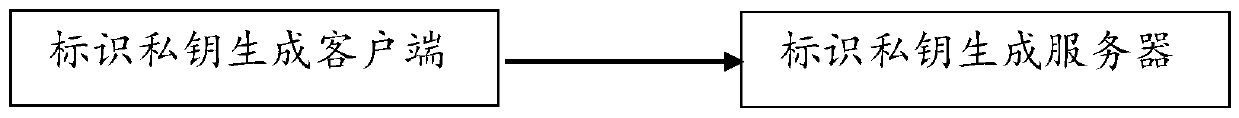SM9 signature private key generation and digital signature method, system and device
A private key and generating element technology, applied in the field of cryptography, can solve the problems that digital signatures cannot achieve non-repudiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] Embodiment 1 relates to the implementation of the SM9 signature private key generation method, digital signature method and signature verification method of the present invention.
[0079] The implementation of the SM9 signature private key generation method involves a bilinear mapping (pairing operation) e:G 1 ×G 2 →G T ;Group G 1 The generator of is P 1 , group G 2 The generator of is P 2 ;Group G 1 , G 2 , G T The order of is a prime number n;
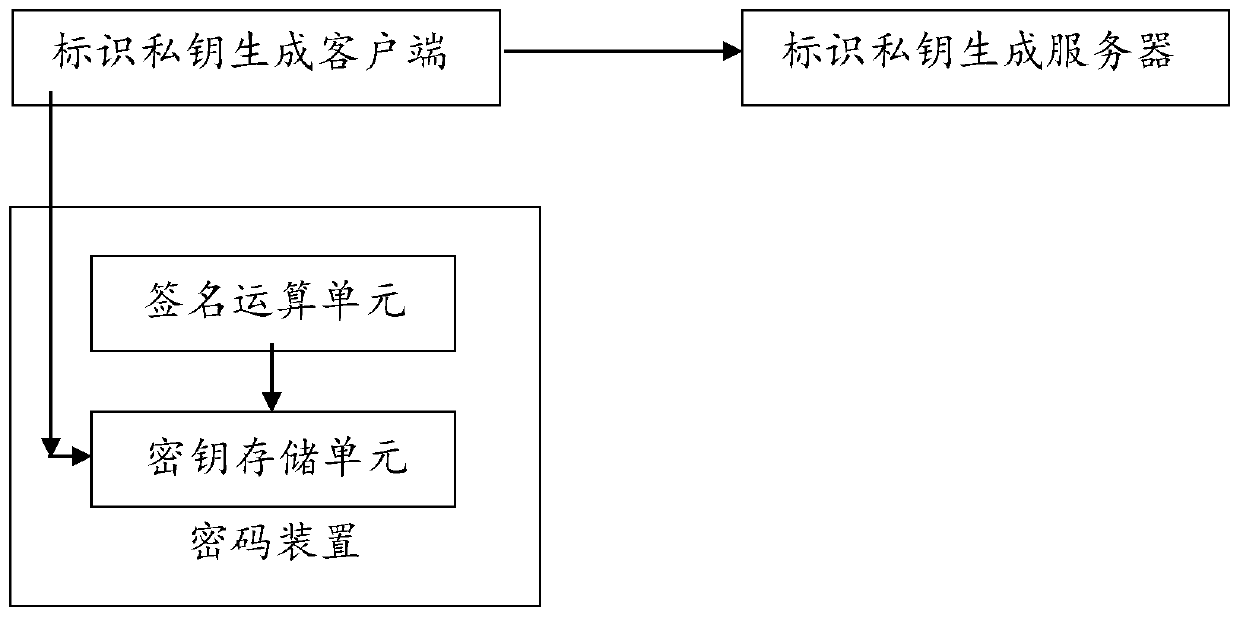
[0080] The implementation involves the identification private key generation server (Private Key Generation Server) of the server and the identification private key generation client (Private Key Generation Client) of the user end;
[0081] The identification private key generation server has the system master key s in [1,n-1] m (or system master private key s m ); m There is a corresponding system master public key P pub =[s m ]P 2 , with the corresponding system auxiliary public key P Fpub =[s m ]P 1 ;
...
Embodiment 2
[0122] The difference between this embodiment and embodiment 1 is:
[0123] The identity private key generation client does not randomly select an integer in [1,n-1] as the user master key s U (or user master private key s U ), do not calculate G 1 element P in U1 =[s U ]P 1 , do not calculate G 2 element P in U2f =[(s U ) -1 ]P 2 , where (s U ) -1 is s U The modulo n multiplicative inverse of ;
[0124] The SM9 identification private key d corresponding to the user identification used for signing is generated collaboratively A and P U2 , the server’s identity private key generation server randomly selects an integer s in [1,n-1] U0 , the client’s identity private key generation client randomly selects an integer s in [1,n-1] U1 ;
[0125] The identity private key generation client and the identity private key generation server use s=(s m +s U0 +s U1 ) mod n as the master key (master private key), without revealing their respective secrets, through interact...
Embodiment 3
[0136] The difference between this embodiment and embodiment 1 is:
[0137] The identity private key generation client does not randomly select an integer in [1,n-1] as the user master key s U (or user master private key s U ), do not calculate G 1 element P in U1 =[s U ]P 1 , do not calculate G 2 element P in U2f =[(s U ) -1 ]P 2 , where (s U ) -1 is s U The modulo n multiplicative inverse of ;
[0138] In collaboratively generating the identity private key d corresponding to the user identity A and P U2 , the server’s identity private key generation server randomly selects an integer s in [1,n-1] U0 , the client’s identity private key generation client randomly selects an integer s in [1,n-1] U1 ;
[0139] The identity private key generation client and the identity private key generation server use s=(s m +s U0 the s U1 ) modn is the master key (master private key), without revealing their respective secrets, the SM9 identification private key d for signa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com