Terminal safety starting method and device and storage medium
A technology for terminal security and memory management, applied in the field of terminal security startup, it can solve problems such as leakage of secret data, economic loss of users, and inability to guarantee system security, and achieve the effect of enhancing security, improving security, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
[0038]The terminals involved in the embodiments of the present application include various network devices. Network devices are physical physical devices connected to the network. Basic network devices such as: computers (whether they are personal computers or servers), hubs, switches, bridges, Routers, gateways, network interface cards (NICs), wireless access points (WAPs), printers and modems, fiber optic transceivers, fiber optic cables, and more.
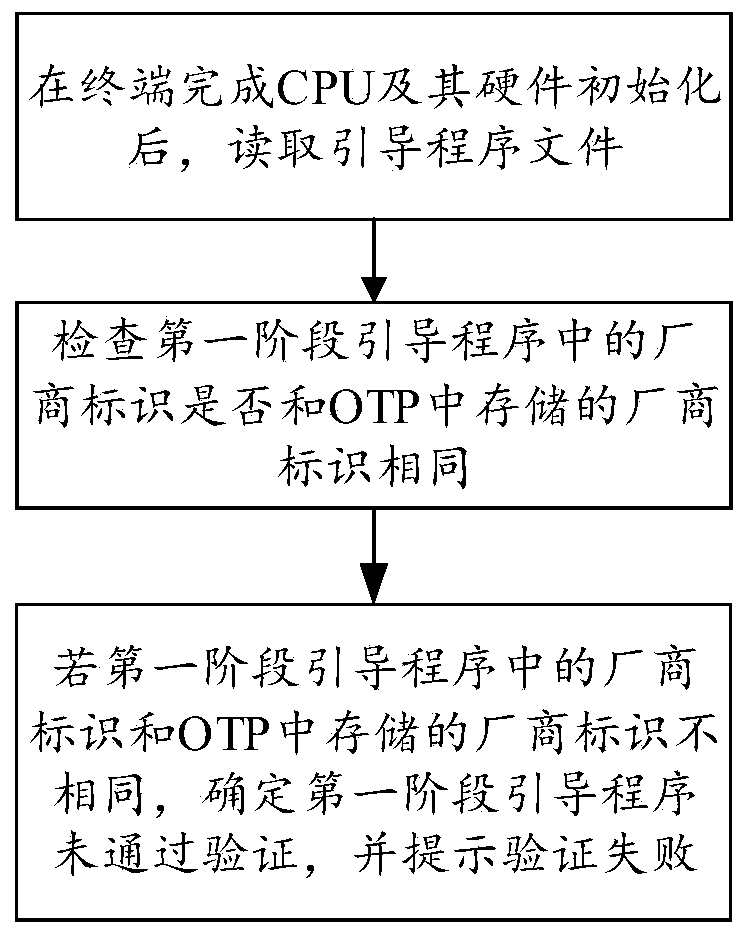
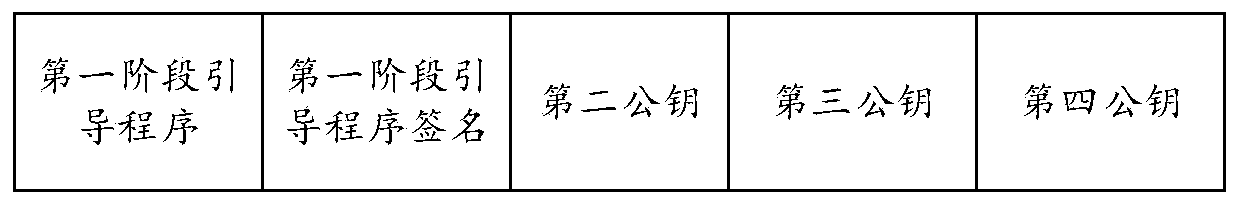
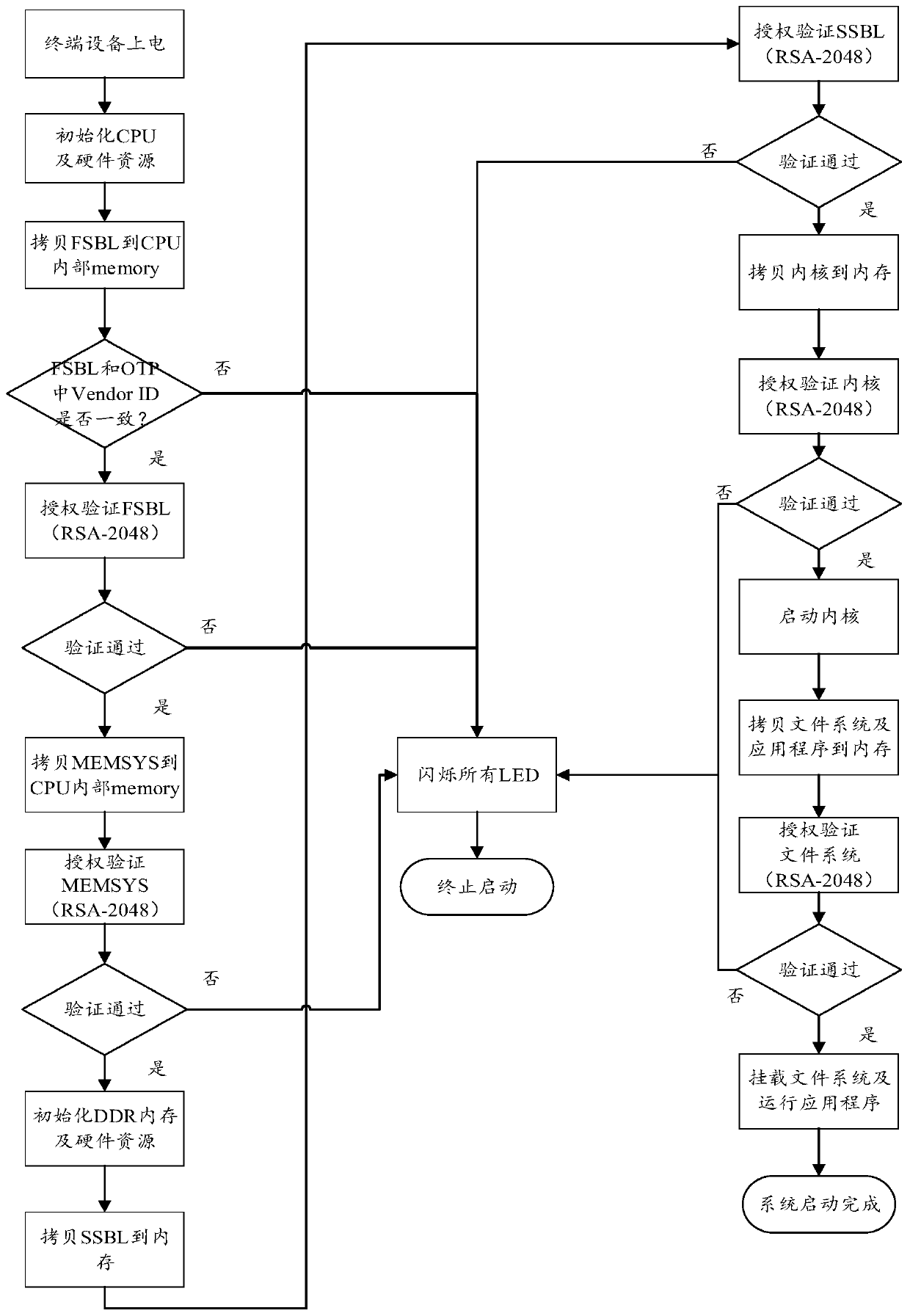
[0039] After the terminal device is powered on, that is, after the terminal switch is turned on, the power supply supplies power to the main board, and the CPU (Central Processing Unit, central processing unit) and its hardware (basic hardware) are initialized first, and the CPU and its hardware are initialized Finally, the CPU copies the stored boot ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com