Visitor face recognition passing method and system based on intelligent terminal
A smart terminal and face recognition technology, applied in the field of visitor identification, can solve the problems of increasing the workload of guards and leakage of visitor identity information, and achieve the effects of saving registration time and labor costs, protecting visitor identity information, and convenient modification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
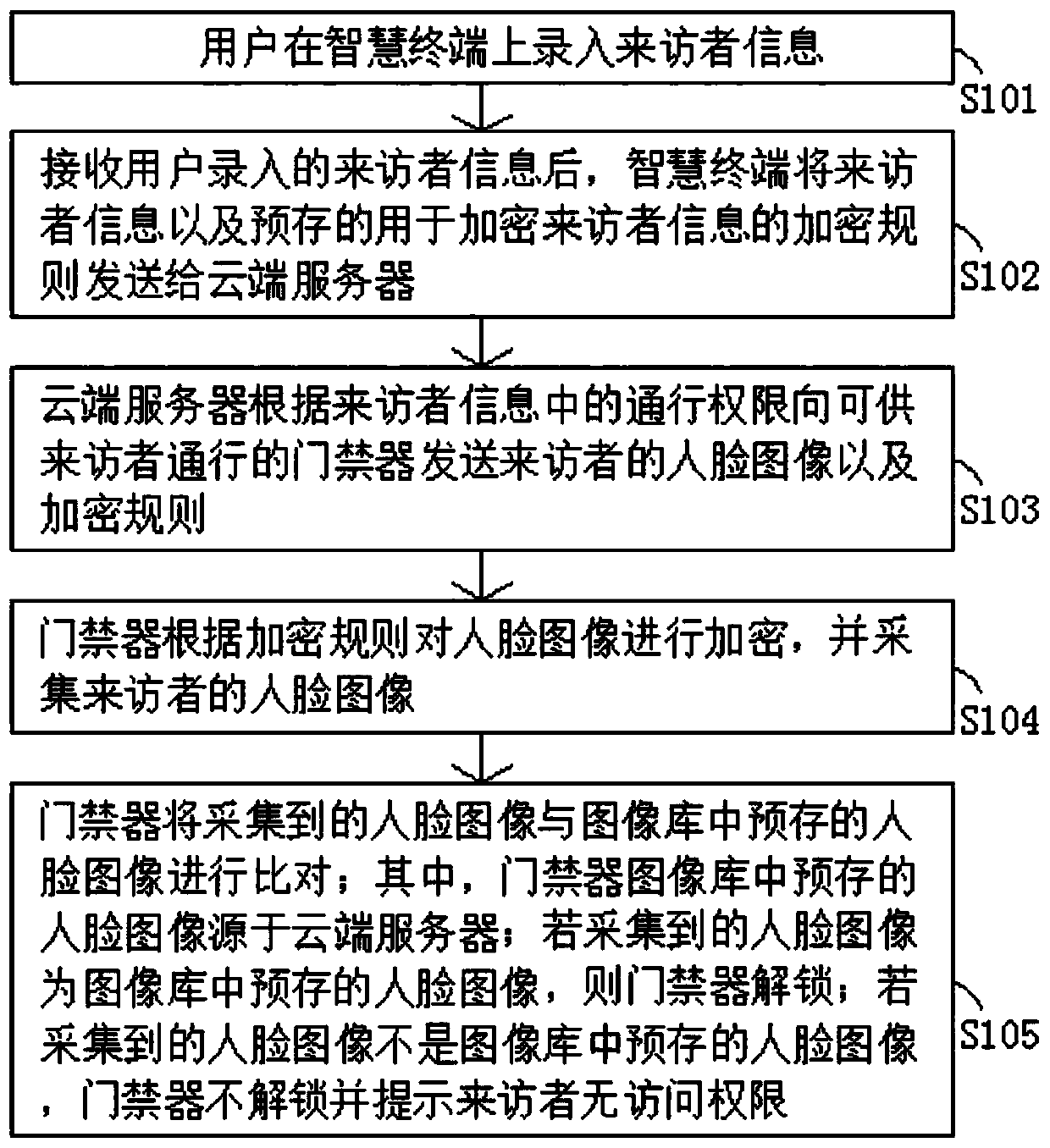
[0030] This embodiment provides a method for face recognition of visitors based on smart terminals, such as figure 1 shown, including the following steps:
[0031] Step S101: the user enters visitor information on the smart terminal; wherein, the visitor information includes the visitor's face image and the visitor's access authority.
