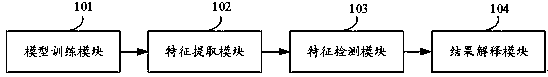
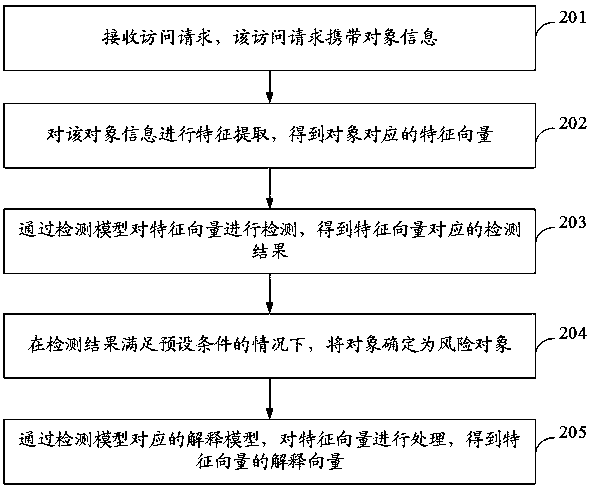
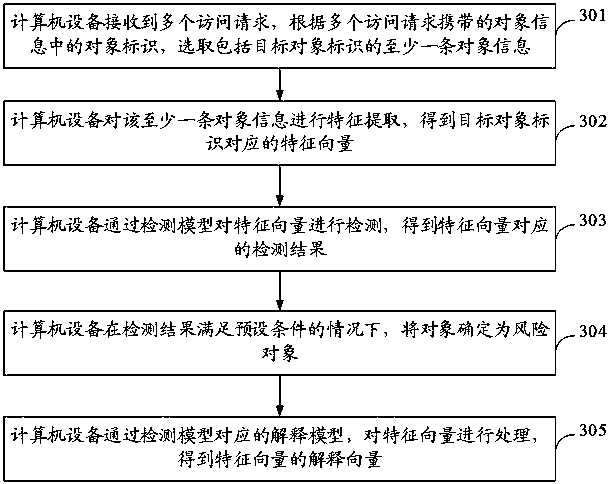
Network risk detection method, device, equipment and medium based on object characteristics
A technology of object characteristics and risk detection, applied in the computer field, can solve problems such as difficulty in ensuring the accuracy of risk objects, labor and time consumption, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0096] In order to make the purpose, technical solutions and advantages of the embodiments of the present application clearer, the following will further describe the embodiments of the present application in detail in conjunction with the accompanying drawings.
[0097] It can be understood that the terms "first", "second" and the like used in this application may be used to describe various concepts herein, but unless otherwise specified, these concepts are not limited by these terms. These terms are only used to distinguish one concept from another. For example, without departing from the scope of the present application, a first sample feature vector may be referred to as a second sample feature vector, and similarly, a second sample feature vector may be referred to as a first sample feature vector .
[0098] Wherein, at least one piece refers to one or more pieces of object information. For example, at least one piece of object information may be any integer piece of ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com