Honeypot server communication method, SSLStrip man-in-the-middle attack perception method and related devices
A communication method and attack perception technology, which is applied in the field of SSLStrip threat perception solutions, can solve the problems of affecting network access efficiency, low perception accuracy of threat perception technology, lack of universality, etc., and achieve good versatility and high perception accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
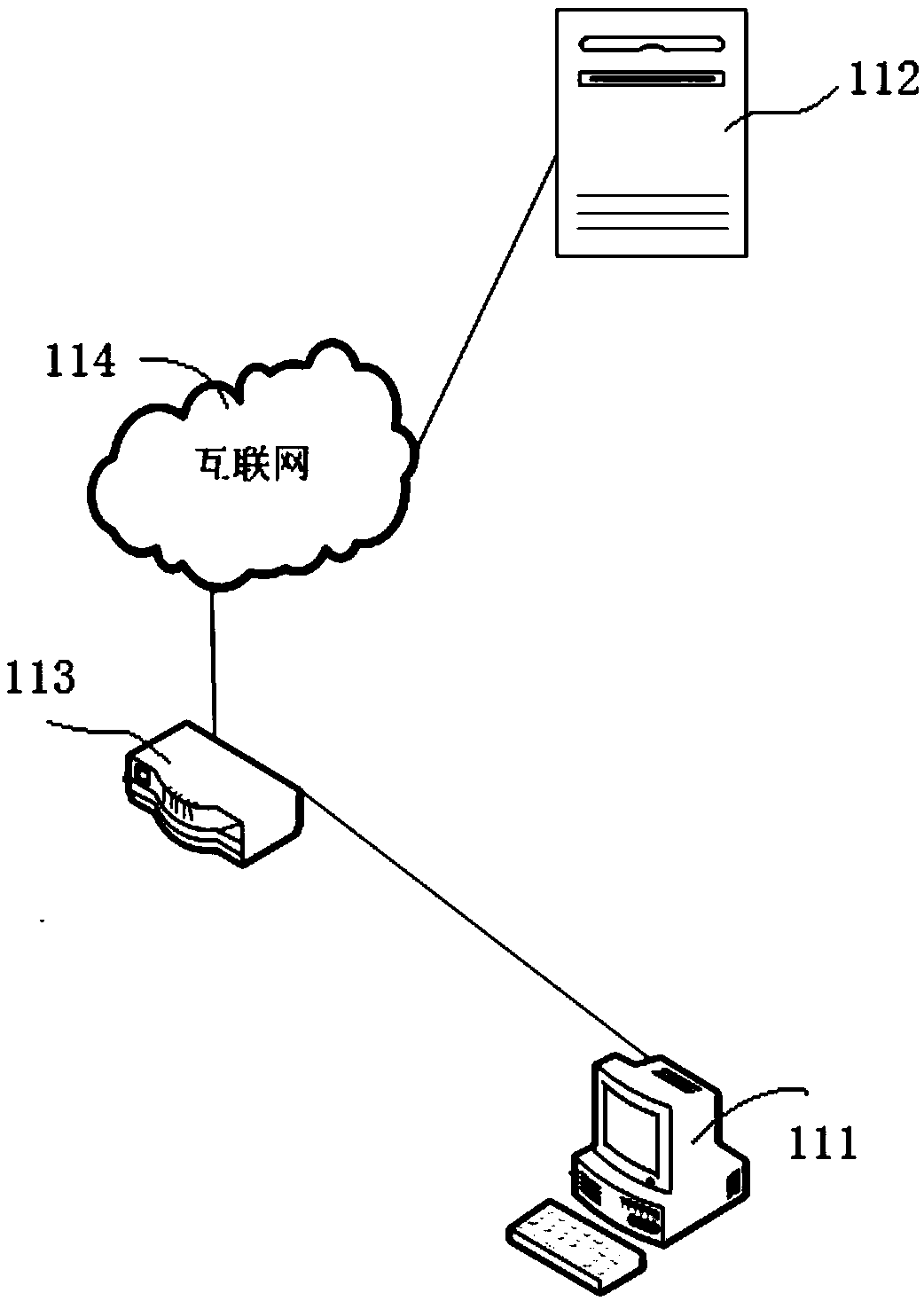
[0090] As mentioned above, when there is a man-in-the-middle attack or no man-in-the-middle attack between the ordinary terminal and the normal server with redirection deployed, after the ordinary terminal sends HTTP protocol request to the normal server with redirection deployed by HTTP protocol, the received In the received HTTP response, the status code is different, and the response header is different, including the Location field of the automatic redirection address or not including the Location field at all. Based on this principle, this embodiment deploys a honeypot server 212 in the network environment. The honeypot server 212 is a normal server that simulates the above deployment of automatic redirection. The honeypot server 212 is used to detect whether the terminal is attacked by a man-in-the-middle. Specifically, the terminal under test 211 determines whether there is a man-in-the-middle attack according to the HTTP response received after accessing the honeypot se...
