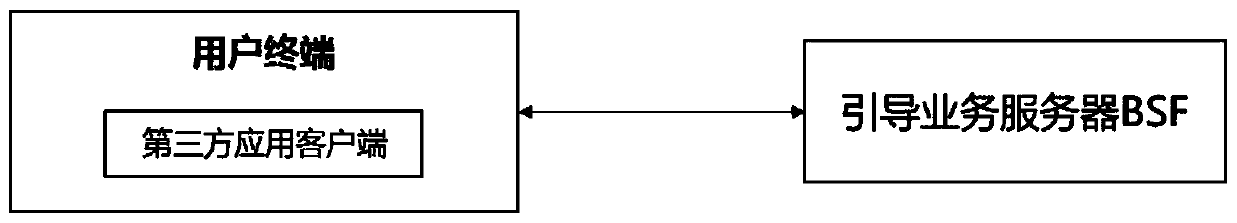
Client registration and key sharing method, device and system based on GBA
A key sharing and client-side technology, applied in the field of communication, can solve problems such as counterfeit computing and storage resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
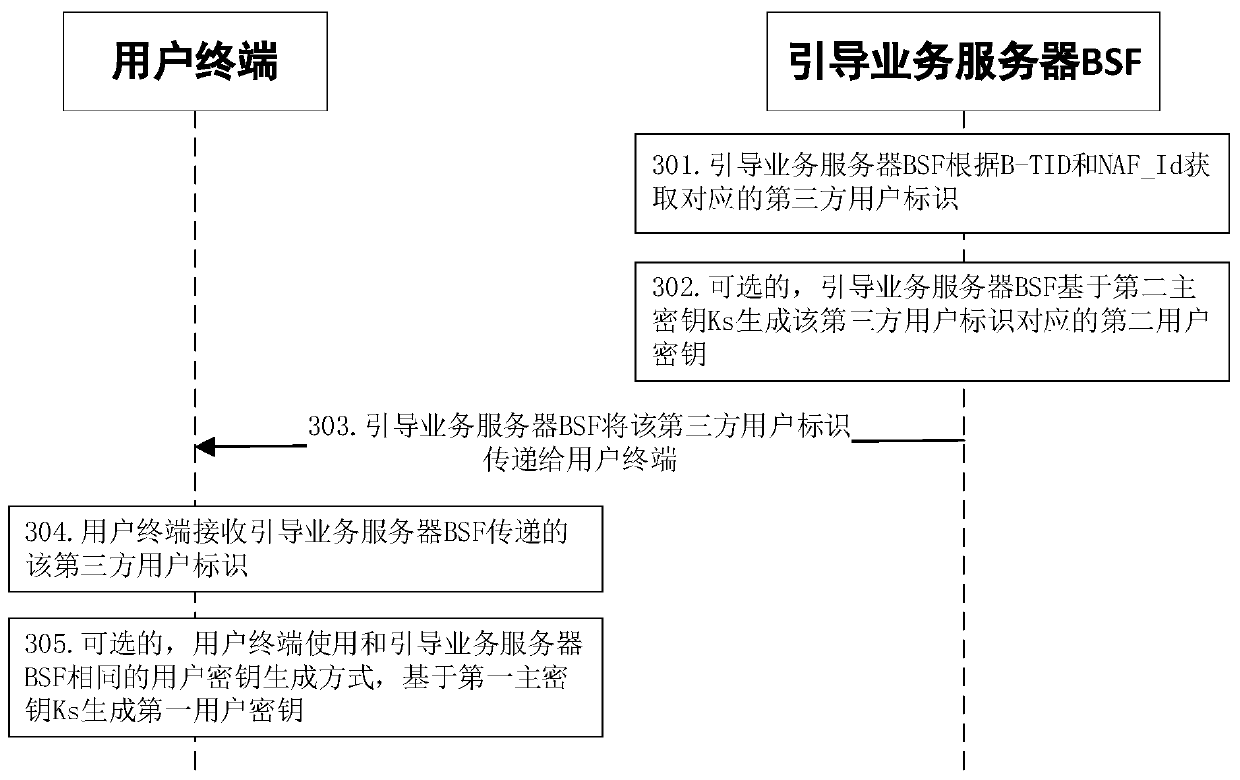
[0284] Specifically, the user terminal transfers the NAF_Id to the guidance service server BSF may include various implementation manners, for example may include:
[0285] In the first implementation manner, during the security authentication process of the user terminal to the guidance service server BSF, the user terminal transmits the NAF_Id to the guidance service server BSF.
