Data evidence storage method and device, apparatus and storage medium
A data storage and data technology, applied in the field of blockchain, can solve the problems of high cost, low storage efficiency, and inability to store large files, and achieve the effect of improving security, improving storage efficiency, and reducing storage costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
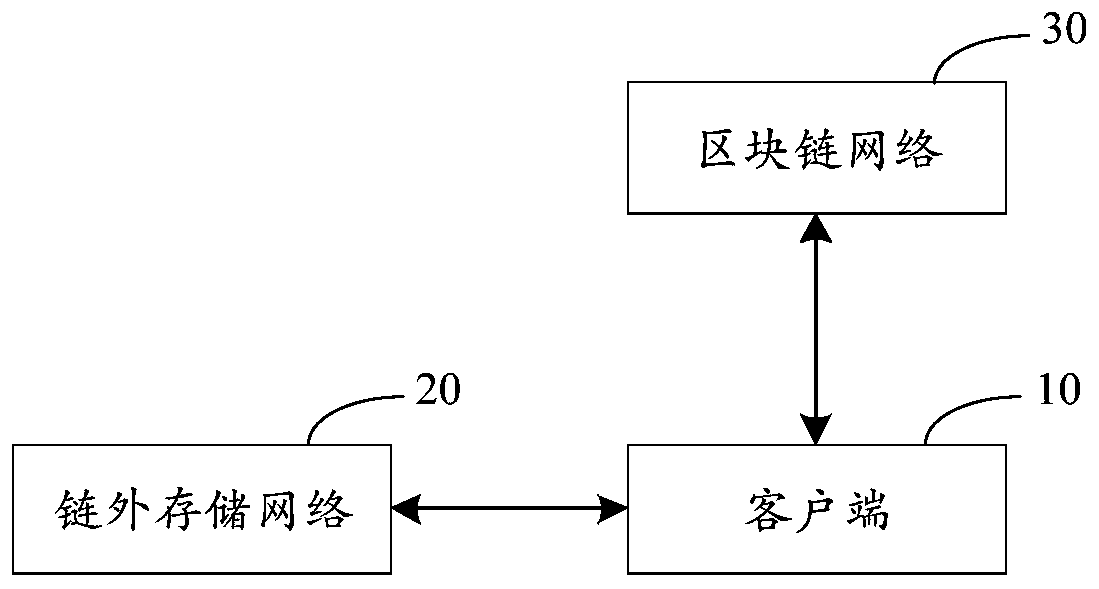
[0109] Figure 1B It is a flow chart of a data certificate storage method in Embodiment 1 of the present application, and this embodiment of the present application is applicable to the case of data storage of the data to be stored. The method is executed by a data storage device, which is realized by software and / or hardware, and is specifically configured in a client.
[0110] Such as Figure 1B A data storage method shown is applied to the client, including:
[0111] S101. When the data storage instruction triggered by the data provider is detected, the storage key is used to encrypt the data to be stored, and the encrypted data to be stored is uploaded to the off-chain storage network to obtain the off-chain storage of the data to be stored logo.
[0112] Wherein, the storage key may be a symmetric key or an asymmetric key, and is randomly generated through a key generation algorithm.
[0113] Among them, the off-chain storage network can be a cloud device that provide...