Embodiment 2
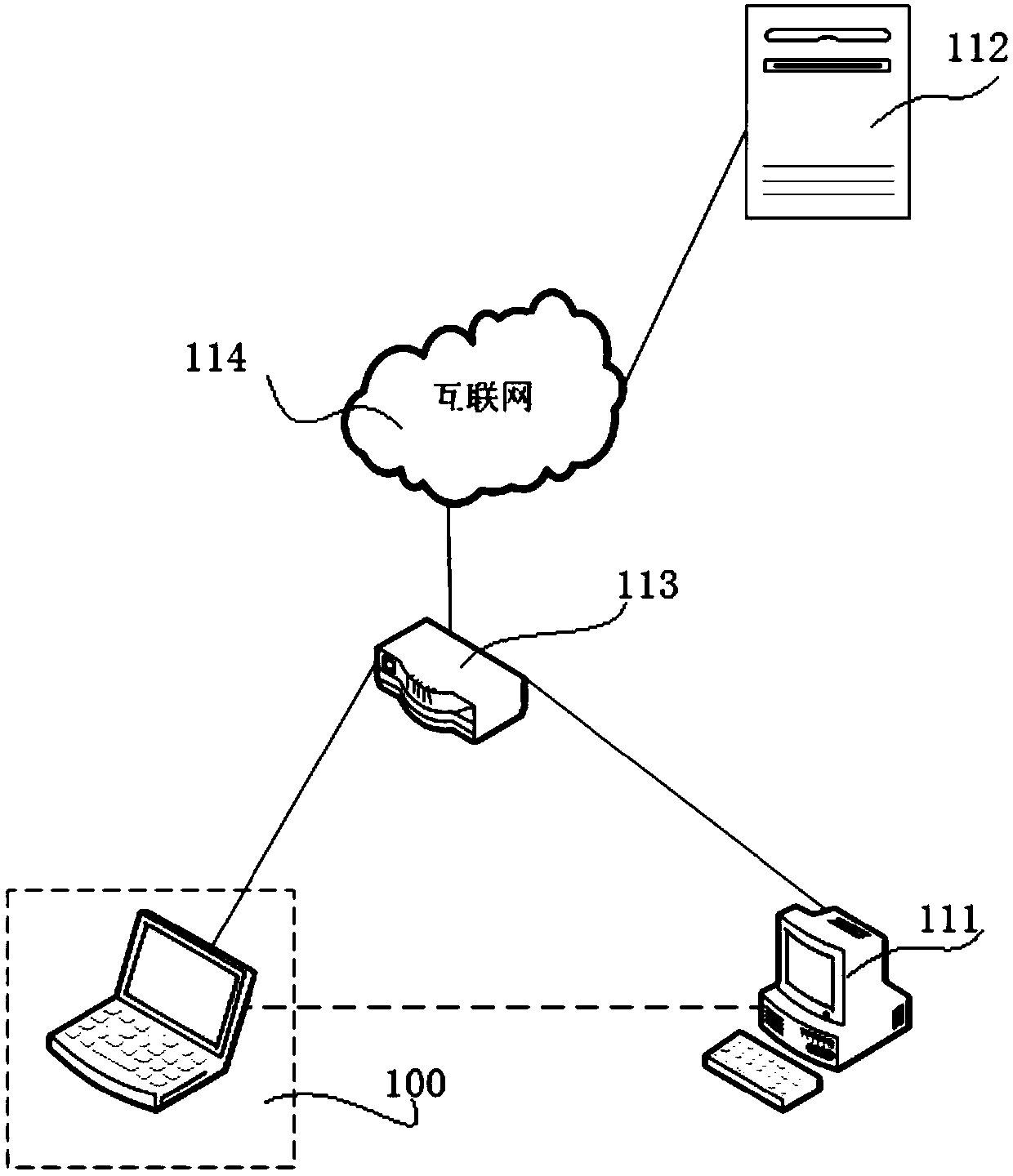
[0116] image 3 It is a flow chart of the SSLStrip man-in-the-middle attack sensing method according to Embodiment 2 of the method of the present invention. The SSLStrip man-in-the-middle attack perception method is applicable to tested terminals, which include but not limited to PC hosts, mobile tested terminals, servers, and the like. see image 3 , in this embodiment, the method includes:
[0117] Step S301, initiate an HTTP page access request to the honeypot server with the HTTP protocol, wherein the honeypot server is a normal server that is simulated and deployed with automatic redirection;
[0118] In an optional implementation of this embodiment, the HTTP page access request includes: sending source information, URL address information of the honeypot server, a destination port number for requesting page service, and a method for requesting page service. Wherein, the sending source information includes the MAC address of the terminal under test itself. The URL add...
