Control method, device and equipment and storage medium
A task and temporary technology, applied in the direction of instruments, data processing applications, office automation, etc., can solve the problems of cumbersome application process, suspect escape, low efficiency, etc., and achieve the effect of improving deployment control efficiency and rapid deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
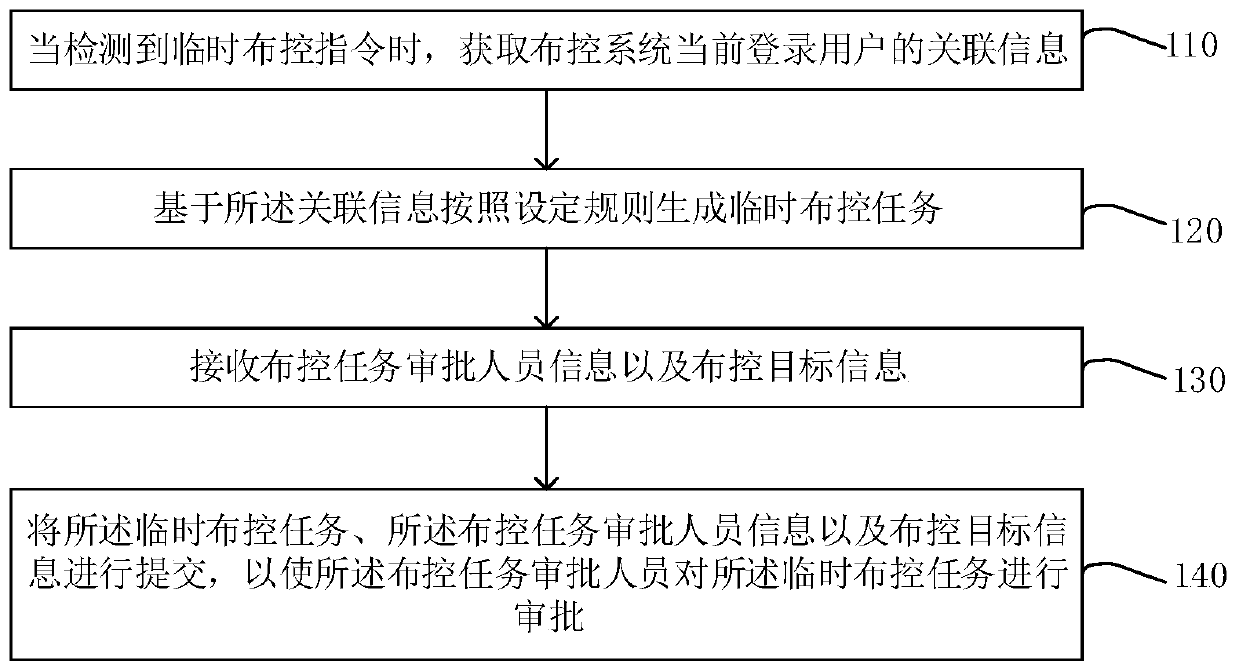
[0032] figure 1 It is a flow chart of a deployment and control method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of temporary deployment and control by the public security department. The method may be executed by a control device, which may be implemented by software and / or hardware, and which may be configured on an electronic device such as a computer. Such as figure 1 As shown, the method specifically includes the following steps:
[0033] S110. When a temporary deployment and control instruction is detected, obtain associated information of a currently logged-in user of the deployment and control system.
[0034] Exemplarily, the temporary arming instruction may be an instruction corresponding to the function of the module generated by triggering a certain module. For example, refer to figure 2 The page diagram of a control system is shown, taking setting a temporary control task as an example, when it is necessa...
