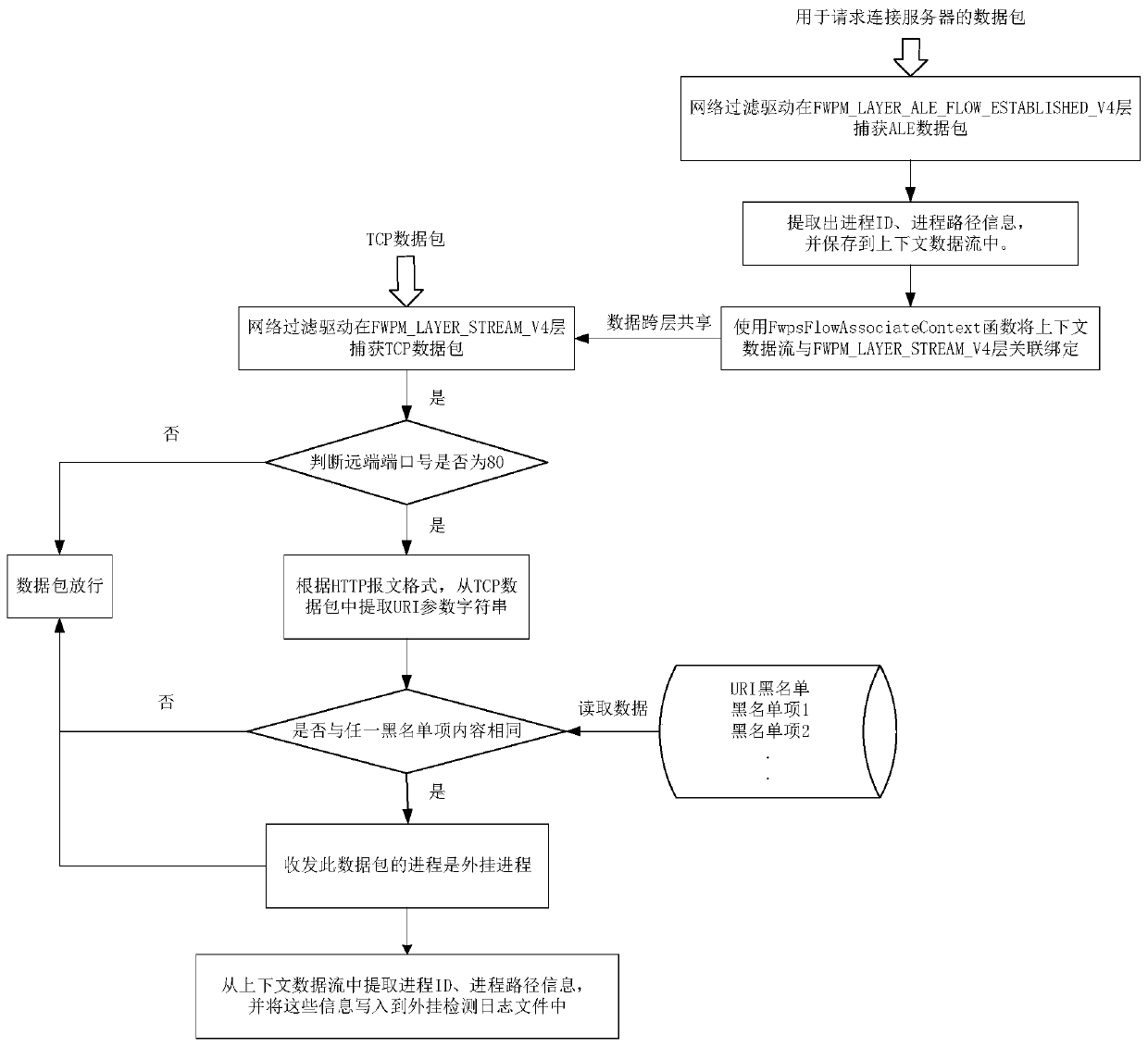
[0039] see figure 1 As shown, a kind of game plug-in detection method based on HTTP traffic URI feature of the present invention, described method comprises the following steps: Step S1, the client of Windows system application layer creates network filtering driver at driver layer;
[0040] Step S2, establish a URI blacklist, the URI blacklist stores the URI character string contained in the HTTP packet sent by the plug-in; the step S2 is further specifically: in the process of creating a network filter driver, the plug-in is carried out in the process of network interaction The URI that can be accessed is written into the file of the network filter driver, and the Windows system application program loads and starts the network filter driver; after the network filter driver is successfully opened, the URI blacklist is initialized. During the process of initializing the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com