Novel RSA blind signature method
A technology of RSA algorithm and blind signature, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
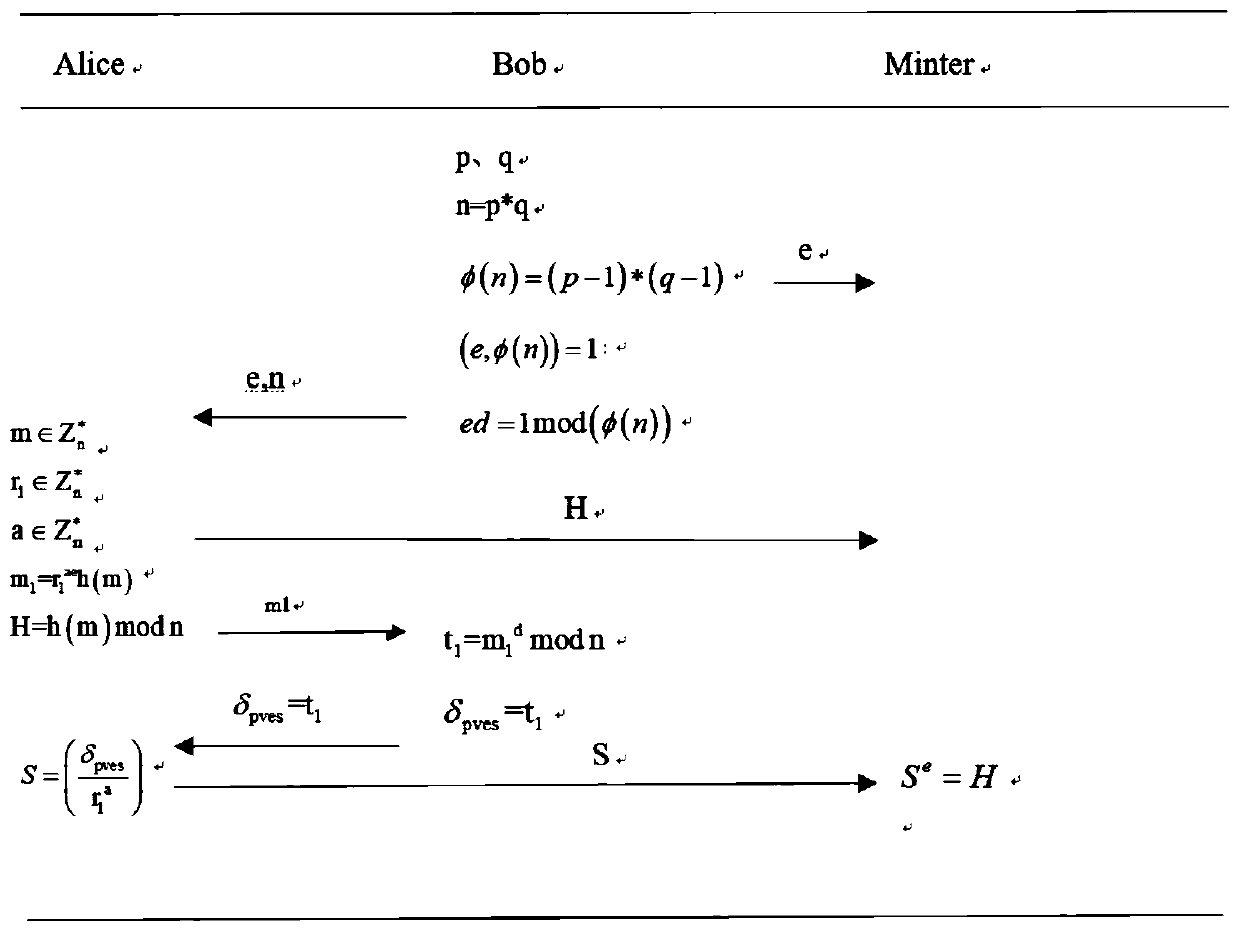
[0014] (1) The signer Bob who participates in the blind signature selects security parameters according to the RSA algorithm, calculates his public key (e, n) and private key d, and publishes a secure one-way hash algorithm at the same time
[0015] (1.1) Bob randomly selects two large prime numbers p and q, calculates n=p*q, and calculates the Euler function value φ(n)=(p-1)*(q-1) of n;
[0016] (1.2) Bob randomly selects a large integer e such that (e, φ(n)) = 1;
[0017] (1.3) According to the extended Euclidean algorithm, calculate the private key d so that it satisfies ed=1mod(φ(n)).
[0018] (2) Alice selects the information to be signed to sign:
[0019] (2.1) Alice selects the message to be signed and two different random numbers
[0020] (2.2) Alice calculates m 1 = r 1 ae h(m), blind the information m, and m 1 Send to Bob;
[0021] (2.3) Alice calculates H=h(m) modn. Public H is convenient for public verification;
[0022] (3) Bob blindly signs the mes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com