Network flow control method and system and safety protection device
A network traffic and control system technology, applied in the fields of systems, security protection devices, and network traffic control methods, can solve problems such as poor network traffic protection effect, and achieve the goal of solving poor protection effect, overcoming network attacks, and improving network protection effect. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
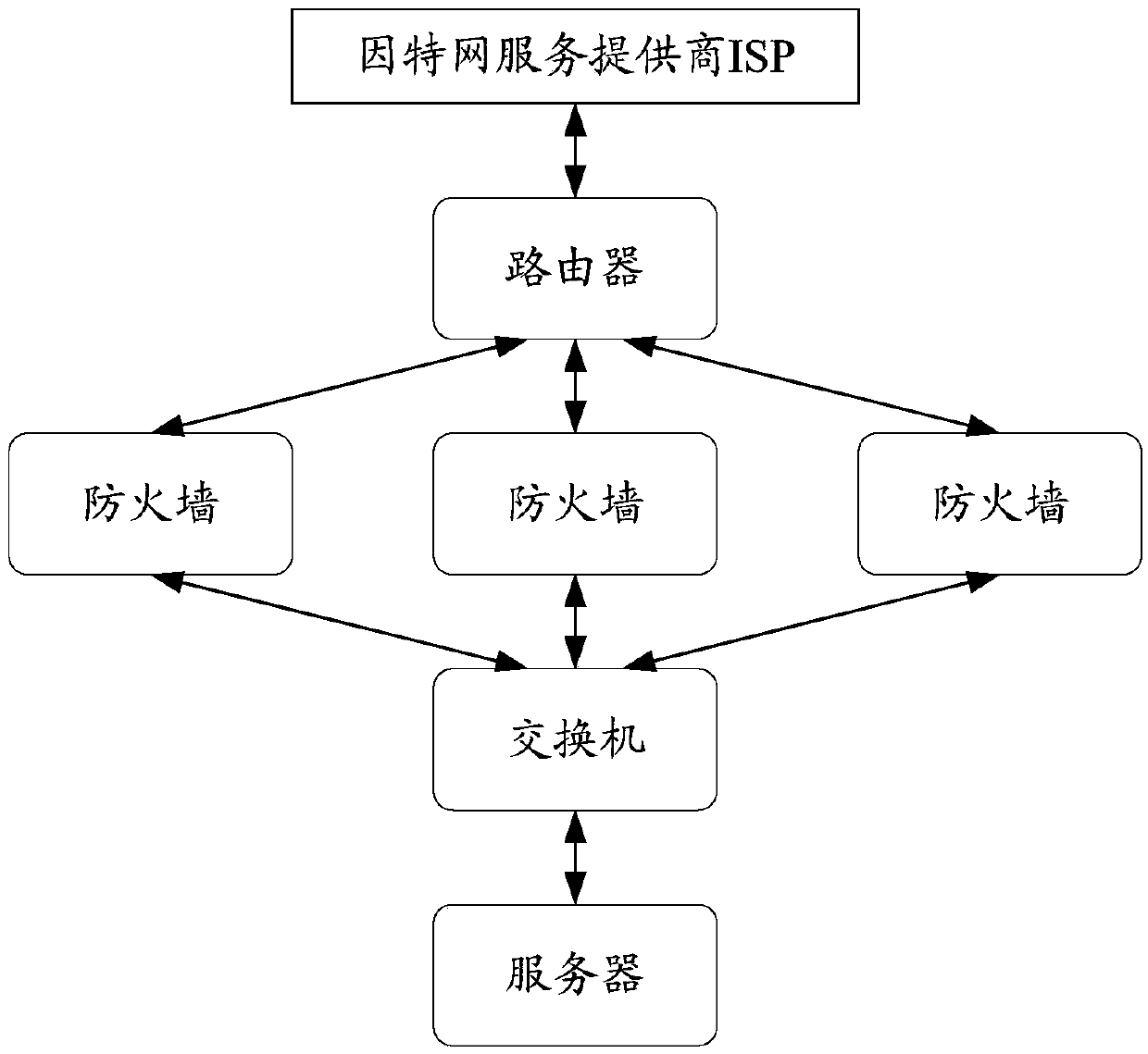
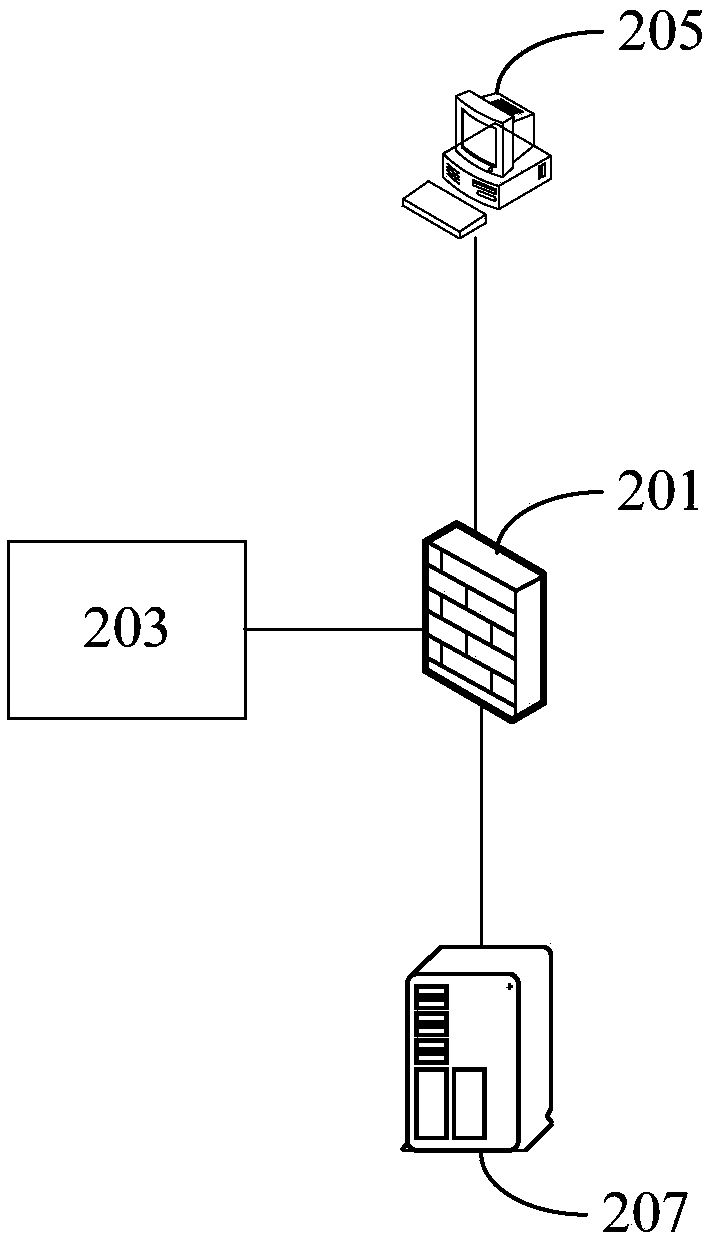
[0036] According to an embodiment of the present application, an embodiment of a network traffic control system is provided, which can be applied to network security protection between an internal network and an external network, between a private network and a public network, and between a computer and a network connected to it.
[0037]Due to the openness of the Internet, while the Internet brings convenience to people's life and work, people pay more and more attention to information security. As an isolation technology, a firewall can isolate any network between two networks (including but not limited to two internal networks, internal network and external network), or terminal devices (including but not limited to mobile phones, laptops, computers, tablets, etc.) A device that can be connected to the Internet) and the network communication traffic between the network are inspected, filtered and restricted to prevent unauthorized access, thereby ensuring the security of the...
Embodiment 2
[0067] According to the embodiment of the present application, an embodiment of a network traffic control method is also provided. This embodiment can be applied to the network traffic control system in Embodiment 1, including but not limited to the scenario in Embodiment 1. It should be noted that the steps shown in the flowcharts of the accompanying drawings may be performed in a computer system, such as a set of computer-executable instructions, and that although a logical order is shown in the flowcharts, in some cases, The steps shown or described may be performed in an order different than here.
