Encrypted traffic identification method based on ensemble learning
An integrated learning and flow recognition technology, applied in character and pattern recognition, digital transmission systems, instruments, etc., can solve problems such as unbalanced number of class samples, unbalanced data flow distribution, and underfitting.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
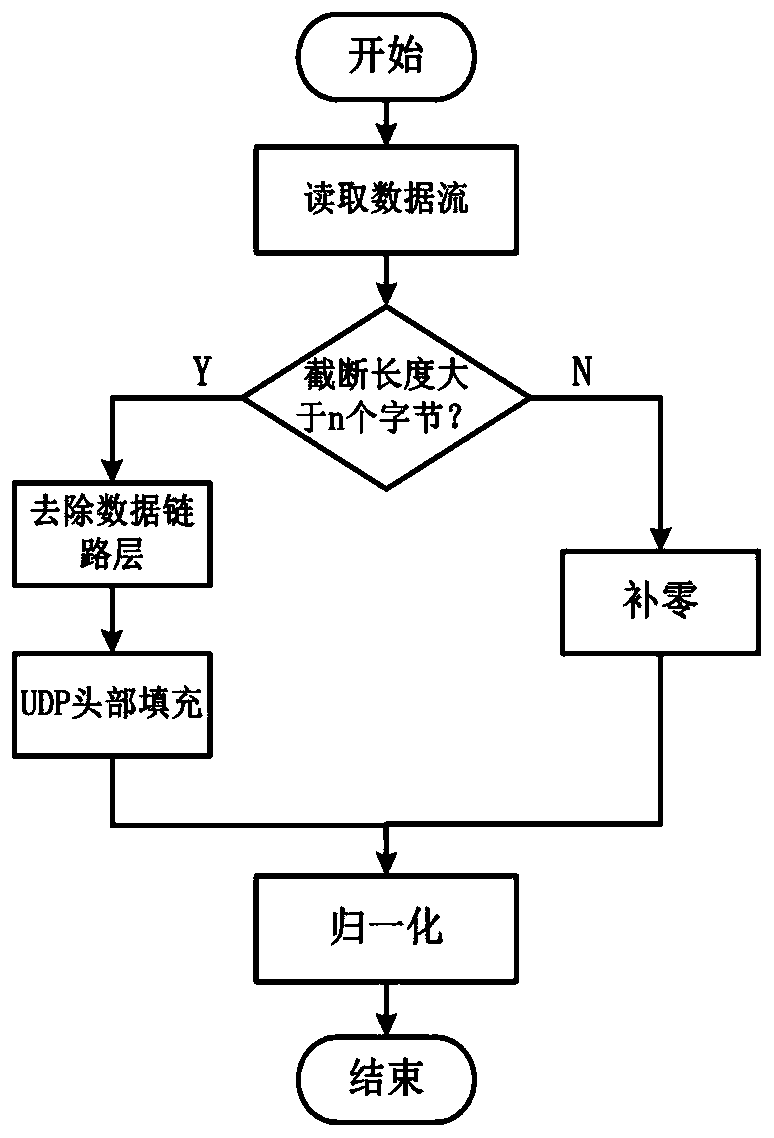
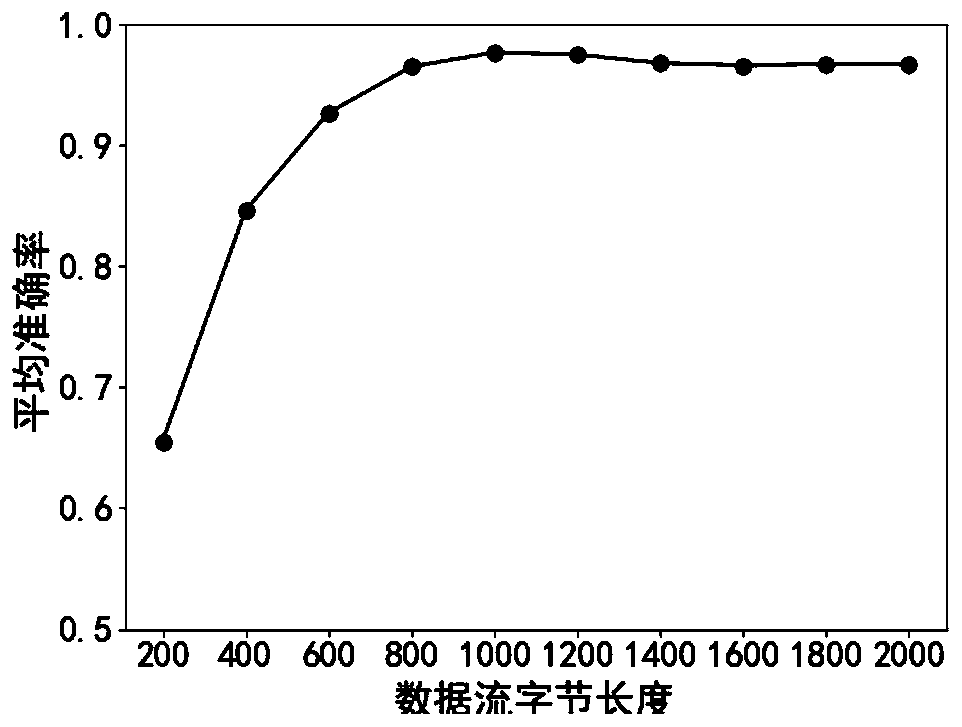
[0020] The present invention provides a method for identifying encrypted traffic based on integrated learning. Aiming at the problems of unbalanced categories of sample data sets, difficulty in feature extraction, and feature redundancy, the original data set is balanced by the SMOTE algorithm, the data packet load is extracted, and the stack is used to The automatic encoder model automatically extracts features, and finally inputs the classifier based on ensemble learning for classification evaluation.
