Firewall policy query, elastic scaling method and system, device, storage medium
A firewall policy and query method technology, applied in the field of network security, can solve the problems of low elastic scaling efficiency, inaccurate policy query results, low firewall policy elastic scaling efficiency, etc., and achieve the effect of improving adjustment efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be described in detail below with reference to the accompanying drawings and specific embodiments. The embodiments cannot be repeated here, but the embodiments of the present invention are not limited to the following embodiments.
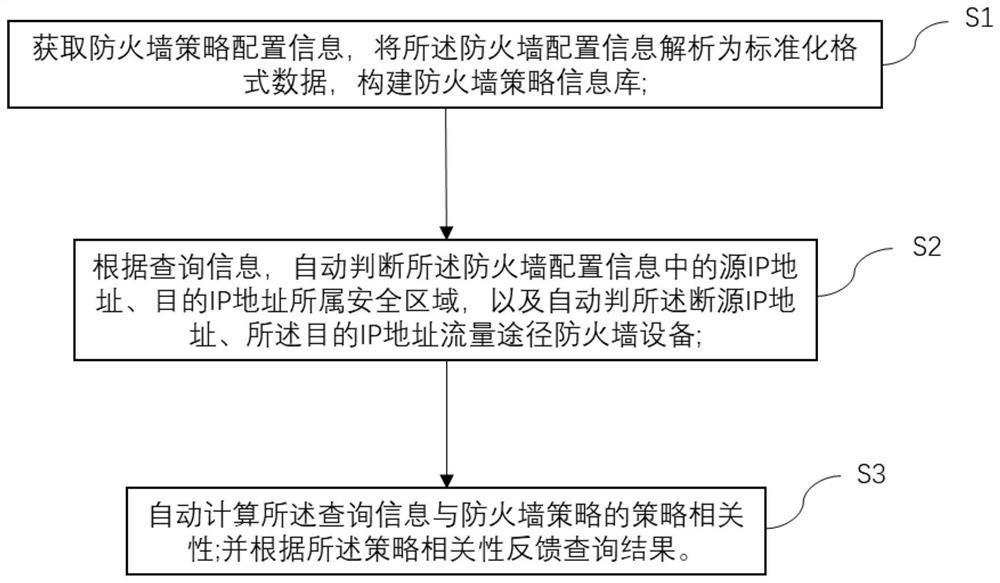
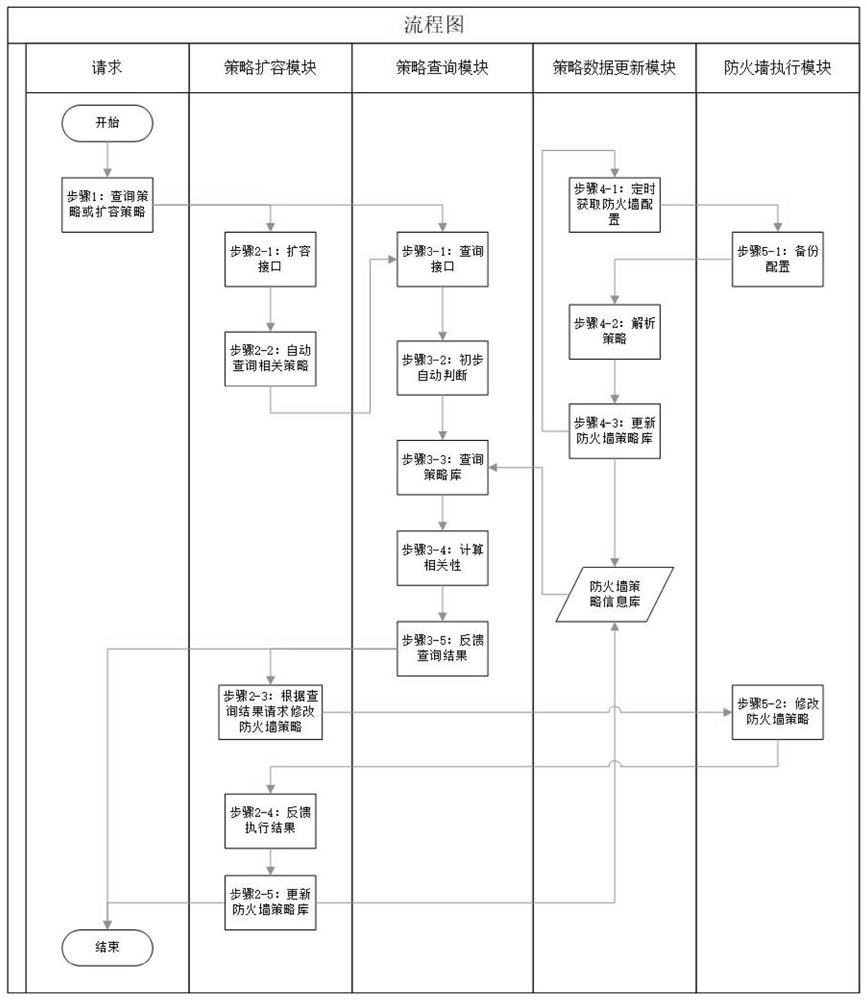
[0046] figure 1 It is a block diagram of steps used in the firewall policy query method of the present invention. like figure 1 As shown, a firewall policy query method of the present invention includes:
[0047] S1. Obtain firewall policy configuration information, parse the firewall configuration information into standardized format data, and build a firewall policy information base;
[0048] S2. According to the query information, automatically determine the security zone to which the source IP address and the destination IP address in the firewall configuration information belong, and automatically determine the source IP address and the destination IP address traffic path through the firewall device;
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com