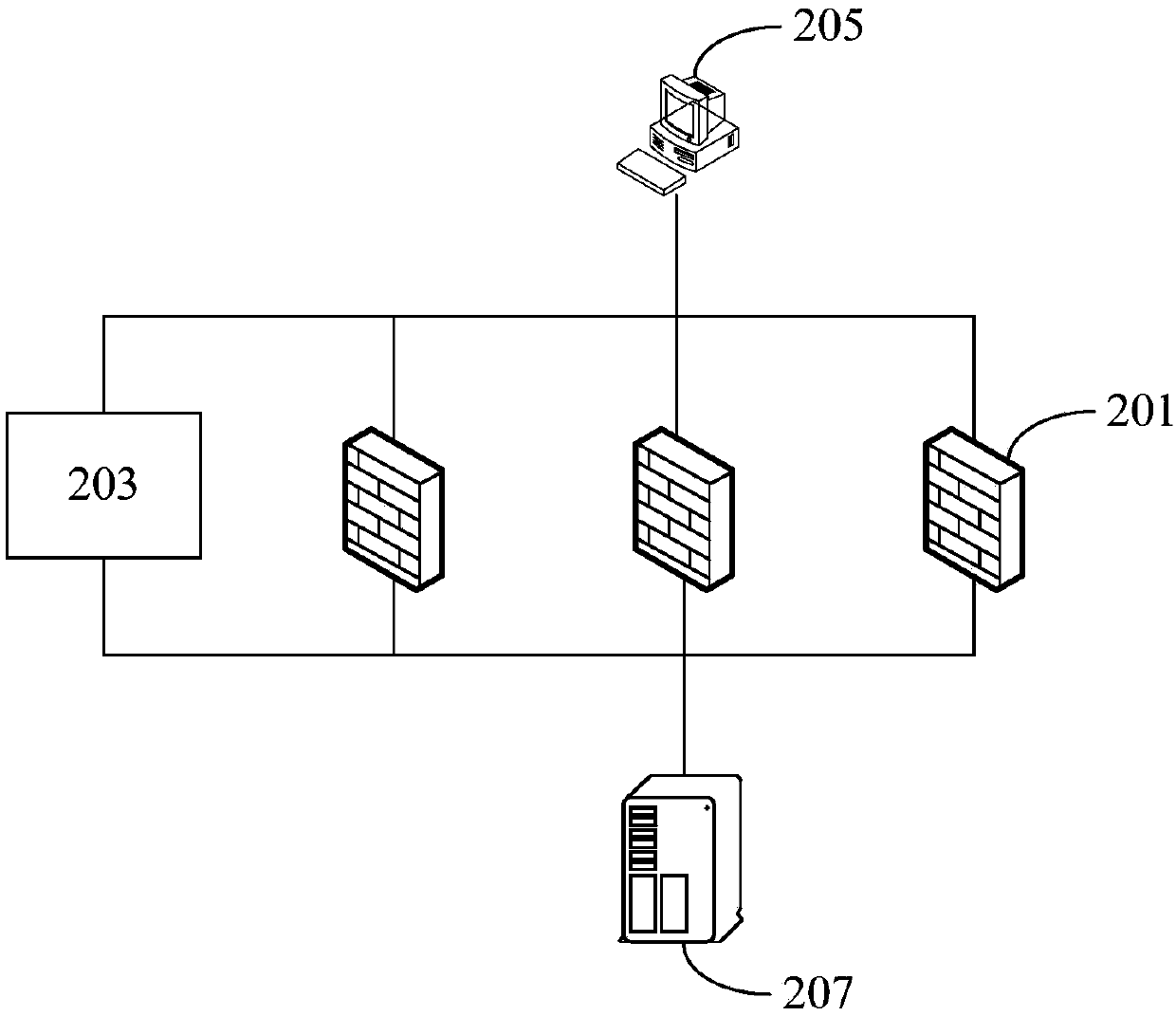
[0068] Because the existing technology uses multiple firewalls connected in parallel to form a firewall cluster to realize the function of a traditional single firewall, although the problem that network services or applications are affected by the firewall bandwidth due to the access of a single firewall can be overcome, due to the scattered flow of network traffic With multip...
Embodiment 3
[0122] According to an embodiment of the present application, an embodiment of a device for implementing the above network traffic control method is also provided, Figure 13 is a schematic diagram of a network traffic control device according to an embodiment of the present application, such as Figure 13 As shown, the device includes: a receiving unit 131 , an analyzing unit 133 and a first determining unit 135 .
[0123] Wherein, the receiving unit 131 is configured to receive flow feature information reported by the firewall;
[0124] An analyzing unit 133, configured to analyze flow characteristic information and / or network behavior information determined by the flow characteristic information, and obtain an analysis result;
[0125] The first determining unit 135 is configured to determine a control instruction to be delivered to the firewall according to the analysis result, wherein the control instruction is used to control network traffic flowing through the firewall...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com