Merchant fraud risk monitoring system and data mining method
A data mining and monitoring system technology, applied in data processing applications, instruments, finance, etc., can solve problems such as low labor efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
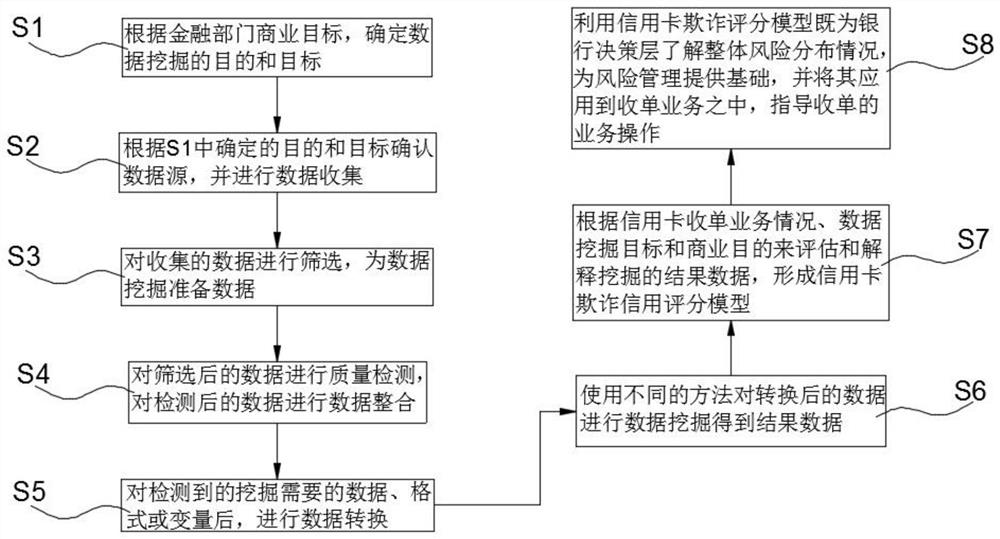
[0041] This embodiment discloses as figure 1 A data mining method for a merchant fraud risk monitoring system is shown, the method includes the following steps:
[0042] S1 Determine the purpose and goal of data mining based on the business goals of the financial sector;
[0043] S2 confirms the data source according to the purpose and target determined in S1, and conducts data collection;
[0044] S3 screens the collected data and prepares data for data mining;
[0045] S4 Perform quality testing on the filtered data, and perform data integration on the tested data;
[0046] S5 performs data conversion after detecting the data, format or variables required for mining;
[0047] S6 uses different methods to perform data mining on the converted data to obtain the result data;
[0048] S7 evaluates and interprets the result data of the mining according to the credit card acquiring business situation, data mining goals and business purposes, forming a credit card fraud credit scoring model;
...
Embodiment 2
[0066] In this embodiment, based on the implementation experience of the Gibbeck data mining project and strictly in accordance with the general data mining methodology, the entire data mining process can be divided into the following 10 steps: they are business purpose determination, data source identification, data collection, and data selection. , Data quality review, data conversion, data mining, result interpretation, application suggestion and result application.
