Identity recognition method based on abnormal behavior detection
A technology of identity recognition and behavior, applied in the field of identity recognition, can solve problems such as weak generalization ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
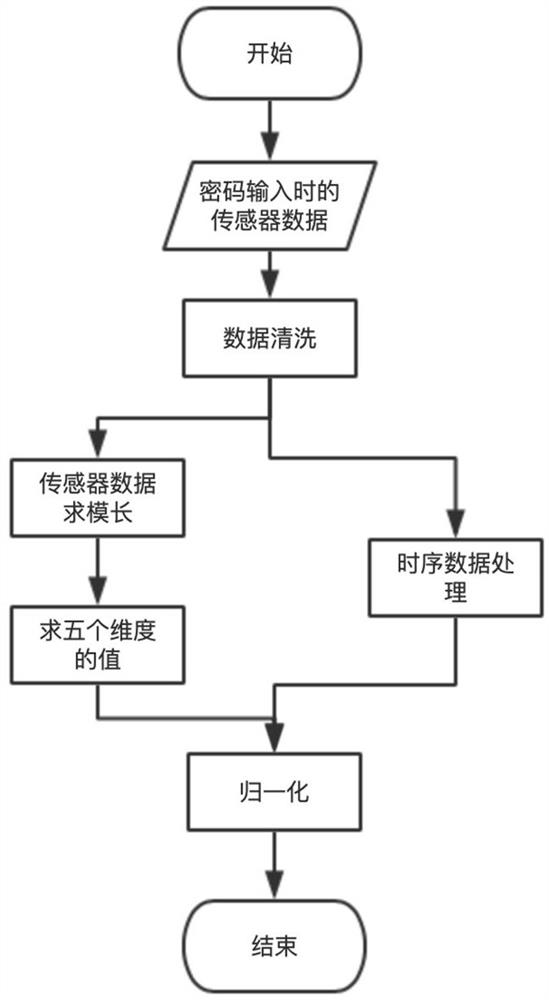
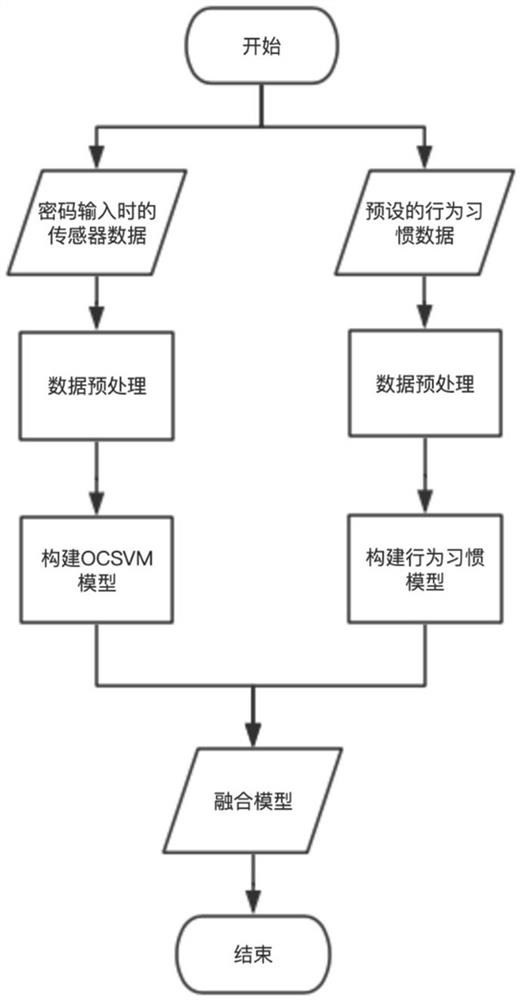
[0060] Such as image 3 As shown, an identification method based on abnormal behavior detection includes the following steps:
[0061] Step 1): Collect the sensor data of the user entering the same password multiple times on the same smartphone;
[0062] Each sensor includes device orientation sensor, acceleration sensor, magnetic field sensor, gyroscope sensor;
[0063] Each sensor data includes device orientation sensor, acceleration sensor, magnetic field sensor, gyroscope sensor axis data;
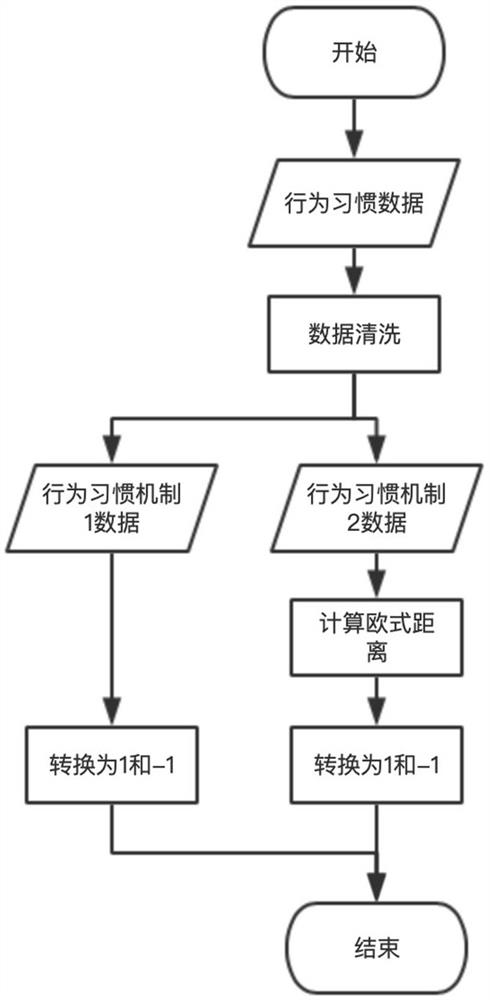
[0064] Step 2): Collect the user's response to the preset behavior mechanism before and after entering the user password;
[0065] The response results of the preset behavioral habit mechanism specifically include:
[0066] When there are numbers in the entered user name, it will be used as the reaction result of the user's first behavior habit mechanism according to whether the user uses the number keyboard or directly uses the numbers in the alphabet keyboard;
[0067] The data o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com