Android malicious software efficient detection method and system based on runtime data analysis, and medium
A malware and data analysis technology, applied in the field of software and information security, can solve problems such as long training time, and achieve the effect of improving accuracy, reducing training time, and strengthening relevance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
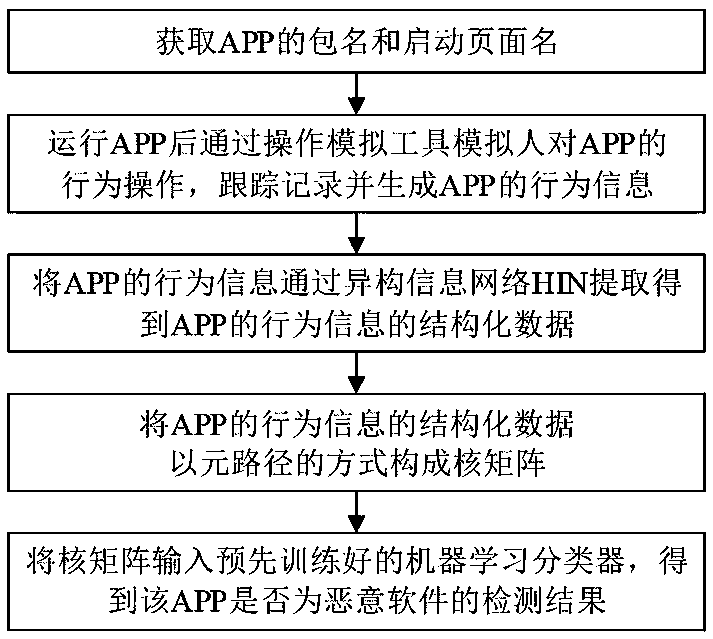
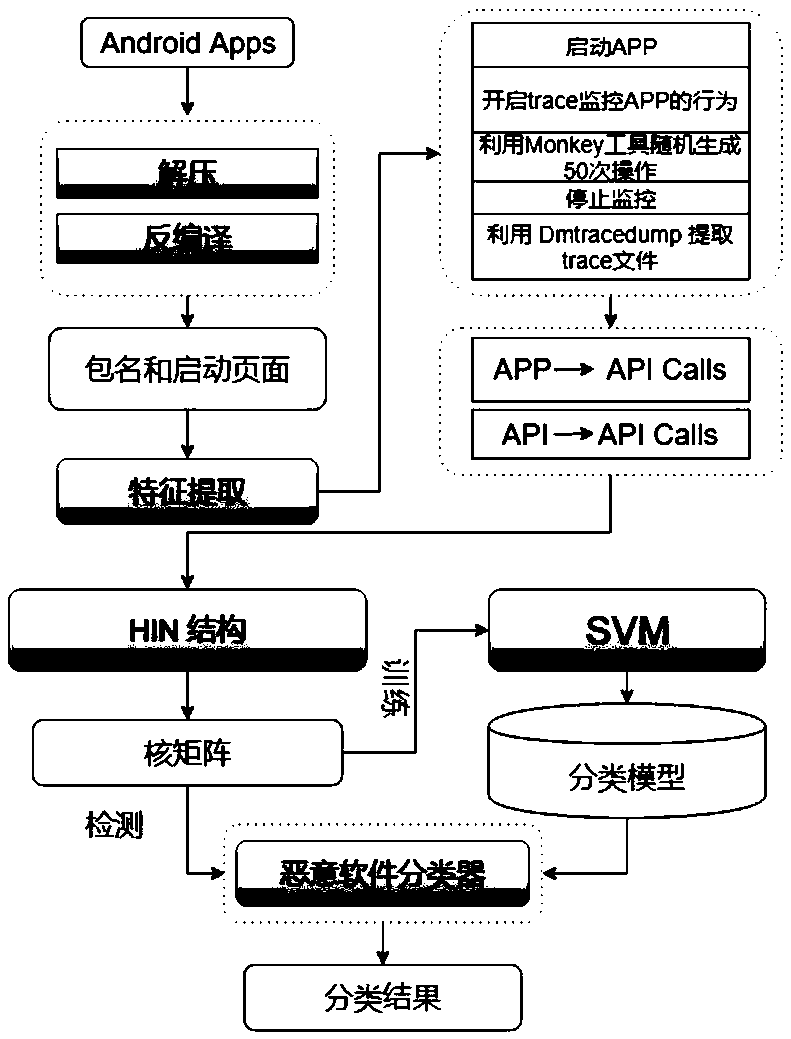
[0038] Such as figure 1 and figure 2 As shown, the implementation steps of the Android malware efficient detection method based on runtime data analysis in this embodiment include:
[0039] 1) Obtain the package name and startup page name (Activity) of APP (Android software);
[0040] 2) After running the APP based on the package name and startup page name, use the operation simulation tool to simulate the human behavior on the APP, track and record and generate the running data of the APP. The running data of the APP includes the calling of the APP to the API and the calling of the API to the API Information;
[0041] 3) Extract the operating data of the APP through the heterogeneous information network HIN to obtain the structured data of the operating data of the APP, and use the structured data of the operating data of the APP to form a kernel matrix in the form of meta paths; the heterogeneous information network HIN Including two types of nodes and two types of edges, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com