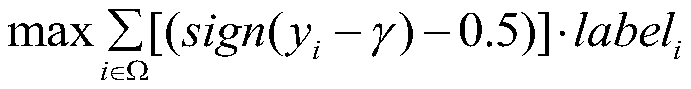Point attack method for generating adversarial sample based on weight spectrum
A technology against samples and weight spectrum, which is applied in the direction of digital data protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
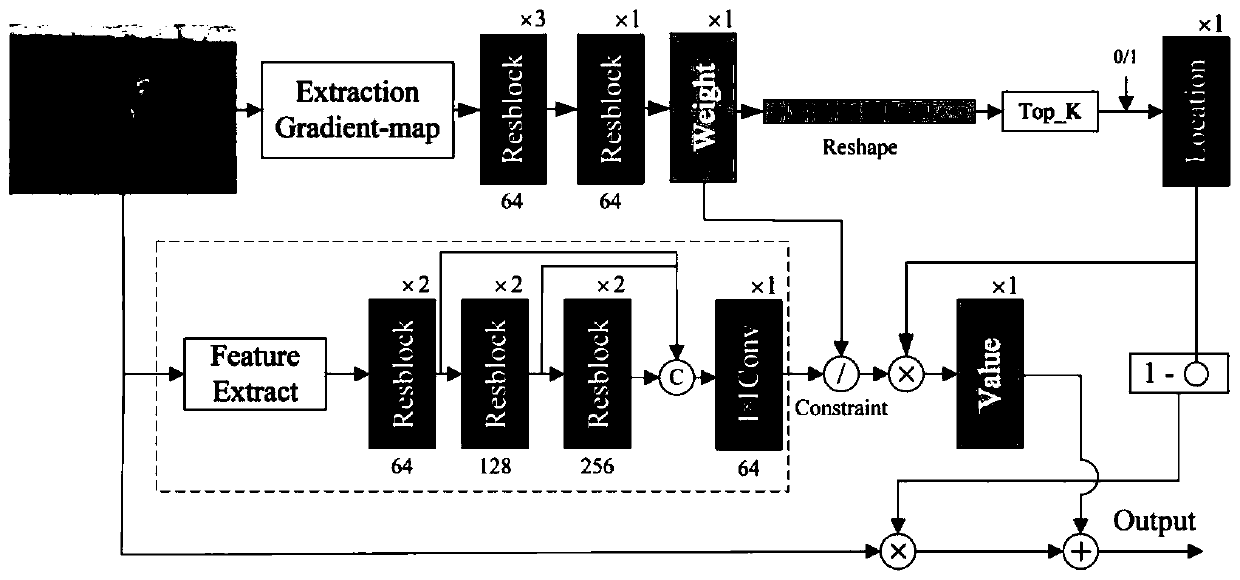
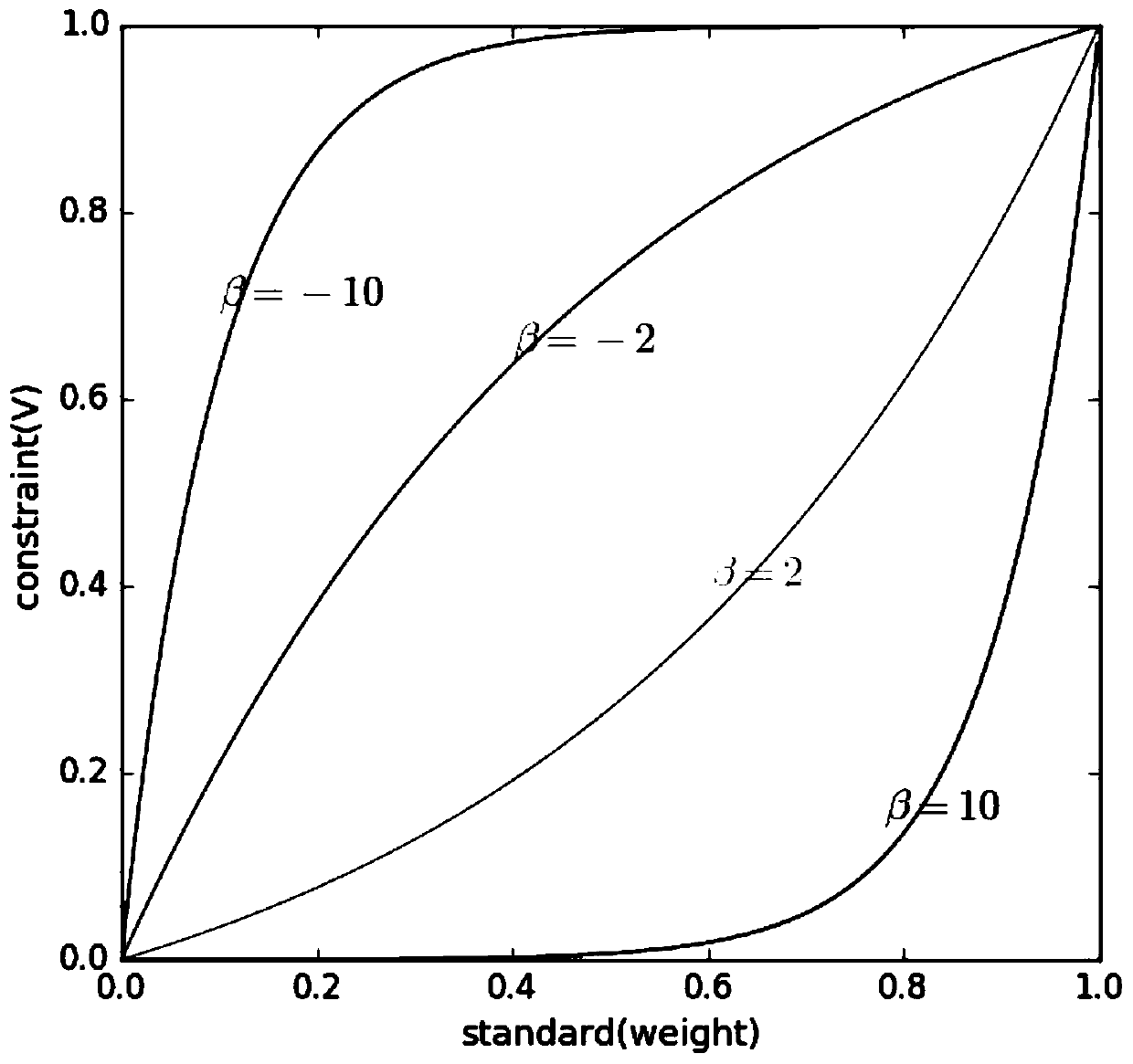
[0056] In view of the poor ability of adversarial samples to resist human eye detection and machine learning method detection, this application proposes a point attack method based on weight spectrum to generate adversarial samples. The method first calculates the weight spectrum based on the edge image generated by the edge filter from the original image, and then modifies the existing method on this basis to make it suitable for the method of point attack. Then, based on the weight spectrum, a constraint function that balances the degree of tampering and attack success rate is proposed. Finally, two methods of fixed tampering points and minimum pixel point attack are used to generate adversarial samples.
[0057] The specific plan is as follows:
[0058] Threshold-based methods for detecting singularities:
[0059] By mapping different samples to the same kernel space, Meng et al. proposed to use the maximum mean difference (MMD) to compute the distance. MMD uses statistic...
Embodiment 2
[0125] A point attack method for generating adversarial samples based on weight spectrum, the steps are as follows:
[0126] S1. Distinguishing adversarial samples containing singular points;
[0127] S2. Design a new point-based attack method to generate adversarial samples with anti-perception and anti-detection performance. The newly generated adversarial samples need to meet the following requirements: they cannot be perceived by human eyes and can be detected as normal samples by existing detection methods;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com