Message recombination method and network equipment
A network device and message technology, applied in the field of communication, can solve the problem of low efficiency of message fragmentation and recombination, achieve the effect of improving recombination efficiency and reducing transmission delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
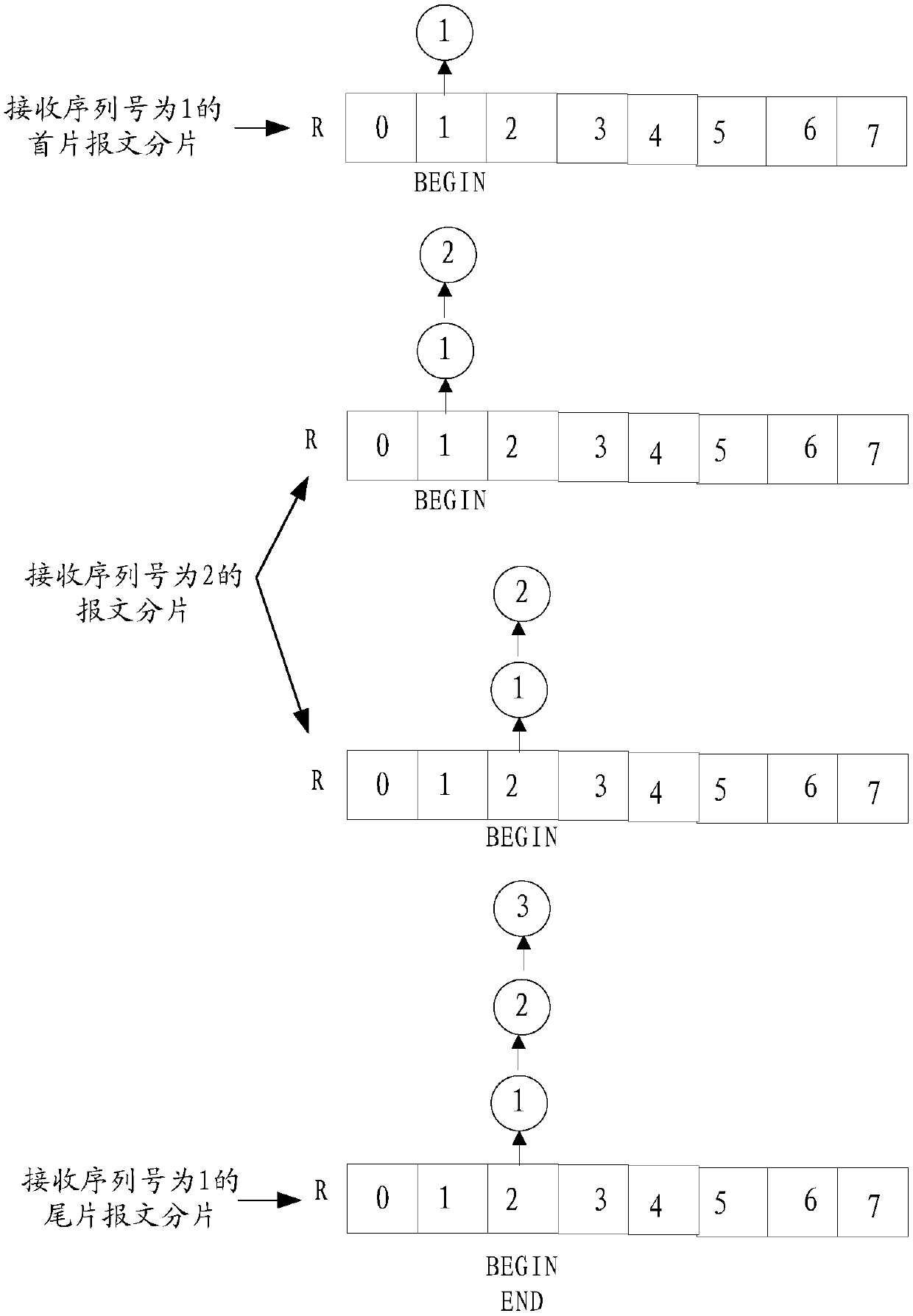
[0071] Example 1: The serial numbers of the message fragments received by a network device are 1, 2, and 3 respectively. According to the above method, the fragment receiving process is as follows: figure 2 shown.
[0072] Specifically, such as figure 2 As shown, after the network device receives the first packet fragment with the sequence number 1, it stores the first packet fragment in the storage unit R[1], and after receiving the packet fragment with the sequence number 2 After fragmentation, append the message fragmentation to the end of the fragmentation chain of storage unit R[1], and record the reorganized fragmentation chain into storage unit R[2]. After the message is fragmented, the storage unit R[2] is not empty, and the message fragment is appended to the tail of the fragment chain of the storage unit R[2]. Since the message fragment with the sequence number 3 is the tail piece Message fragmentation, because there are signs of the first message fragmentation a...
