Alarm method and device thereof
A technology of alarm time and log, which is applied in the computer field, can solve the problem that the server cannot alarm in time, achieve the effect of reducing operation complexity, avoiding false alarm problems, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
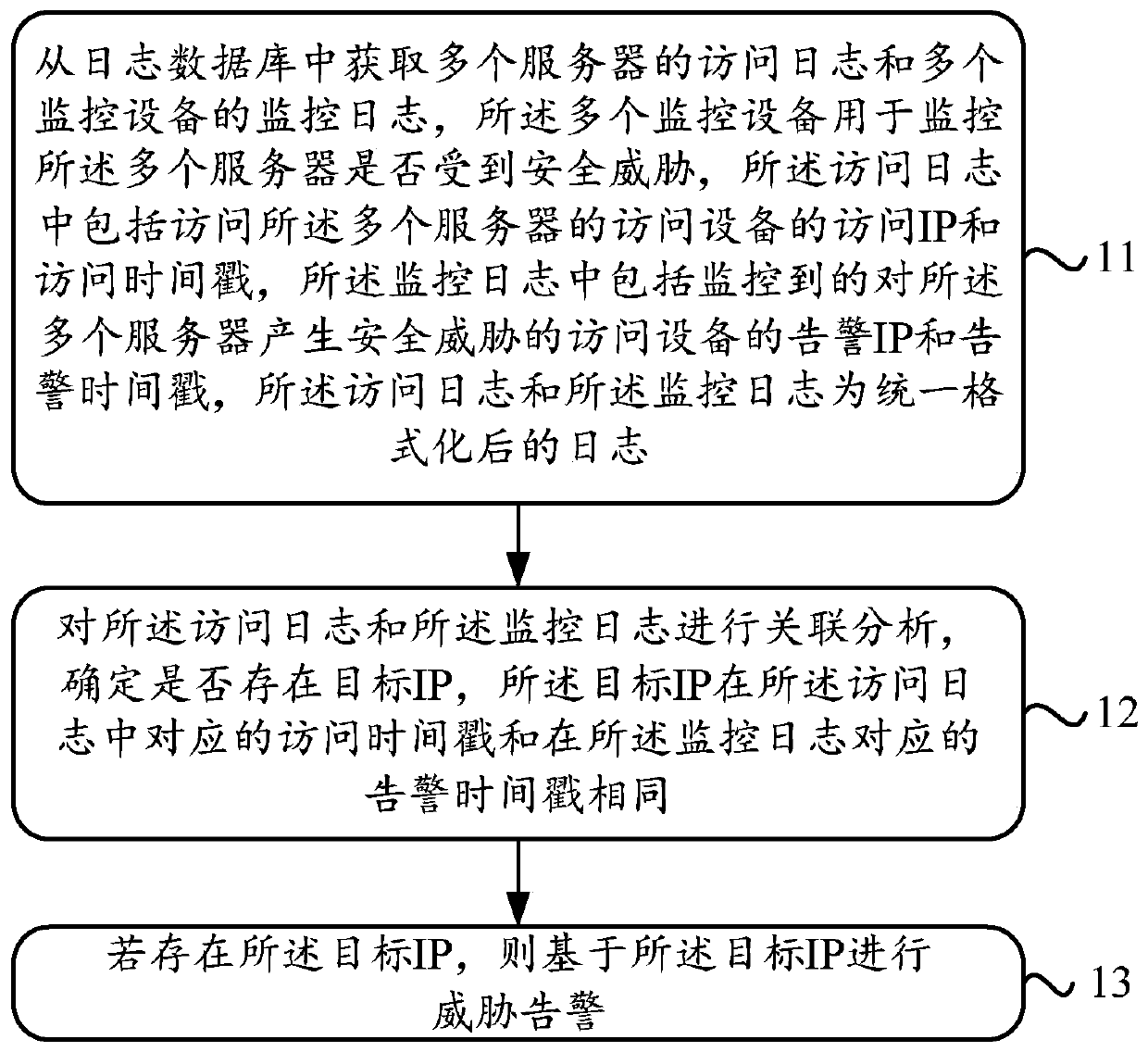
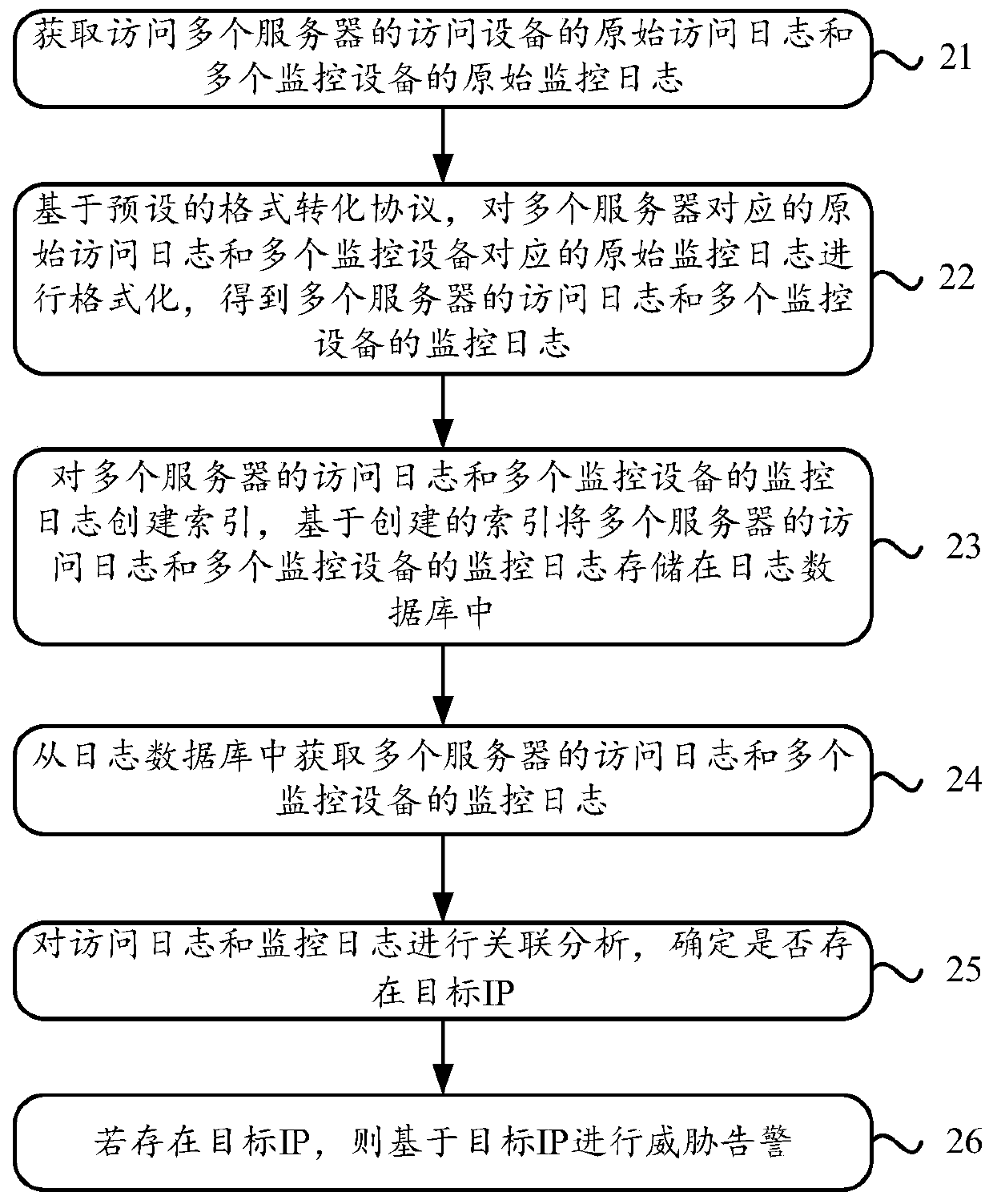
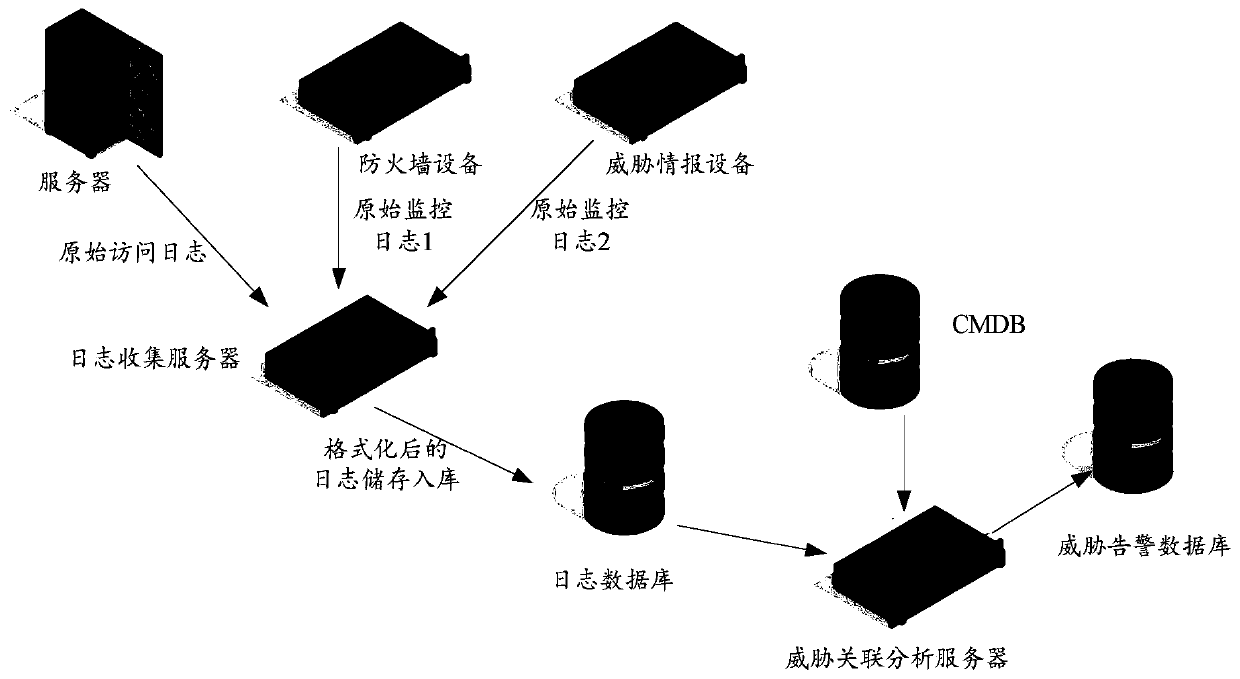
[0021] In the process of the server providing external services, multiple different monitoring devices can be used to monitor whether the server is subject to security threats. However, different monitoring devices may have different sensitivity to security threats, which makes the monitoring of different monitoring devices Results may be inconsistent, making it impossible to accurately determine whether a server is compromised.
[0022] For example, during the process of server 1 providing external services, monitoring device A and monitoring device B can simultaneously monitor whether server 1 is threatened by security. Among them, if the sensitivity of monitoring device A to security threats is too low, and the sensitivity of monitoring device B to security threats is too high, the following monitoring results will appear: monitoring device A monitors that server 1 is not threatened by security, monitoring device B It is monitored that server 1 is threatened by security, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com