Position privacy protection method based on Chinese remainder theorem and intelligent contract
A Chinese remainder theorem and smart contract technology, applied in the fields of communication, computer, and blockchain, it can solve the problems of centralized user trust and service quality, and achieve the effect of improving generation efficiency, protecting location privacy data, and ensuring credibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Blockchain technology originated in 2008 and was proposed by a scholar named Satoshi Nakamoto in the foundational article of cryptocurrency, "Bitcoin: A Peer-to-Peer Electronic Cash System". It was originally known as the underlying supporting technology of cryptocurrency, and later recognized by people for its good distributed storage, data immutability and decentralization. As an important part of blockchain technology 2.0, smart contracts not only inherit good features such as decentralization, but also complete a series of interactions through code logic. The emergence of blockchain and smart contract technology provides new ideas for traditional location privacy protection solutions.
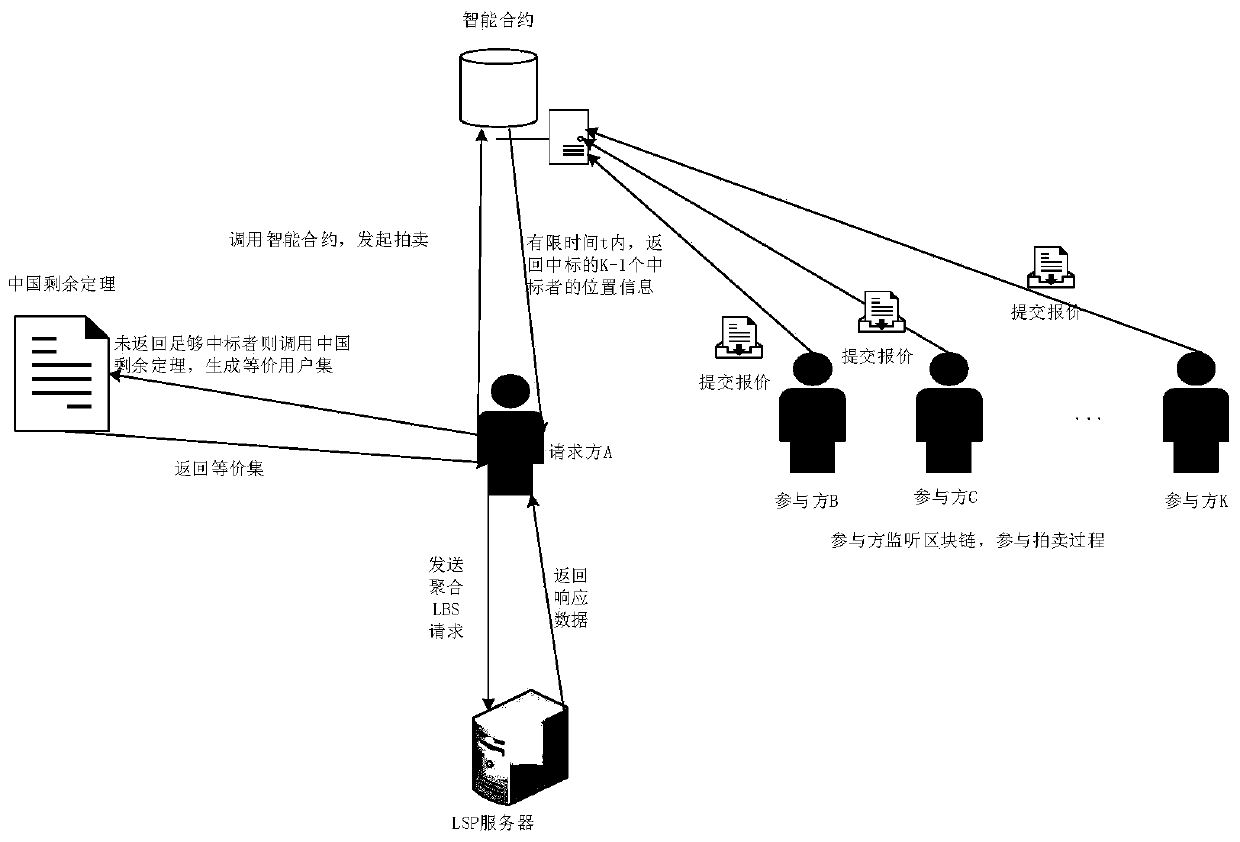
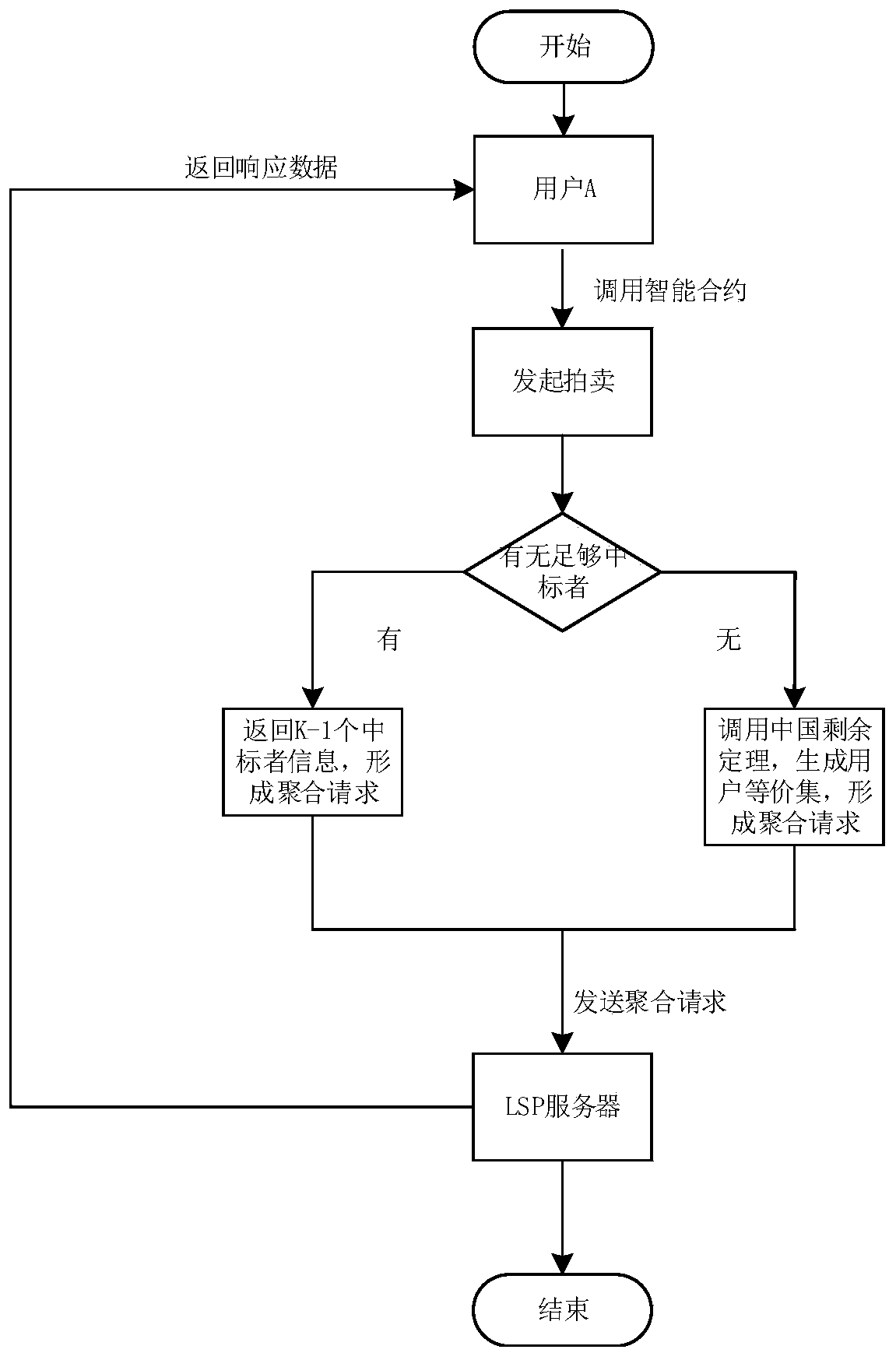
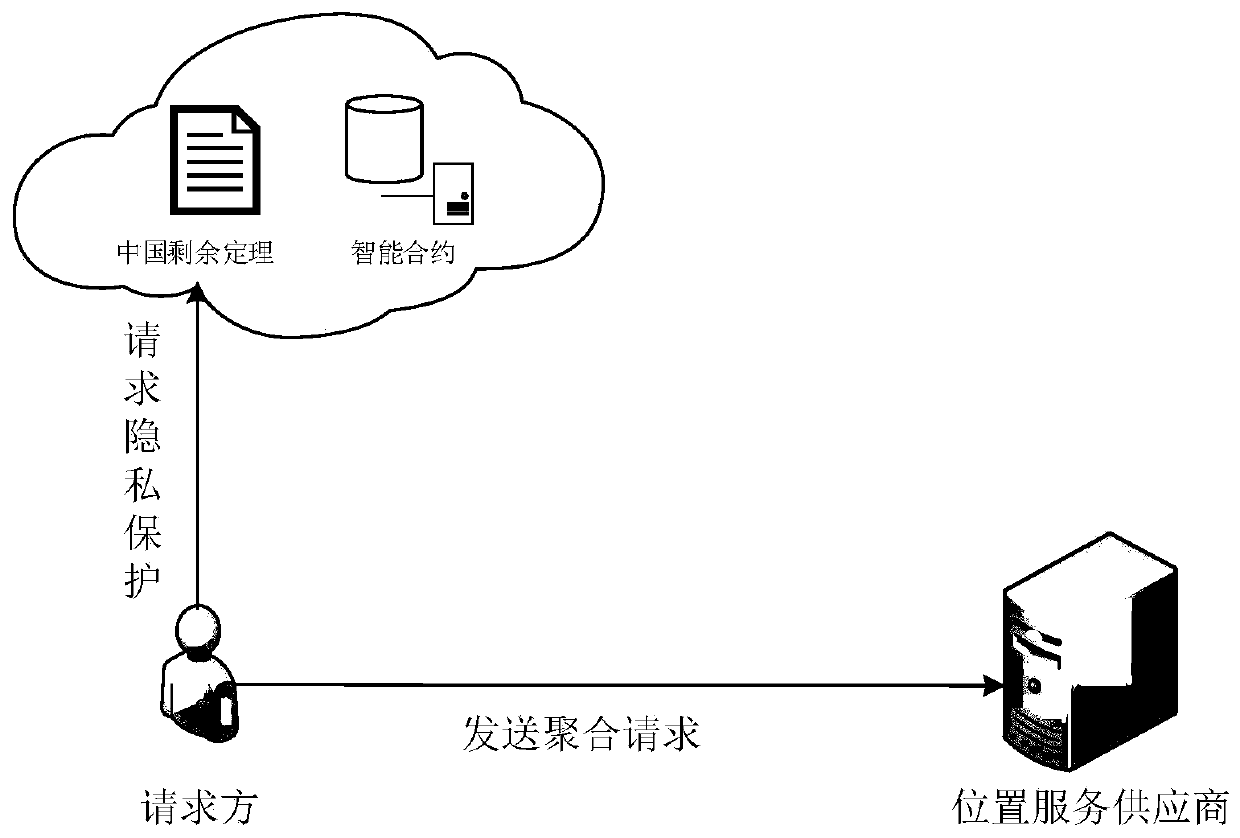
[0052] Aiming at the problems in the prior art mentioned in the background technology above, this application provides a location privacy protection method based on the Chinese remainder theorem and smart contracts. The overall idea of the method is: when the requesting party wants...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com