example 2
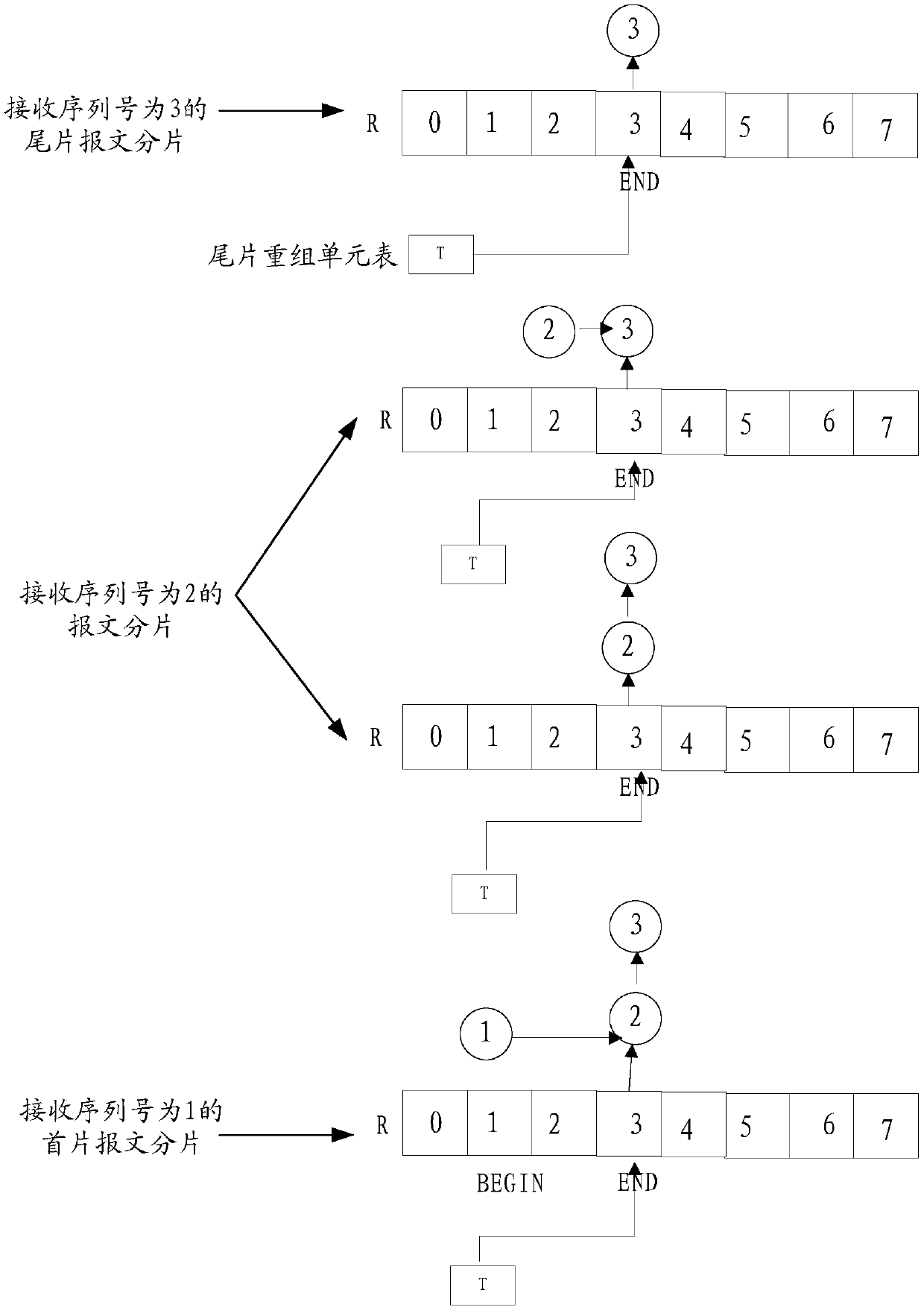
[0073] Example 2: The sequence numbers of the packet fragments received by the network device are 3, 2, and 1 respectively. According to the above method, the fragment receiving process is as follows: image 3 shown.
[0074] Specifically, such as image 3 As shown, after the network device receives the fragment of the tail message with the serial number 3, it stores the fragment of the tail message in the storage unit R[3]. After receiving the fragment of the message with the serial number 2 After fragmentation, add the message fragmentation to the head of the fragmentation chain of storage unit R[3], and record the reorganized fragmentation chain into storage unit R[3]. After the message is fragmented, add the message fragment to the header of the fragment chain of the storage unit R[3]. Then integrate and submit the shard chain.
example 3
[0075] Example 3: The sequence numbers of the message fragments received by the network device are 2, 1, 4, 3, 6, 5 respectively. According to the above method, the fragment receiving process is as follows: Figure 4 shown.
[0076] Specifically, such as Figure 4As shown, after the network device receives the message fragment with the serial number 2, it stores the message fragment in the storage unit R[2], and after receiving the message fragment with the sequence number 1, it stores the The message fragment is appended to the head of the fragment chain of the storage unit R[2], and the reorganized fragment chain is recorded in the storage unit R[2]. After receiving the message fragment with the sequence number 4 Afterwards, the message fragment is stored in the storage unit R[4]. After receiving the message fragment with the sequence number 3, since the front and rear adjacent storage units of the storage unit R[3] are non-empty, then Integrate the fragmentation of the me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com