[0032] In this embodiment, the smart terminal is preferably a mobile phone or a tablet computer.
[0033] In this embodiment, the face image is used as the primary visitor information, and the visitor does not need to be in contact with the recognizer during subsequent identification, so the leakage of biological information is less and the security is better.
[0034] In this embodiment, the passage authority mainly includes two parts: one is the passable area, and the other is the passable time period. Among them, the passable area mainly considers that different office personnel in each unit will work in different office areas. By setting ...
Embodiment 2
[0048] This embodiment provides a smart terminal-based visitor face recognition pass method, including the following steps:
[0049] Step S201: The user enters the visitor's information and number strings on the smart terminal; wherein, the visitor's information includes the visitor's face image and the visitor's access authority.
[0050] Step S202: After receiving the visitor information entered by the user, the smart terminal sends the visitor information and the pre-stored encryption rules for encrypting the visitor information to the cloud server;
[0051] In this embodiment, the encryption rule is that the number from the first digit of the number string to the last digit of the number string are multiplied sequentially, and the final result obtained is used as the unlocking password corresponding to the visitor information, so that the initial input password and the final decryption The passwords are not the same. Even if others peep when entering the number string, it ...
example 1
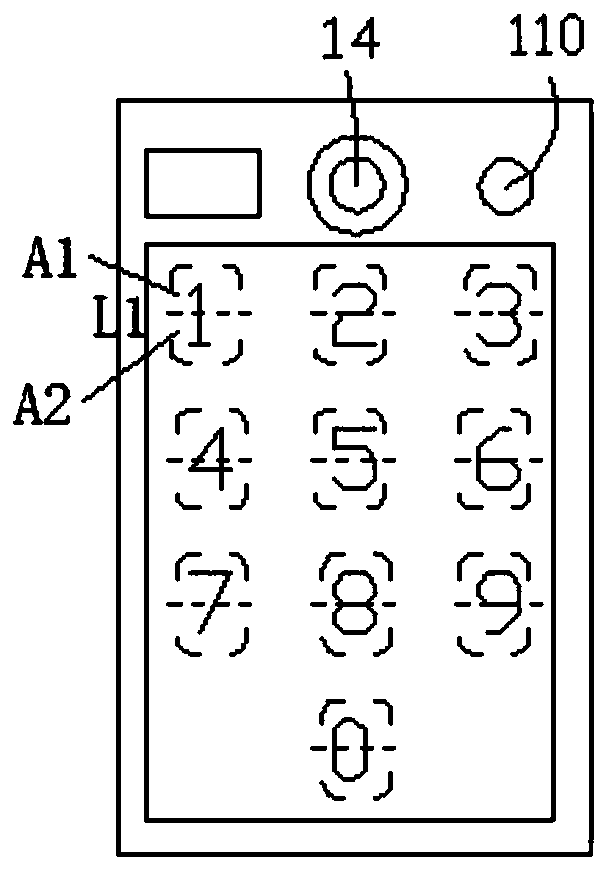
[0062] The division of the touch area of each touch number key on the access control device is as follows: figure 2 As shown, wherein, the horizontal line L1 divides the number key touch area into two equal parts to obtain sub-area A1 and sub-area A2, all sub-areas A1 are cooling areas, and all sub-areas A2 are normal temperature areas;
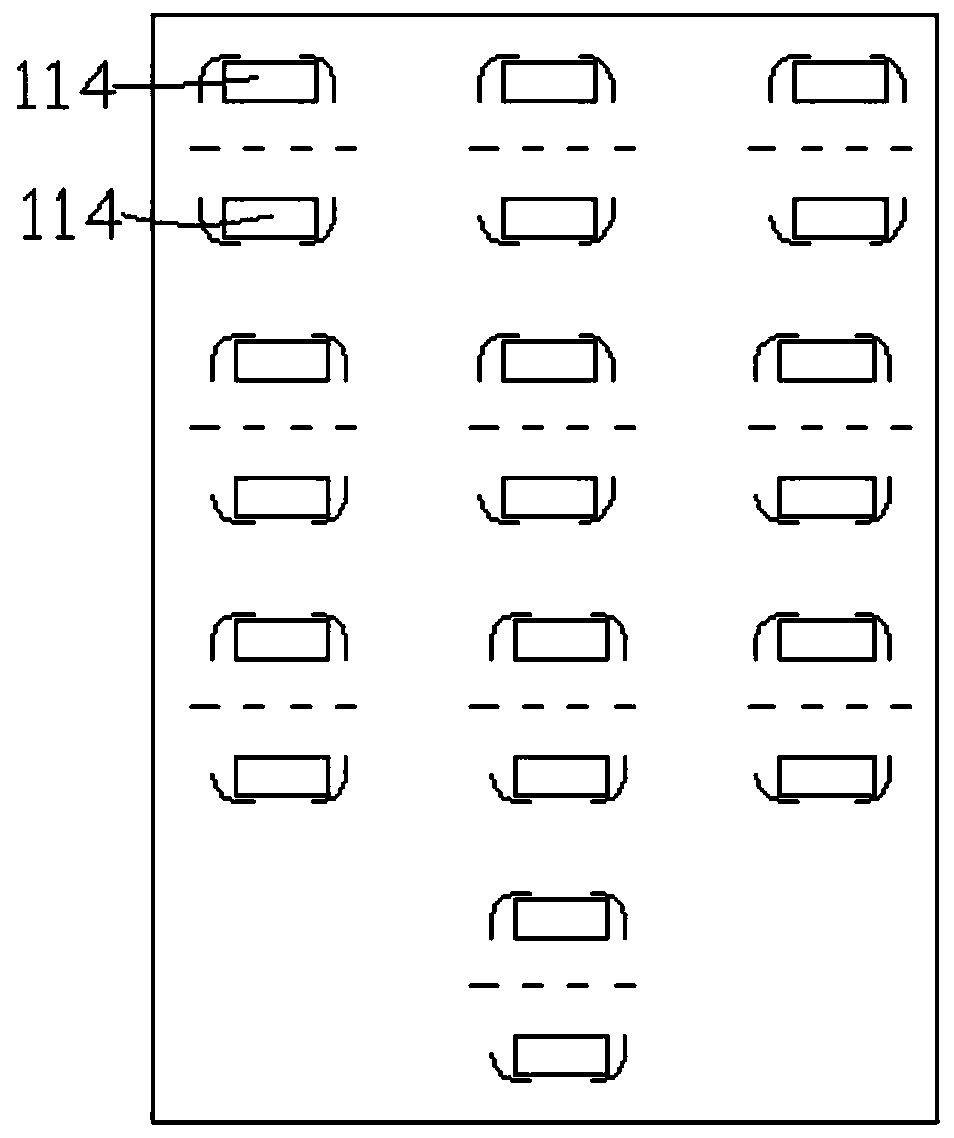
[0063] The semiconductor refrigeration sheet is adopted to cool down, and the distribution of the semiconductor refrigeration sheet 114 is as follows: image 3 shown;
[0064] The numbers corresponding to the sub-areas of each touch number key are as follows: Figure 4 shown;
[0065] The preset threshold is 2S;
[0066] The number string entered by the user is 1234, and the final decryption password is 1*2*3*4=24;
[0067] The collected data are:
[0068] The user's fingertip stays in the sub-area A2 of the number key 3 for 1 second, and stays in the sub-area A1 of the number key 3 for 2.2 seconds, then the number to be input is 2; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com