Method for generating physical layer cooperation key when channels in wireless relay network have correlation
A wireless relay network and key generation technology, applied in wireless communication, electrical components, security devices, etc., can solve the problem of not considering the correlation between eavesdroppers and relays, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
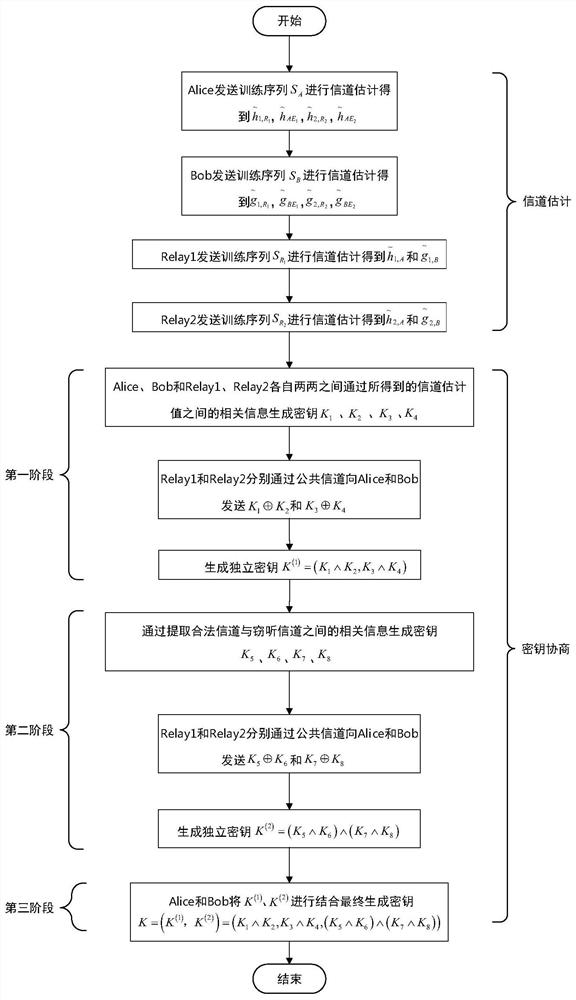
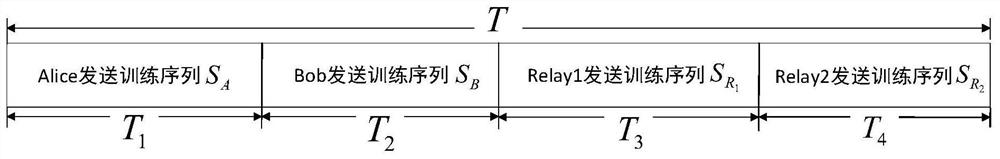
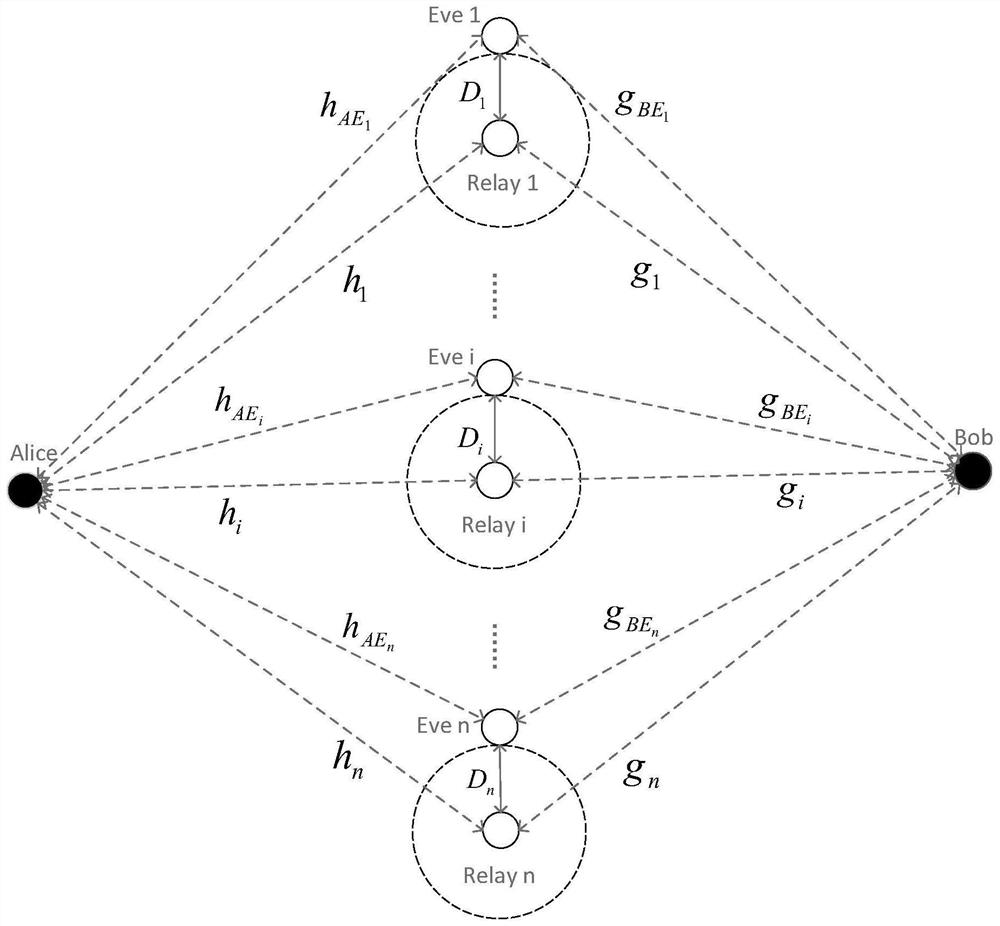
[0019] The relevant eavesdropping channel model considered by the present invention is as figure 1 As shown, the two legal user nodes and each relay node are single-antenna, the distance between Alice and Bob is far away or blocked by obstacles and there is no direct link, so it is necessary to pass through n relay nodes Relay 1(R 1 ), Relay 2(R 2 ),..., Relay n(R n ) to generate keys, but each relay has a radius of D i There is a bug Eve i(E i ), where i=1, 2,...,n, the relay cannot determine the location of the bug but can be sure that the bug must exist. All legal nodes except bugs are limited by half-duplex, they can only receive and send information at different times. The eavesdropper is always in a quiet state, that is, it only receives information without active attack, and the distance between the eavesdropper and the relay is close enough that the eavesdropping channel generated between the legitimate user and each eavesdropper will affect the information betwee...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com