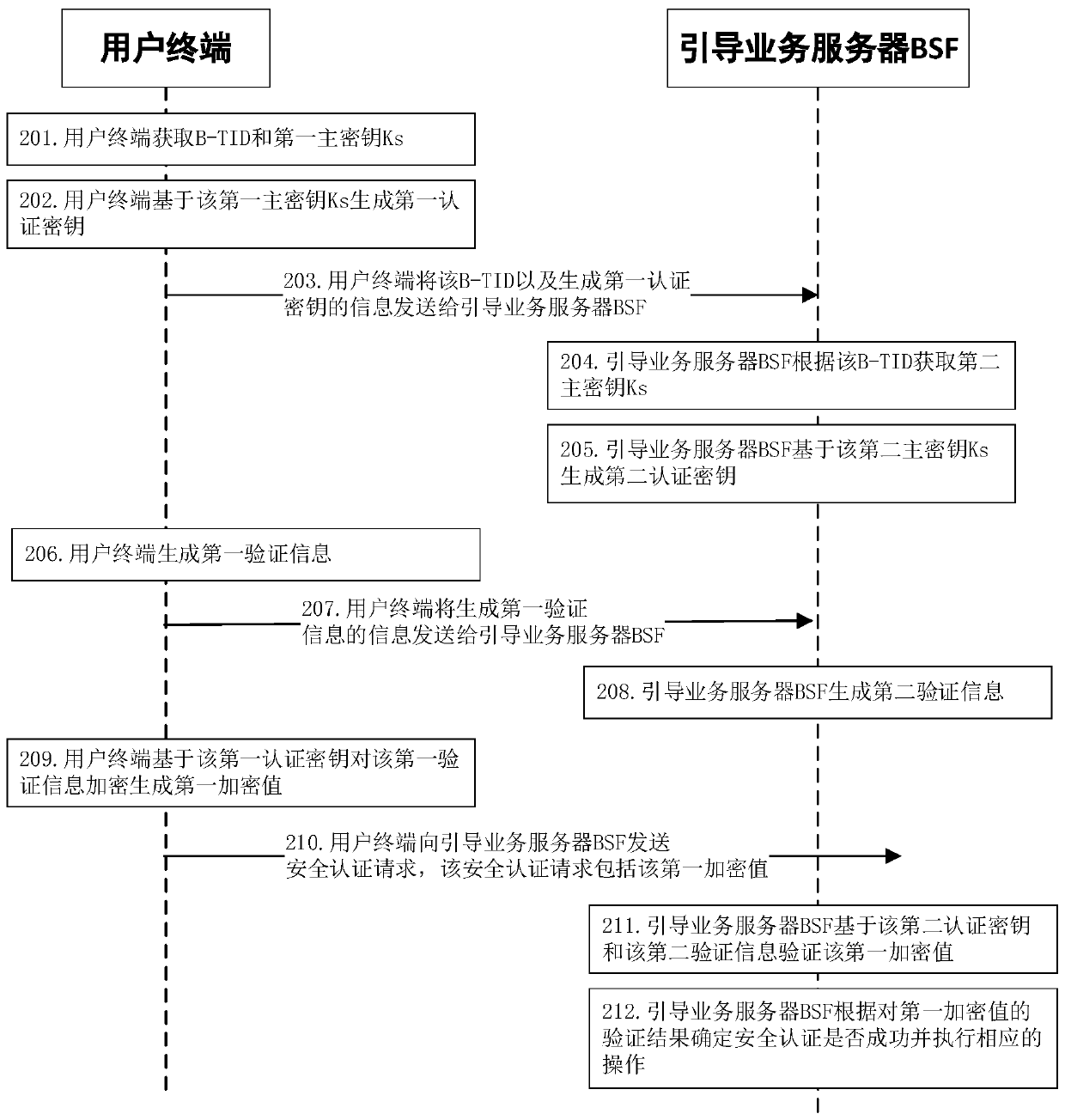
[0286] The user terminal transmits the NAF_Id to the guidance service server BSF, and may send the NAF_Id to the guidance service server BSF in a separate sending request, or send the NAF_Id to the guidance service server BSF in combination with other sending requests. For example, taking Embodiment 1 of the above-mentioned GBA-based client registration and key sharing method as an example, it may be incorporated into the security authentication request in step 210 above, or the B- TID and the information of generating the first authentication key, or / and in the step of sending the information of g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com