Embodiment 3
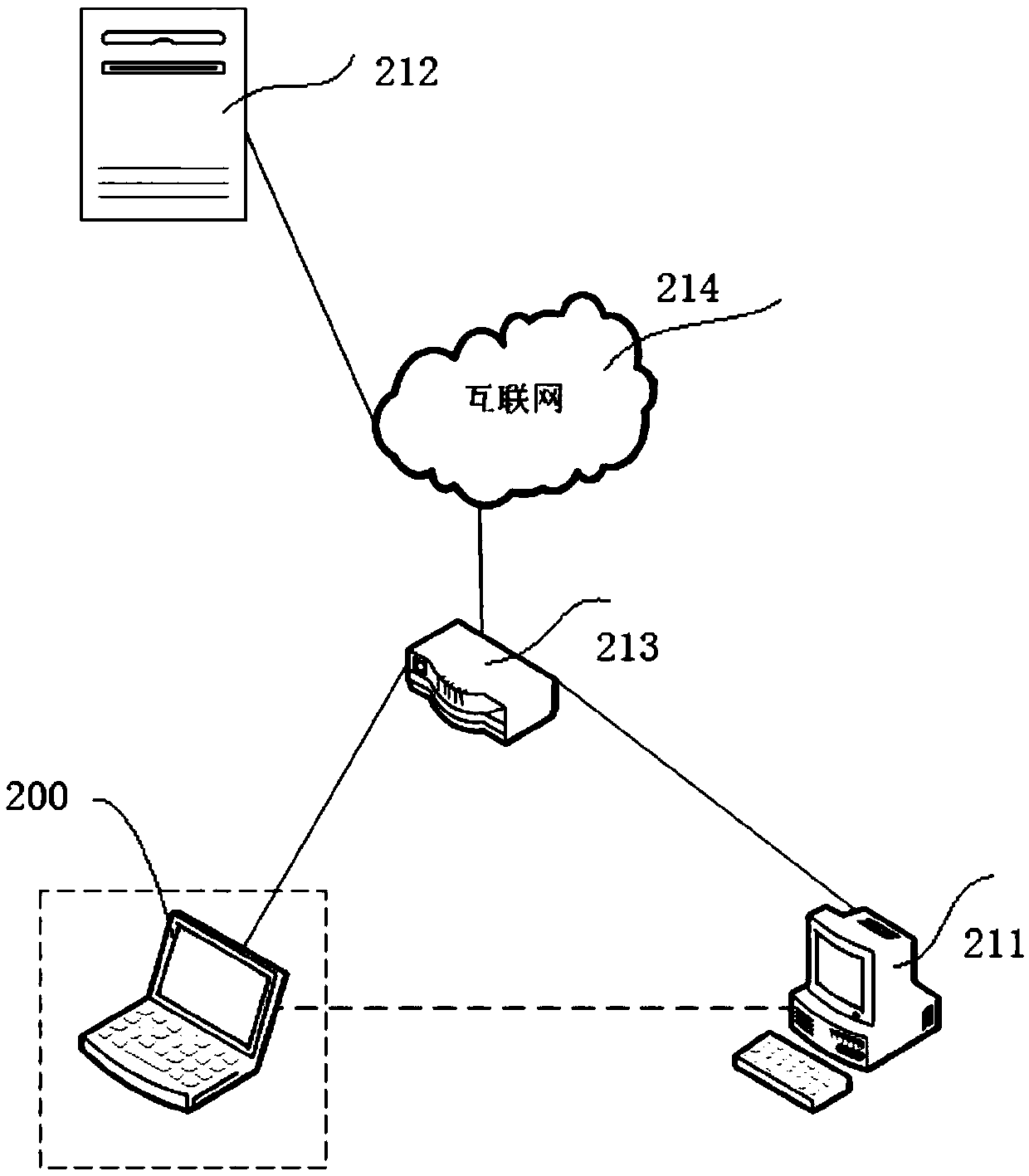
[0132] In this embodiment, the honeypot service site is configured to automatically redirect to https: / / weixin.xxx.com when accessing http: / / weixin.xxx.com as an example, to specifically describe the implementation of the SSL man-in-the-middle attack sensing method.
[0133] Firstly, the specific configuration of the honeypot service site is explained. The domain name of the honeypot service site is configured as weixin.xxx.com. When the terminal under test initiates an HTTP page access request with the URL address http: / / weixin.xxx.com, the honeypot server judges the terminal under test according to the HTTP page access request Whether to request access to the default page content configured in the root directory of the honeypot service site. Specifically, the honeypot service site judges whether the destination port number of the requested service is the default port 80 of the HTTP service, whether the method of requesting the service is the GET method, whether the URL addre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com