Malicious Traffic Detection Method Fused with Deep Neural Network and Hierarchical Attention Mechanism
A detection method, malicious traffic technology, applied in neural learning methods, biological neural network models, neural architectures, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0114] Embodiments of the present invention will be described in detail below, and examples of the embodiments are illustrated in the drawings, in which the same or similar reference numerals represent the same or similar elements or elements having the same or similar functions. The following is exemplary, and is intended to be illustrative of the invention, not to be construed as limiting the invention.
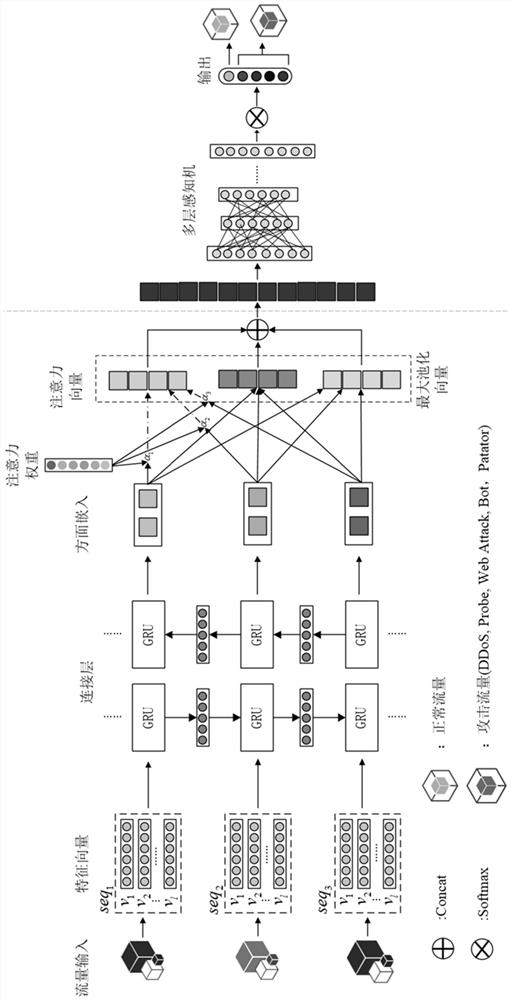
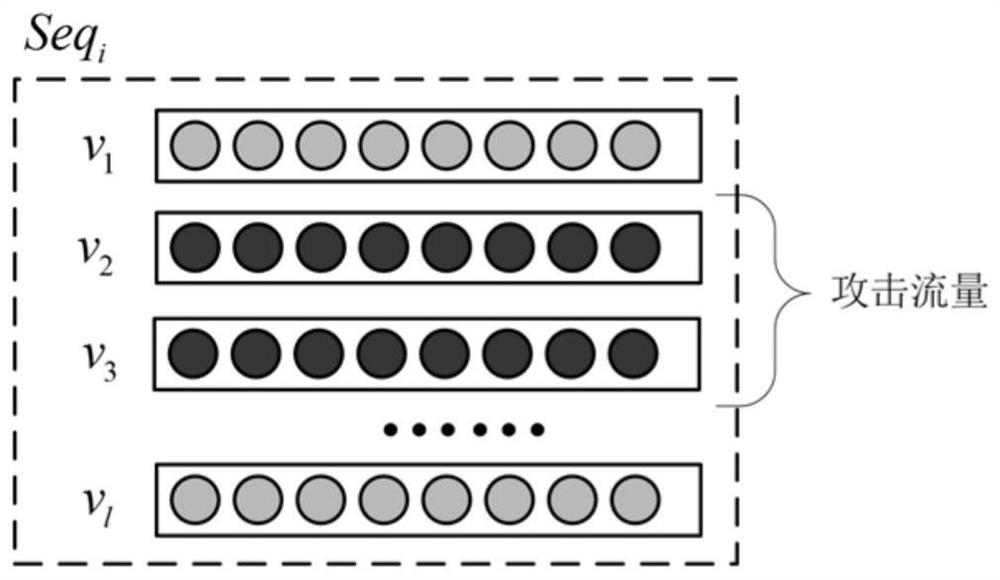
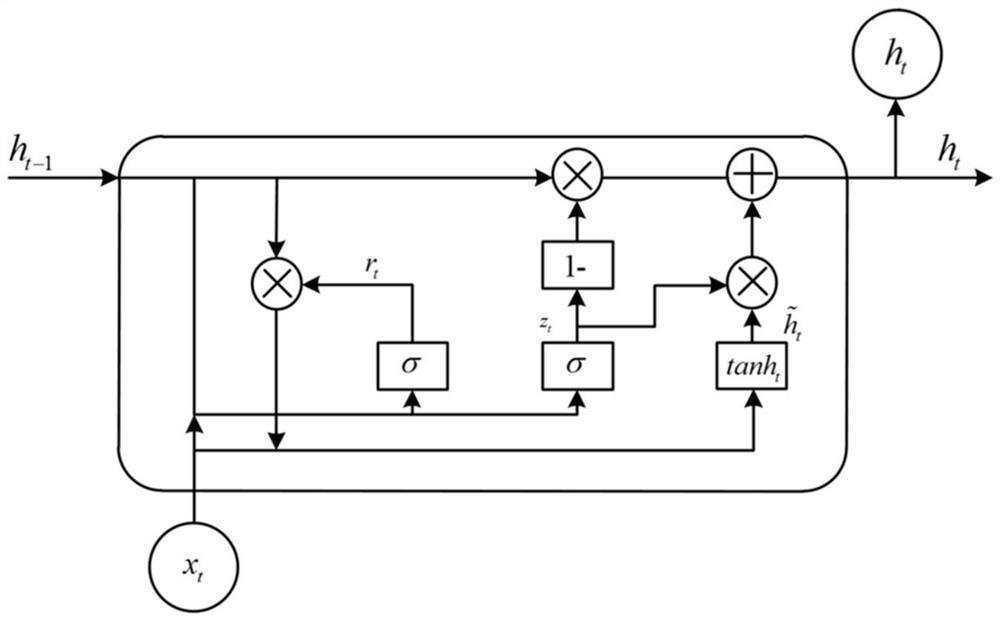
[0115] The present invention proposes a hierarchical precaution model (HAGRU) for malicious flow detection, and the model is based on currently effective, reliable depth cycle neural network. The hierarchical attention is compared with the previously proposed neural network for malicious flow detection, a relatively high detection rate, a relatively low false positive rate and relatively good real-time. Schematic diagram of the hierarchical attention of malicious flow detection figure 1 Indicated.
[0116] The hierarchical precision model (HAGRU) designed for malicious flow det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com