Method for encrypting vehicle defect messages
A defect reporting, vehicle technology, applied in the direction of registration/indication of vehicle operation, instrumentation, registration/indication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
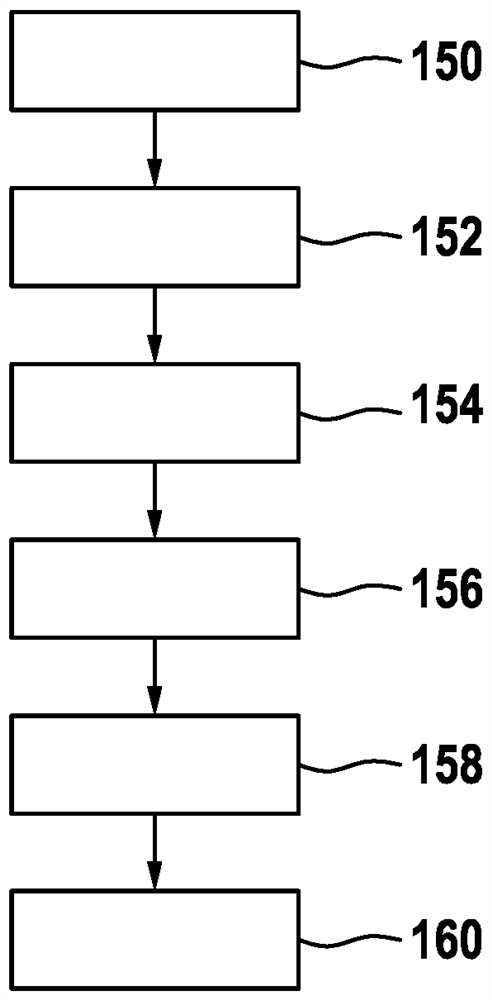
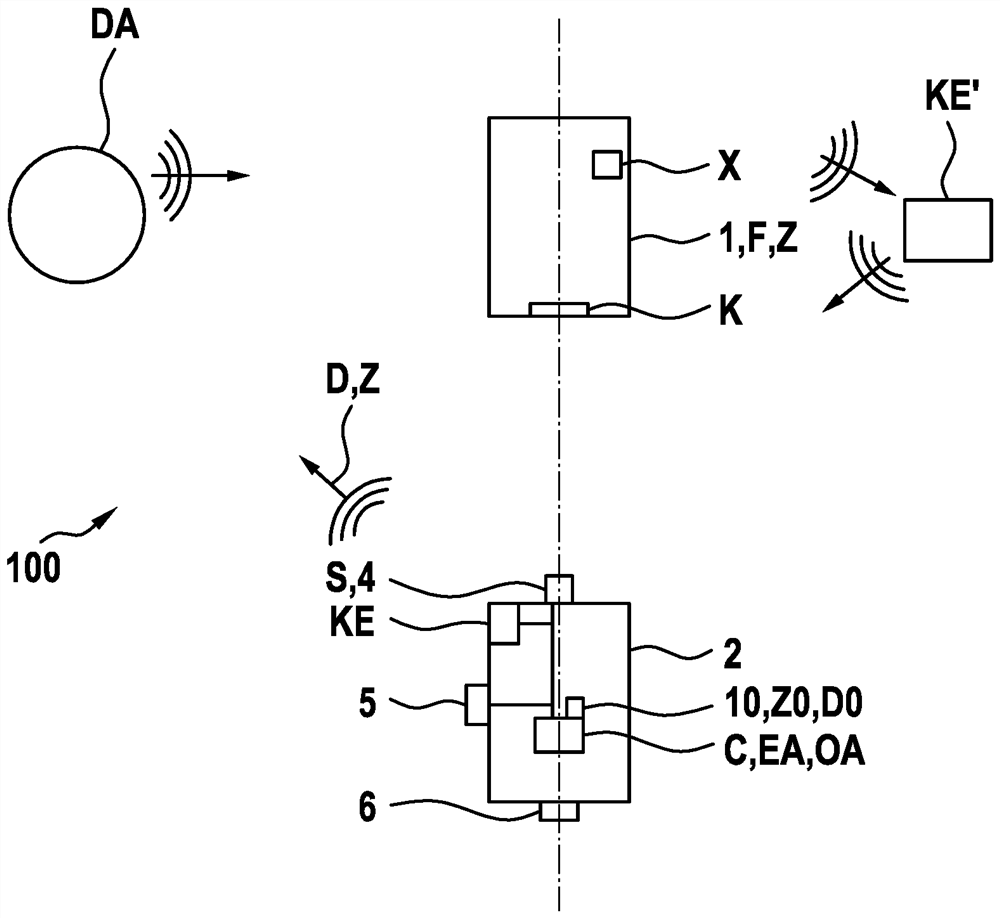
[0064] The invention is shown schematically in the drawing on the basis of an embodiment and will be described in detail later with reference to the drawing. In the figures, identical reference numerals indicate identical or functionally identical elements.
