Portrait biological characteristic privacy protection and decryption method
A privacy protection and biometric technology, applied in the field of deep learning applications, can solve problems such as illegal use of privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
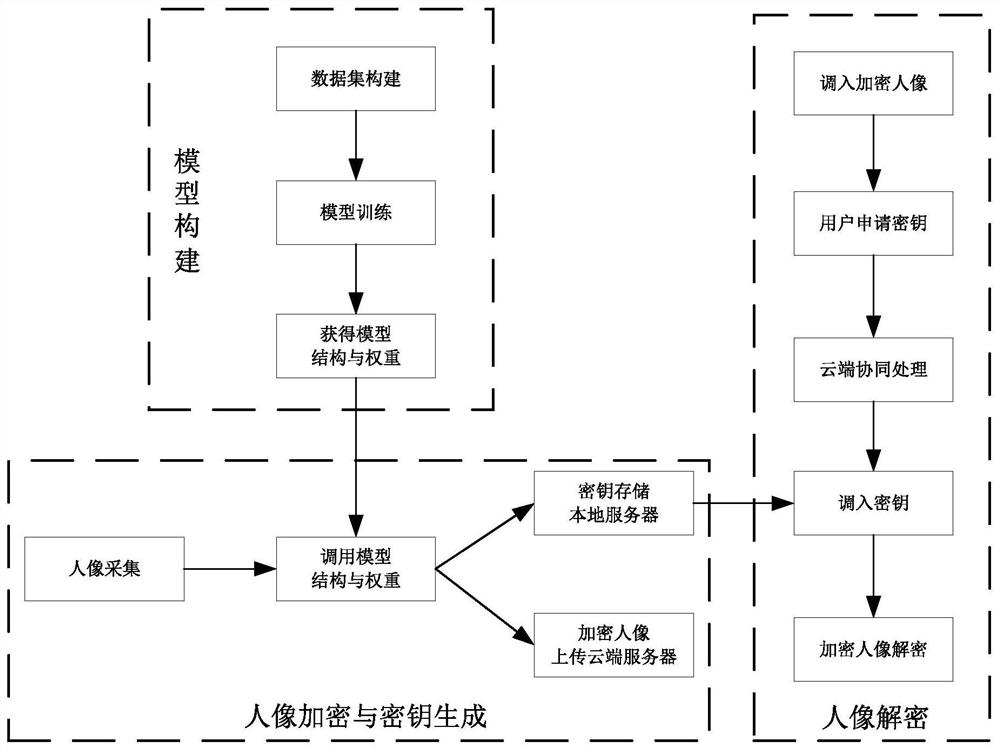
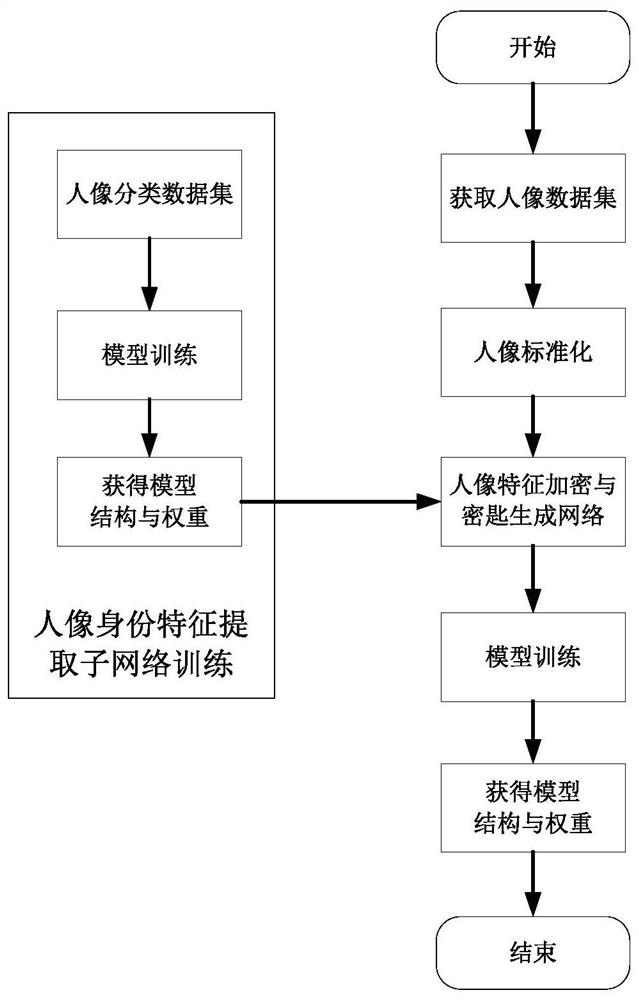
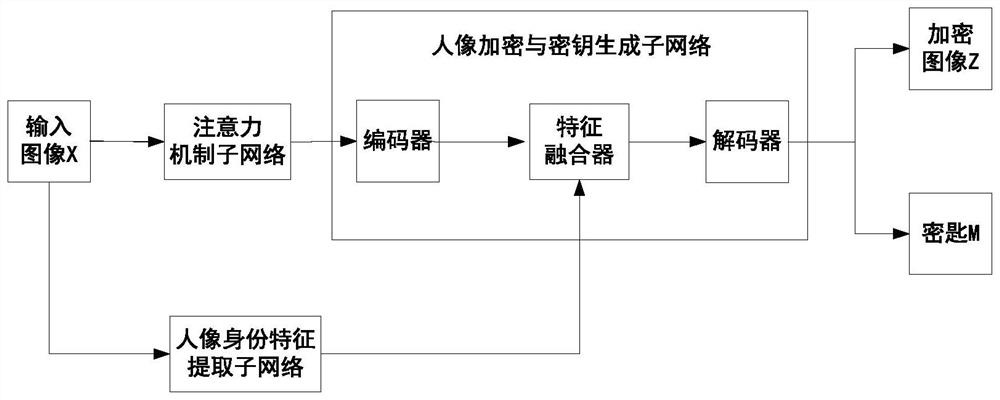
[0056] The technology of the network architecture design in this embodiment mainly involves the following types of technologies: 1) portrait encryption and key generation method: use the attention mechanism and the codec network to precisely encrypt the portrait image, and at the same time, extract the input portrait data The portrait identity feature vector defines the identity characteristics of the encrypted result, so that the encrypted portrait and the input portrait data have similar visual effects; 2) Encrypted portrait and key storage method: according to the principle of who uploads who has the right , after encrypting the actual collected face image, the encrypted portrait is uploaded to the cloud server, and the corresponding unique key is stored in the local server, and the read permission of the key is reserved locally; 3) Portrait decryption method: cloud The server adopts a cooperative processing method to process user applications and local server key authorizat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com