Embodiment 2
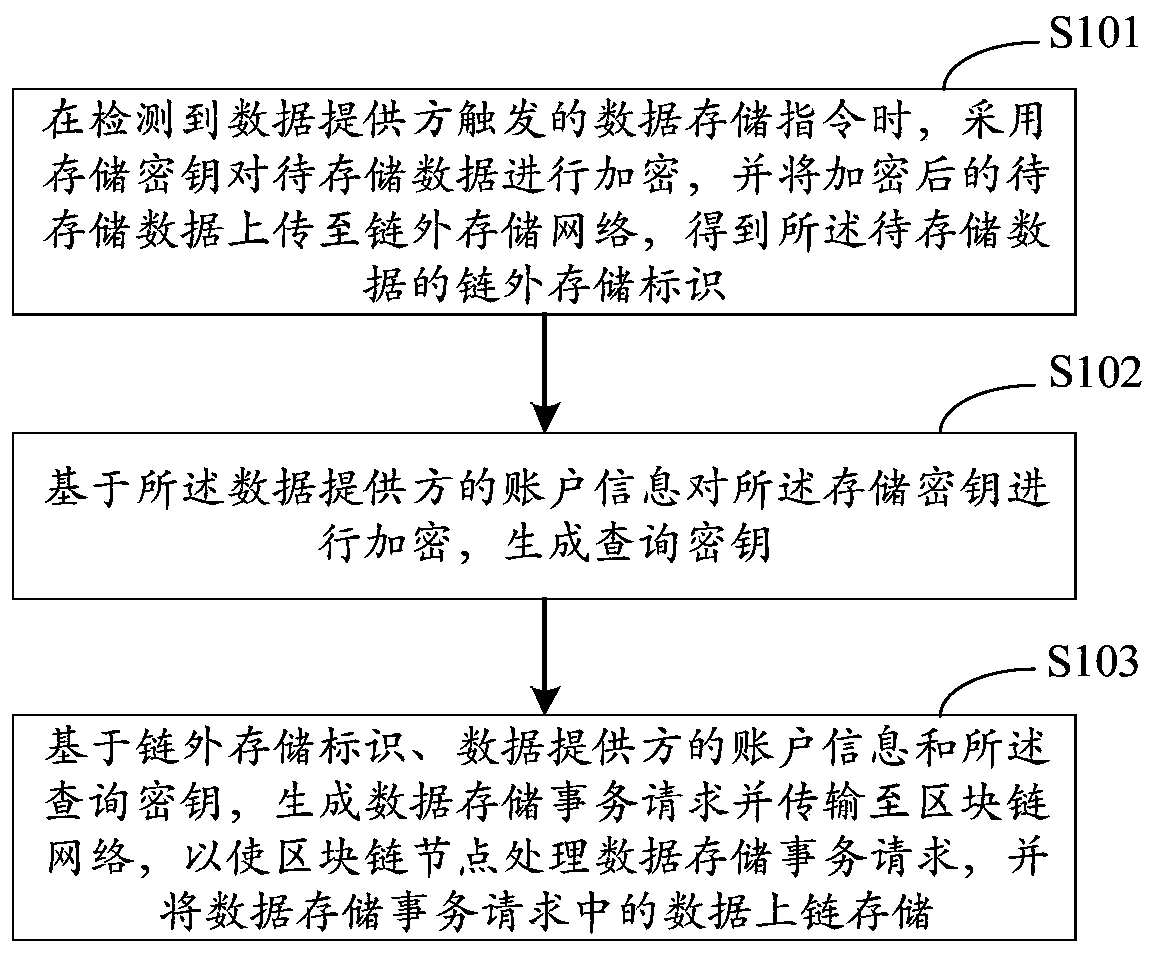
[0127] figure 2 It is a flow chart of a data storage certificate method in Embodiment 2 of the present application. The embodiment of the present application is optimized and improved on the basis of the technical solutions of the above-mentioned embodiments.
[0128] Further, the following operation is added to the data storage method: "When the request authorization instruction triggered by the authorization applicant is detected, generate an authorization application transaction based on the account information of the authorization applicant and the account information of the data provider of the data to be authorized Request and transmit to the blockchain network, so that the blockchain node processes the authorization application transaction request, and sends the authorization applicant's account information to the data provider of the data to be authorized, so as to realize the authorization application direction data Provider requests data authorization.
[0129] Suc...