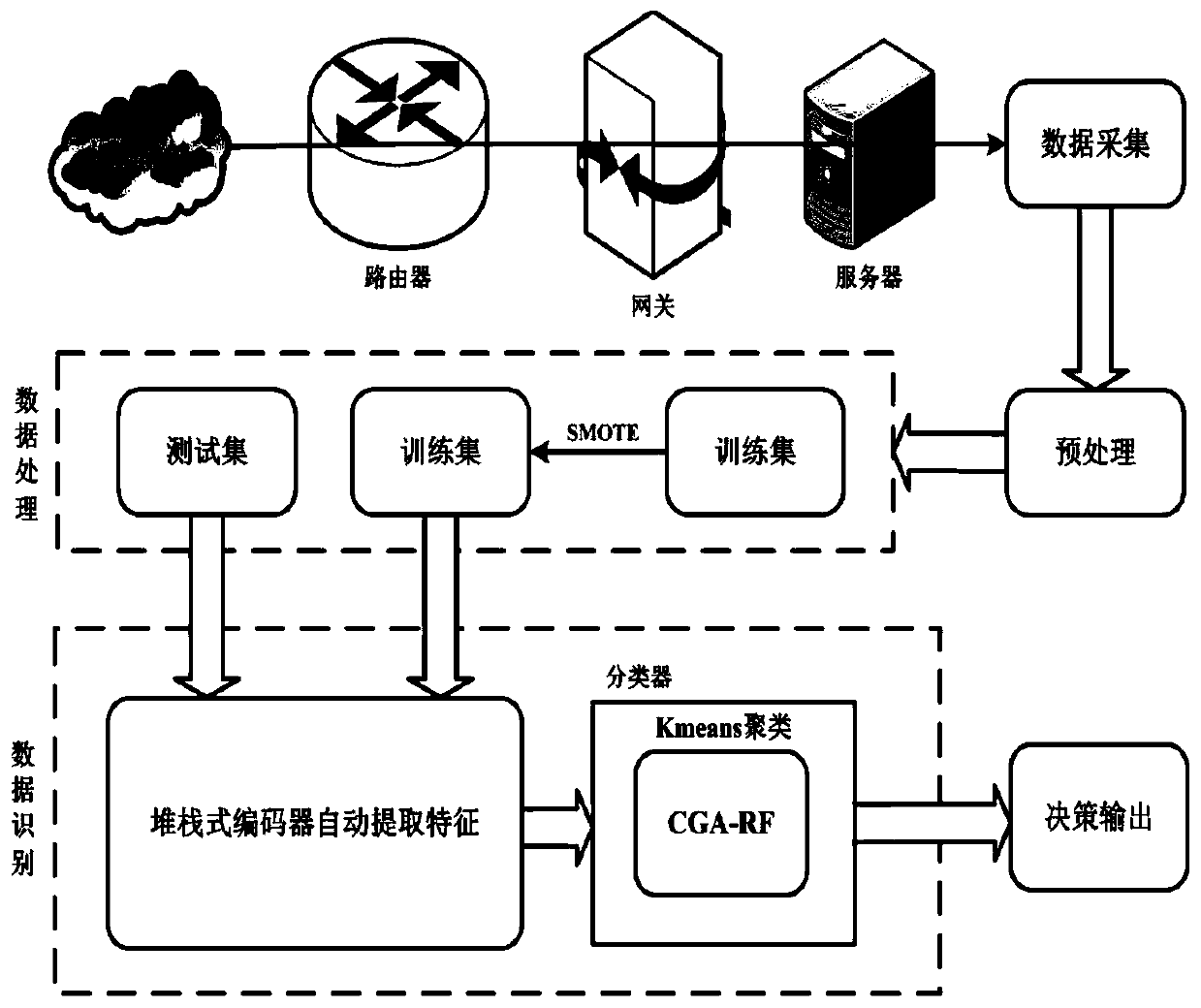
[0021] like figure 1 As shown, the process of encrypted traffic identification method based on ensemble learning includes at least several steps: data set collection, data preprocessing, balancing data set, automatic feature extraction, traffic identification and index result analysis.
[0022] Data set collection is to use Wireshark to capt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com