Password generation and authentication method and device, electronic equipment and medium
An authentication method and technology for electronic equipment, which are applied to encryption devices with shift registers/memory, secure communication devices, electrical components, etc., can solve problems such as fixed-value password cracking, prevent brute force cracking, and increase key security. , enhance the effect of control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
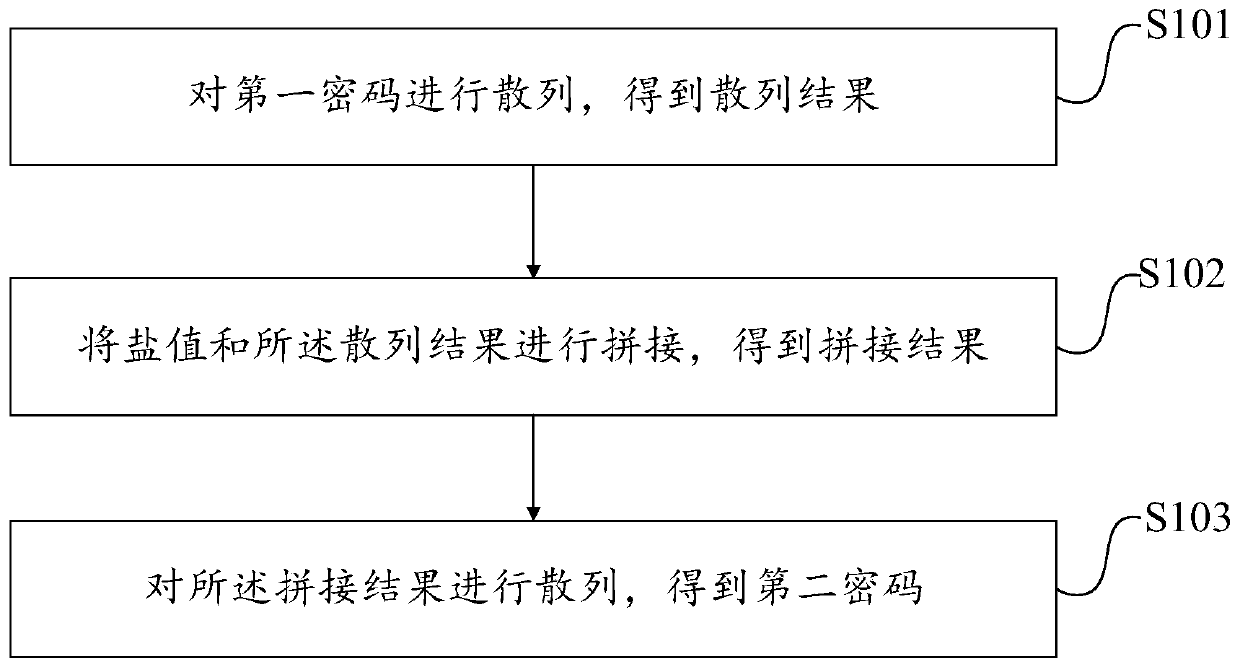
[0049] see figure 1 , the embodiment of the present disclosure provides a password generation method. Including the following steps:
[0050] S101: Hashing the first password to obtain a hash result;
[0051] When a user accesses through a terminal, it first needs to register, and when the user registers, a first password and a salt value are generated in response to a user request. The salt value sets the validity period, and the validity period can be customized.
[0052] Specifically, performing hashing on the first password is performing hash calculation on the first password by using a hash algorithm to obtain a hash result.
[0053] In a specific application scenario, such as the application scenario of the government department's government affairs system, first the user registers an account on the government department's government affairs system, and will get a password and salt value after successful registration. The validity period of the salt value is 24 hours...
example
[0060] Examples of splicing are as follows:
[0061] The result of the first password hash is:
[0062] qfIDdGxjCXJhC1Igpap34GZ / BBHyXNHYaXNwm8JO6e8=,
[0063] The salt value is:
[0064] pGe9vCaE1kb+P6WglZpQ3w==,
[0065] Then the splicing result is:
[0066] qfIDdGxjCXJhC1Igpap34GZ / BBHyXNHYaXNwm8JO6e8=pGe9vCaE1kb+P6WglZpQ3w==.
[0067] The above splicing result is hashed again to obtain the second password, and the result is: 648DB9886AA6A3CD833F3E45BD281B97C665D825C4EA375BF480EC9DBD779F6C.
[0068] For example, in the application scenario of the government affairs system of the government department, the hash algorithm still uses the SM3 hash algorithm.