Embodiment 2
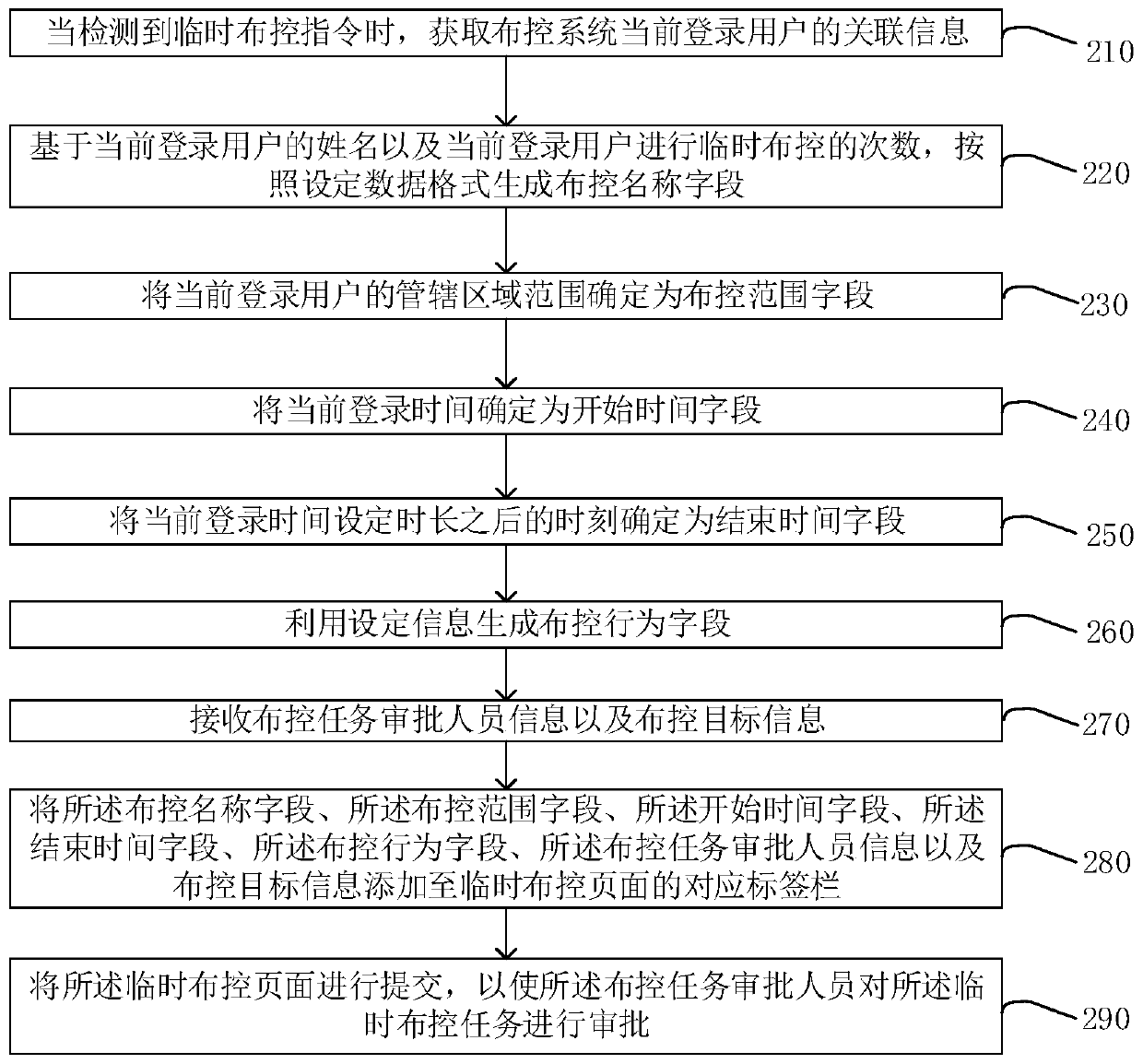
[0049] image 3 It is a flow chart of a deployment and control method provided by Embodiment 2 of the present invention. Embodiment 2 of the present invention is based on the above-mentioned embodiment and further refines the above-mentioned embodiment, as shown in image 3 As shown, the method specifically includes the following steps:
[0050] S210. When a temporary deployment and control instruction is detected, obtain associated information of a currently logged-in user of the deployment and control system.
[0051] S220. Based on the name of the currently logged-in user and the number of times the current logged-in user performs temporary deployment, generate a deployment name field according to a set data format.
[0052] The format of the set data can be in the form of "name + police officer's temporary deployment + number of times". refer to Figure 4 A schematic diagram of a temporary deployment page is shown, in which the deployment name field is "Officer Zhang Sa...
Embodiment 3
[0071] Figure 5 The flow chart of a deployment and control method provided by the third embodiment of the present invention, the third embodiment of the present invention is based on the above-mentioned embodiment, and further refines the above-mentioned embodiment, as shown in Figure 5 As shown, the method specifically includes the following steps:
[0072] S310. When a temporary deployment instruction is detected, obtain associated information of a currently logged-in user of the deployment and control system.
[0073] S311. Based on the name of the currently logged-in user and the number of times the current logged-in user performs temporary deployment, generate a deployment name field according to the set data format.
[0074] S312. Determine the jurisdictional area of the currently logged-in user as the deployment and control range field.
[0075] S313. Determine the current login time as the start time field.
[0076] S314. Determine the time after the set duratio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com