Element abnormal structure detection model construction method based on complex network
A technology of abnormal structure and detection model, which is applied in the fields of instruments, finance, and data processing applications, and can solve problems such as neglect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings.
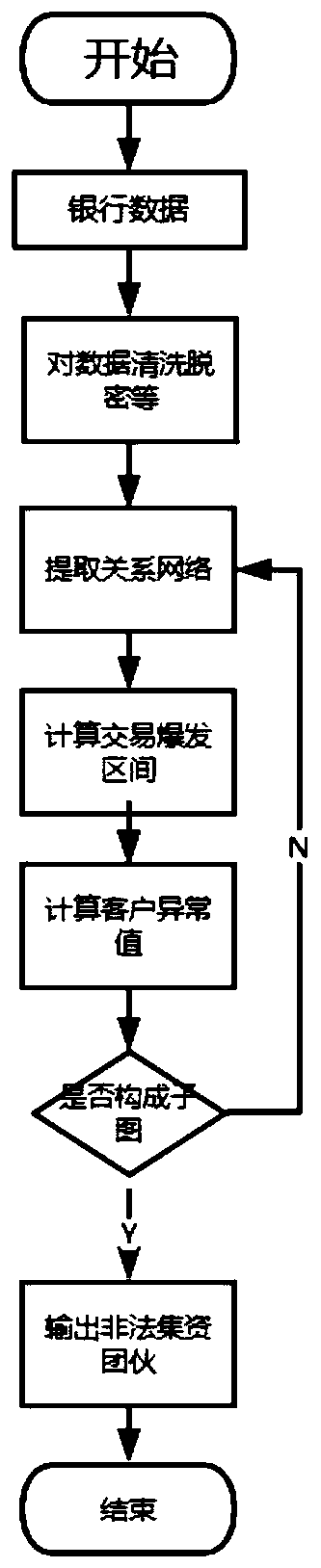
[0035] The detection method of illegal fund-raising behavior based on complex network proposed in this paper is mainly applied to discover illegal fund-raising behavior and find out its operation rules. When unearthing an illegal money syndicate, follow the steps described below.
[0036] Step 1: First, we obtain the bank's transaction data, and we mainly clean the bank's transaction flow.
[0037] Step 2: Further pre-process the data and remove redundant data. In order to protect the privacy of customers in the bank, we perform decryption processing, such as the customer's id (the card number in the bank).
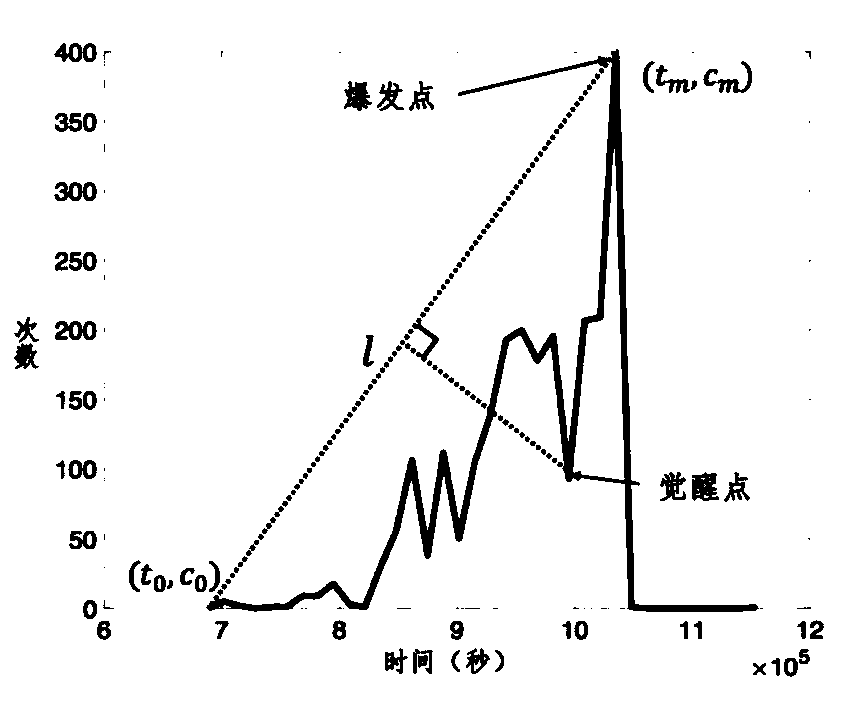
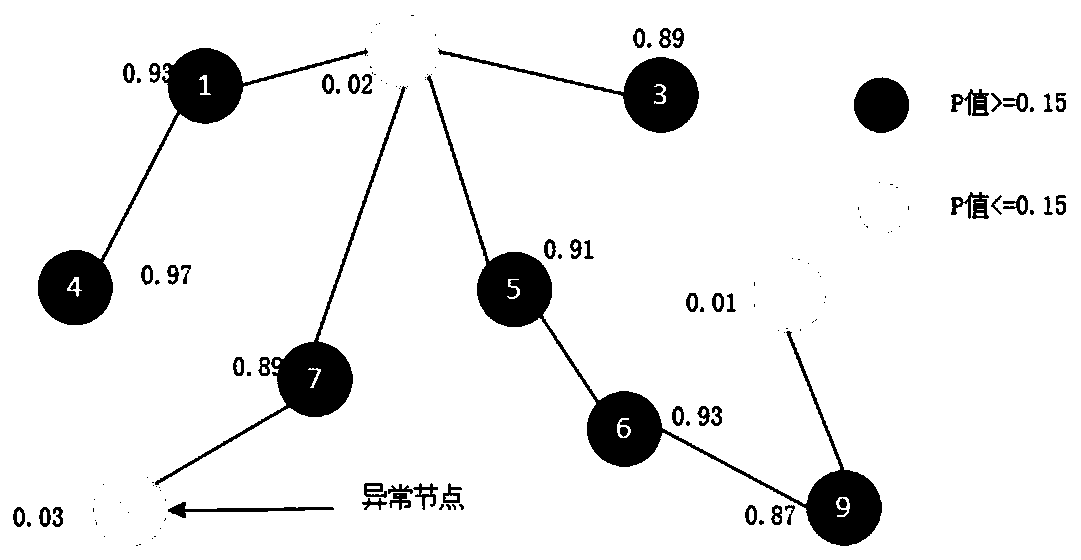
[0038] Step 3: Construct a transaction network according to the ternary relationship model. The transaction network is G=(V, E, M, T). In its meaning, nodes are transaction nodes between customers, and the attributes on the edge include transaction time and trans...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com