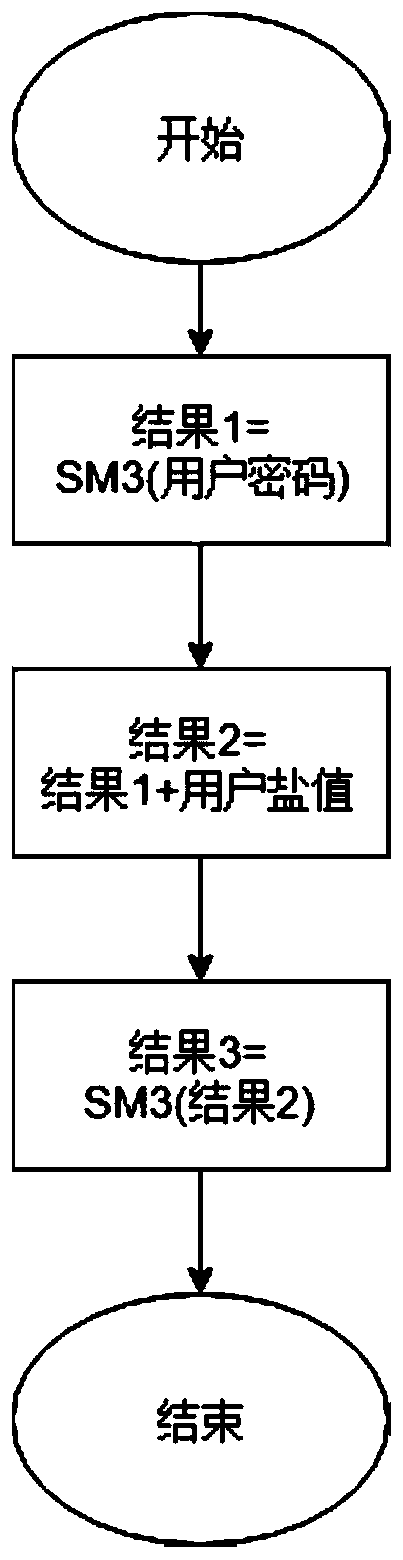
[0069] During password generation, such as figure 2 As shown, SM3 first performs hash calculation on the original text of the user password, and then splices the hash result with the salt value. Then use SM3 again for hash calculation on the spliced result. The formula is expressed as: Hash=SM3((SM3(pass)+salt)). ...
Embodiment 2
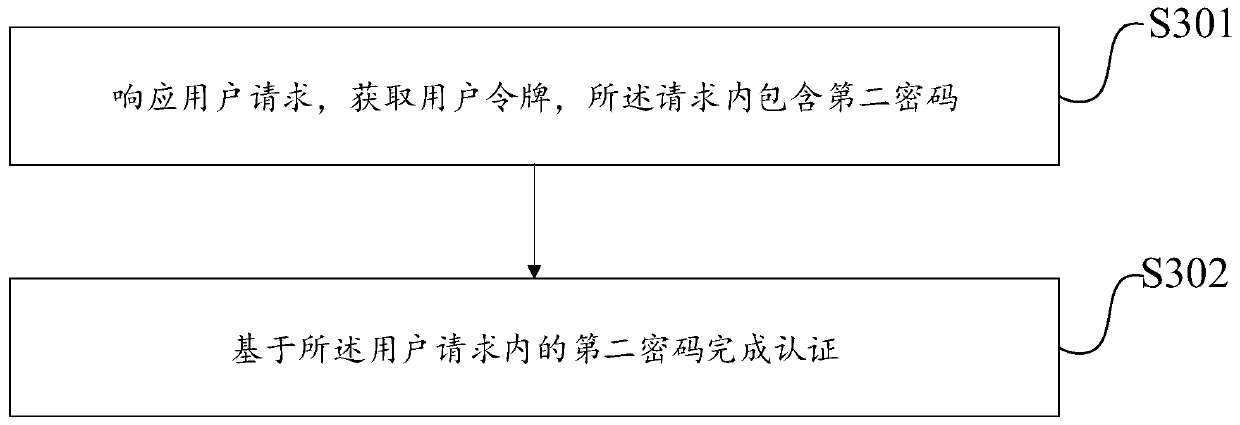
[0072] see image 3 , the embodiment of the present disclosure provides an authentication method. Including the following steps:
[0073] S301: Obtain a user token in response to a user request, where the request includes the second password generated by the method in Embodiment 1;
[0074] In a specific application scenario, such as the application scenario of the government affairs system of the government department, whenever the user sends a query request from the server to the government affairs system, it first needs to obtain the user token token. The parameters included in the request include the hashed password, that is, the second password generated by the method in Embodiment 1. Such as Figure 4 shown.
[0075] S302: Complete authentication based on the second password in the user request.
[0076] see Figure 5 , completing authentication based on the second password in the user request, including:
[0077] S501: Obtain a second password in the request;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com