Secure secret key and ciphertext generation, storage and transmission method and device
A key generation and ciphertext technology, which is applied to secure communication devices and key distribution, can solve problems such as theft, loss of security information keys, and inability to guarantee the security of key storage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
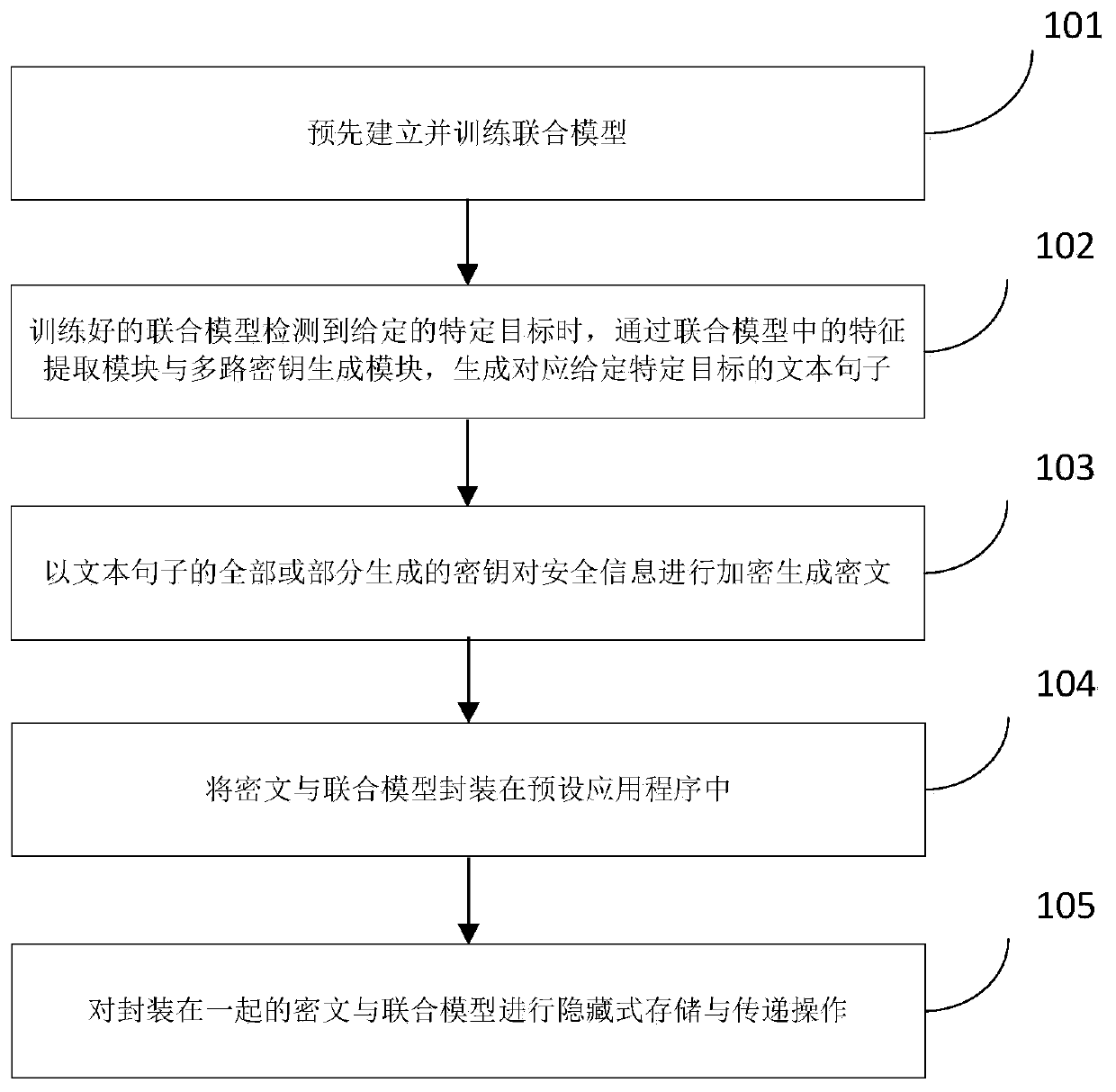
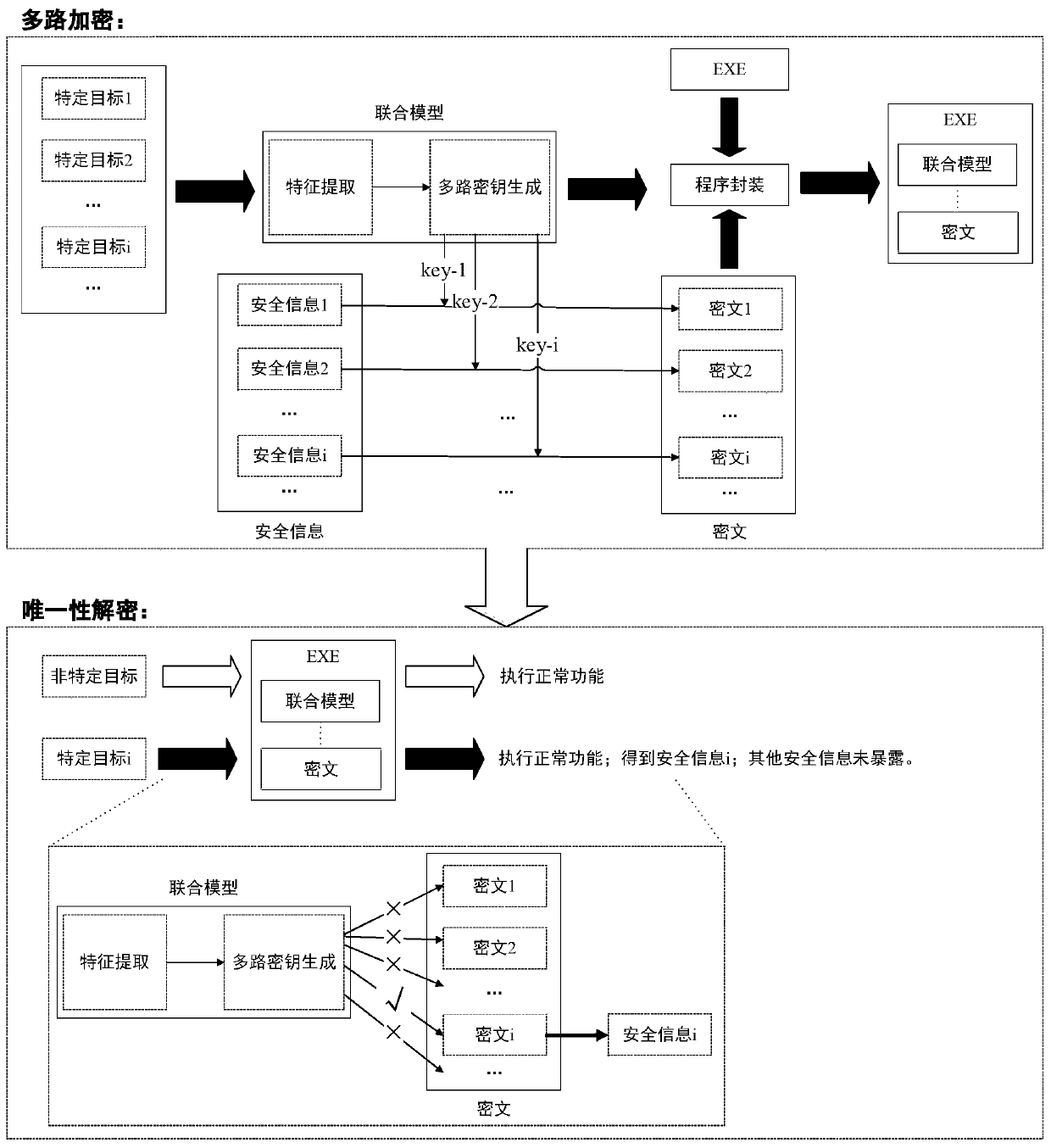
[0022] The application will be further described in detail below in conjunction with the drawings and embodiments.
[0023] In the following introduction, the terms "first" and "second" are only used for descriptive purposes, and cannot be understood as indicating or implying relative importance. The following description provides multiple embodiments of the present disclosure, and different embodiments can be replaced or combined. Therefore, this application may also be considered to include all possible combinations of the same and / or different embodiments described. Therefore, if one embodiment includes features A, B, C, and another embodiment includes features B, D, then this application should also be considered as including all other possible combinations of one or more of A, B, C, and D Although the embodiment may not be clearly written in the following content.
[0024] In order to make the objectives, technical solutions, and advantages of the present invention clearer, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com