Embodiment 3
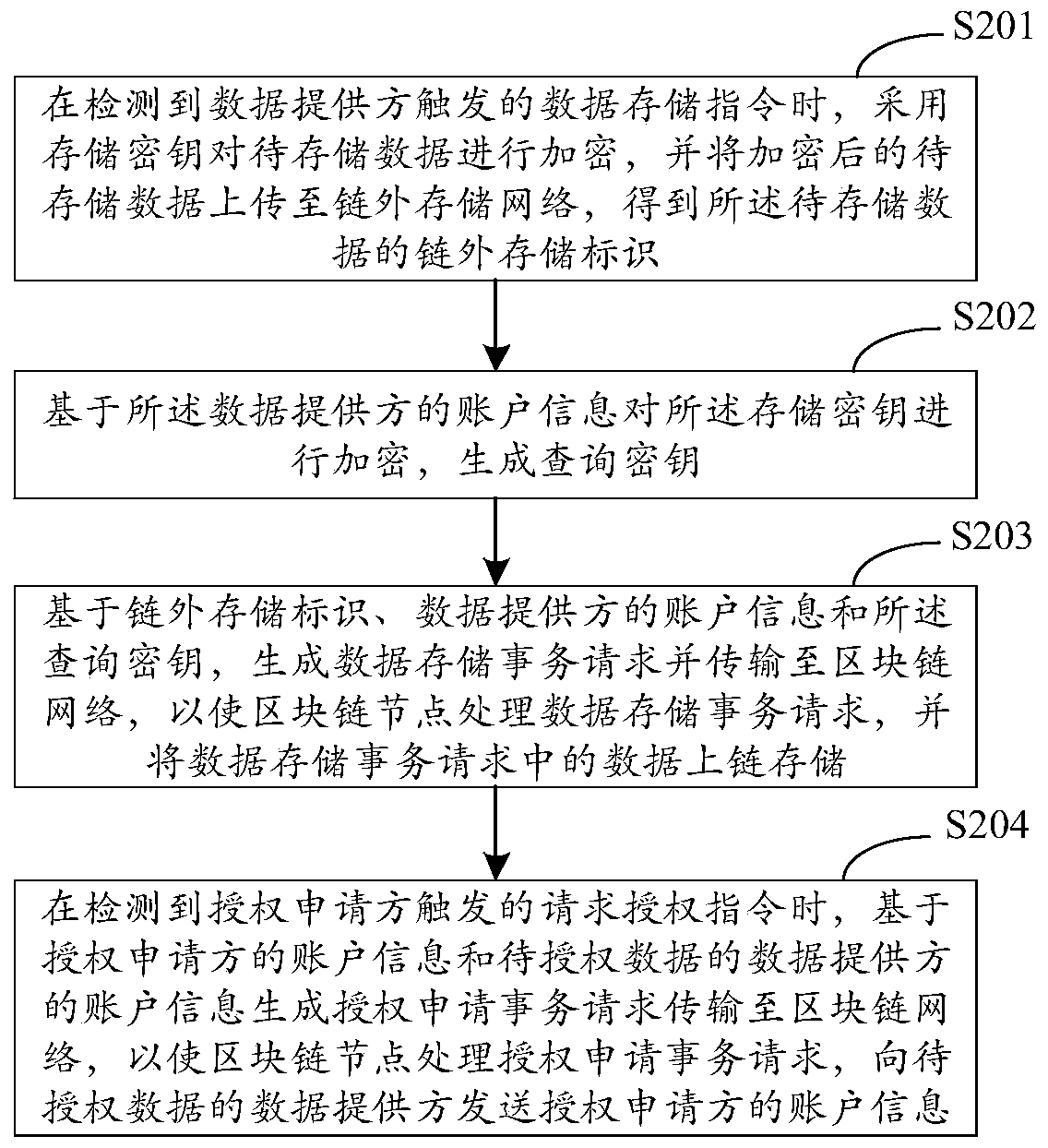
[0143] image 3 It is a flow chart of a data certificate storage method in Embodiment 3 of the present application, and this embodiment of the present application provides a preferred implementation mode on the basis of the technical solutions of the foregoing embodiments.
[0144] Further, the following steps are added to the data storage method: "When the data authorization instruction triggered by the data provider is detected, obtain the account information of the authorization applicant of the data to be authorized; generate a data authorization based on the account information of the authorization applicant. The transaction request is transmitted to the block chain network, so that the block chain node executes the data authorization transaction request, and stores the data in the data authorization transaction request and the data to be authorized in the block chain”, In order to realize that the data provider grants the authorized applicant the right to use the data to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com