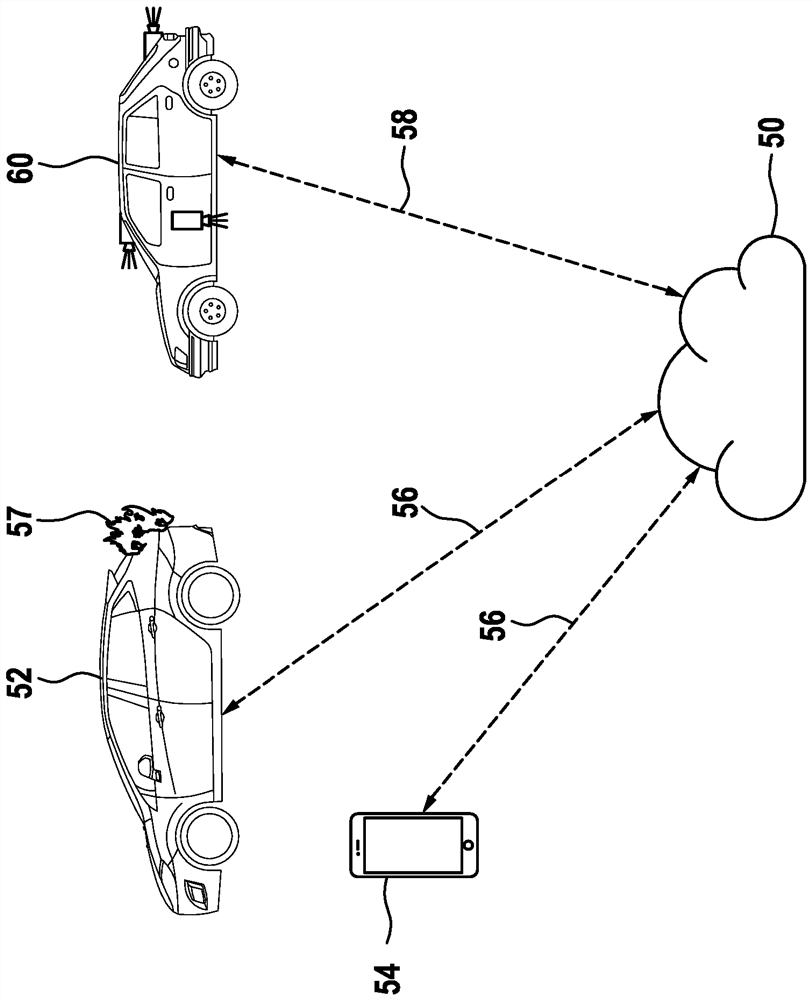
[0065] figure 1 A switching platform 50 is shown, which is connected to a first vehicle 52 or a mobile data device 54 , such as a smartphone, via a car-to-X (Car2X) connection 56 or also via a mobile radio connection. There is also a car-to-X connection 58 with a second vehicle 60 . The second vehicle 60 identifies one or more vehicle defects 57 on the part of the first vehicle 52 and transmits data or information about the defect or about these defects (this is also referred to as diagnostic information) as well as about identifiers, Information such as vehicle identification is sent to the exchange platform 50 . The exchange platform selects a key based on the identifier, which key is distributed to the first vehicle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com