User feature extraction method and device, electronic equipment and readable storage medium
A technology of user characteristics and extraction methods, applied in the field of information processing, to achieve the effect of accurate user portraits and guaranteeing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
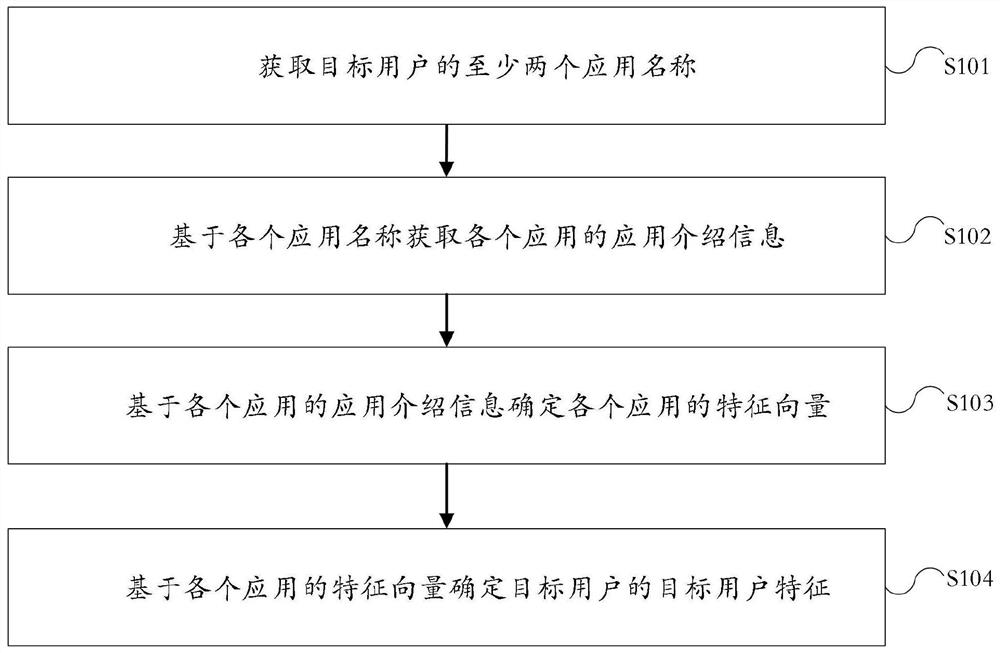
[0055] The embodiment of this application provides a user feature extraction method, which is applied to the terminal device side, such as figure 1 As shown, the method may include the following steps:
[0056] Step S101, acquiring at least two application names of the target user;
[0057] Specifically, the name of the application installed by the target user on the terminal device can be obtained by invoking or querying the application registry of the terminal device; as another implementation method, a screenshot of the terminal device screen can be obtained, and then the terminal device installation can be obtained by identifying the image recognition method. The application information; where at least two application names can be obtained.
[0058] Wherein, the terminal device may be a mobile phone, a PAD, or a wearable device (smart watch, smart glasses, etc.).
[0059] Step S102, acquiring application introduction information of each application based on each applicatio...
Embodiment approach
[0089] The first one is to determine the weight of the application according to the download volume of the application, and the second one is to determine the weight of the application according to the last use (or installation) time of the application. The smaller the weight of the user's personalized features should be, and the longer the last time the application is used, the smaller the weight should be;
[0090] Such as Figure 5 As shown, the third one adopts the self-attention mechanism, that is, the k-th app weight bk is calculated through the deep neural network according to the introduction information of the application, and bk is multiplied by ak after normalization. Examples of deep networks include RNN, LSTM, or other text classification networks, which only need to satisfy the input as text and the output as a probability value from 0 to 1 (the text network using sigmoid as the final activation function meets the requirements. This "self-attention The "mechanis...
Embodiment 2
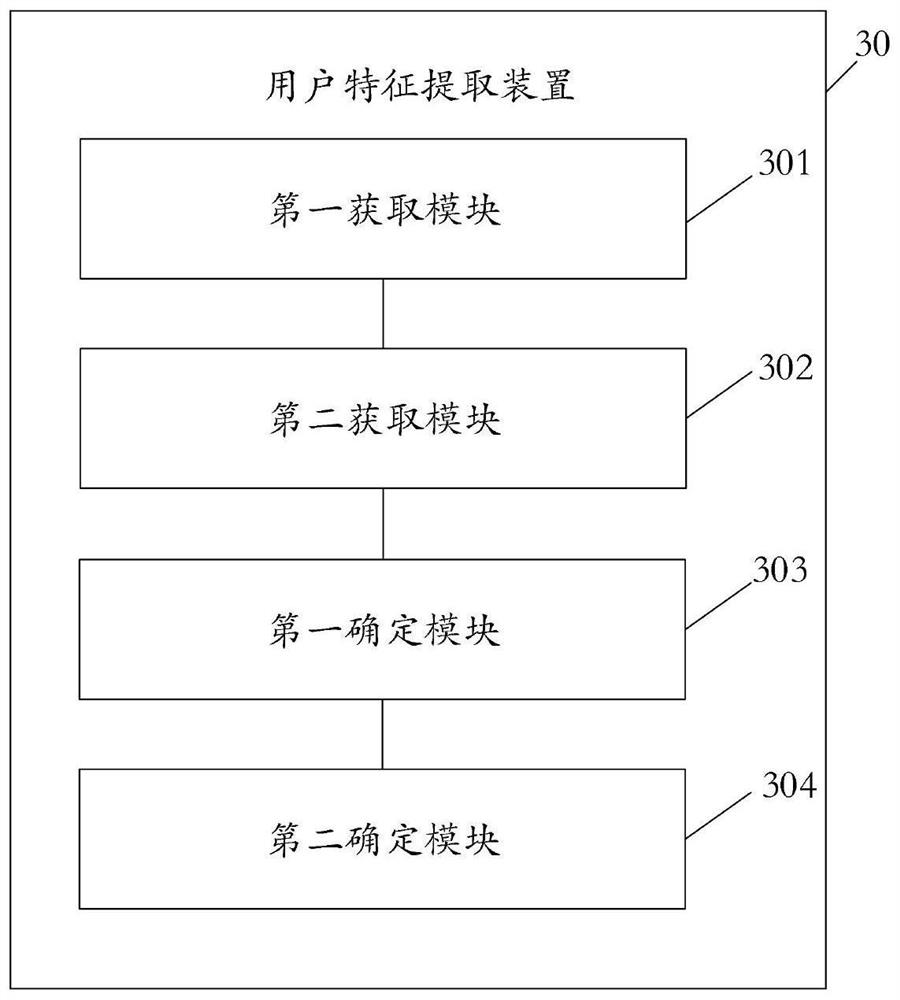
[0096] figure 2 An apparatus for extracting user features provided by an embodiment of the present application, the apparatus 20 includes: a first acquisition module 201, a second acquisition module 202, a first determination module 203, and a second determination module 204, wherein,
[0097] The first acquisition module 201 is configured to acquire at least two application names of the target user;
[0098] The second acquiring module 202 is configured to acquire application introduction information of each application based on each of the application names;
[0099]The first determining module 203 is configured to determine the feature vector of each application based on the application introduction information of each application;
[0100] The second determining module 204 is configured to determine target user characteristics of the target user based on the feature vectors of each application.
[0101] The embodiment of the present application provides a user feature e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com