[0067] (1) Determination of business goals: Clarifying the purpose or goal of data mining is the key to the successful completion of any data mining project. For example, determining the goal of the project is to build a credit card fraud analysis model.
[0068] (2) Confirm the data source: Given the business goals of data mining, the next step is to find data that can solve and answer business problems. What is needed to build a fraud analysis model is a lot of information about credit card transactions, and as m...
Embodiment 3
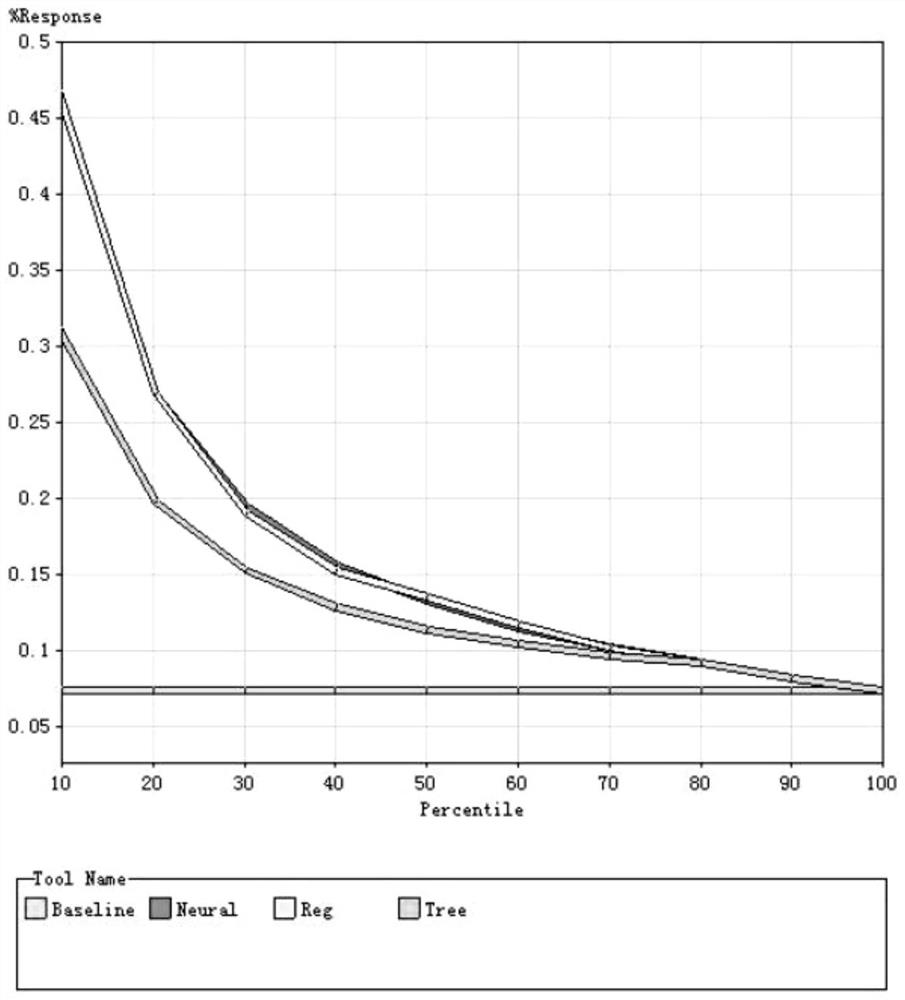
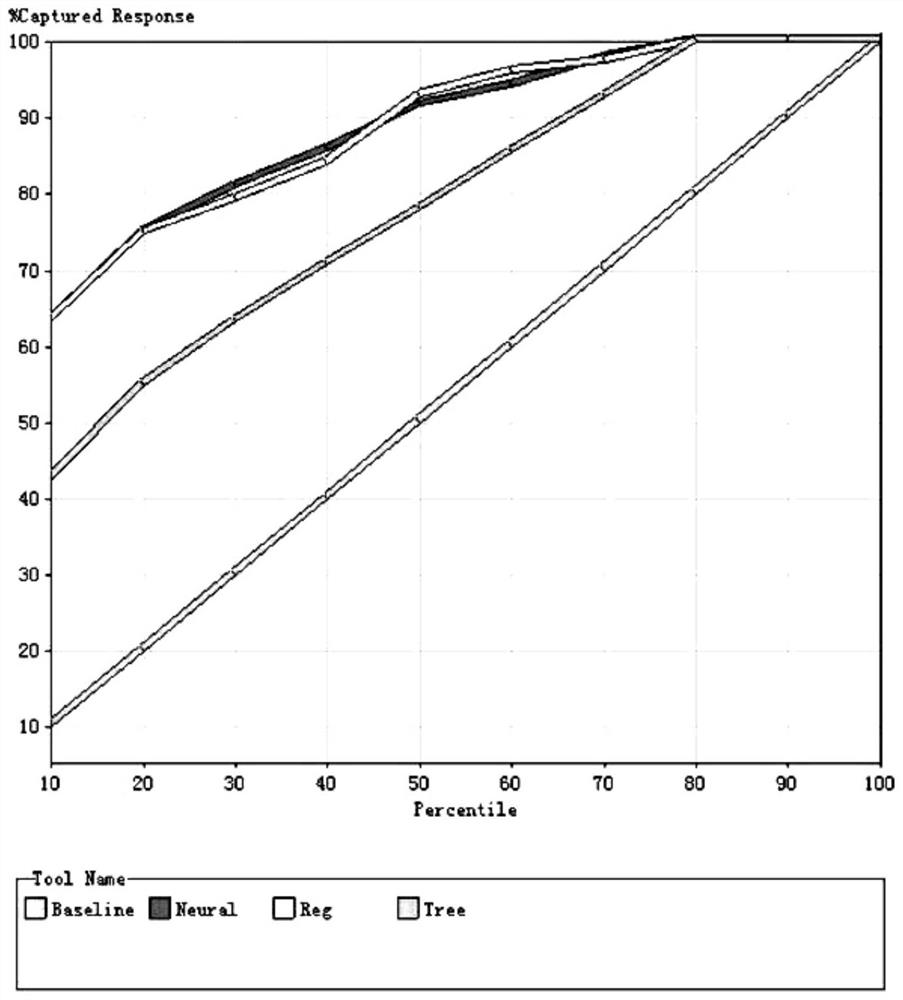
[0078] This embodiment analyzes the data by taking the example of transaction behavior. The objective of the Bank of Communications' credit card acquiring bank risk monitoring system is to use advanced data mining technology to conduct in-depth analysis of historical transaction information, find out the hidden knowledge and laws, and develop transaction fraud risks. The scoring model is used to identify fake cards and fake cards of credit cards, find out the transactions generated by fake cards and fake cards, and use them to predict the probability that credit card transactions are fraudulent, providing a scientific basis for formulating intelligent anti-fraud strategies. Specifically, the system should achieve:
[0079] Analyze massive credit card transaction data, establish a fraud identification model for fake cards, shorten the time between fraud occurrence, identification, and processing, and reduce losses caused by fake cards;
[0080] Continue to track and explore new cred...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com