A screen recording method under windows system
A screen and flow technology, applied in the field of network security, can solve the problems of attack behavior analysis deviation, lack of important operation video, high system resource consumption, etc., to achieve complete attack behavior, reduce packet loss rate, and reduce system resource consumption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] According to a specific embodiment of the present invention, the screen recording method under a kind of windows system provided by the present invention comprises the following steps:
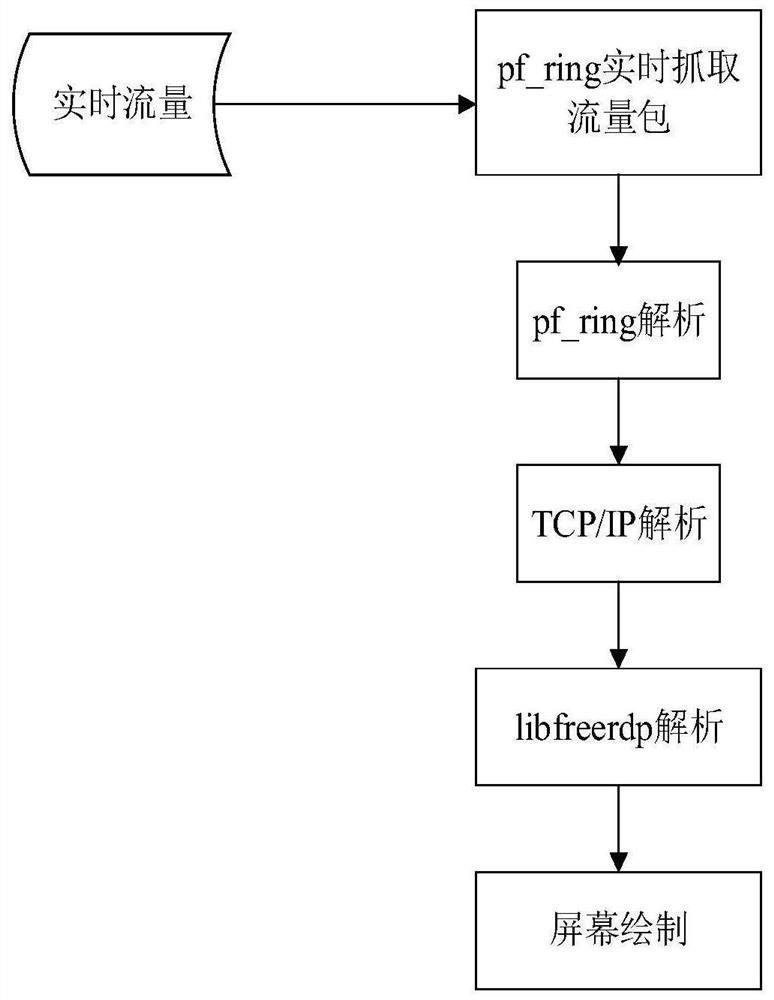
[0079] First deploy rdp replay on the gateway of the monitored windows system host, and install pf_ring on the gateway.
[0080] as attached figure 1 , wherein the windows system host can be used as a honeypot in practical applications. In the present invention, the attack behavior occurs on the honeypot host equipped with the windows system, and the gateway is a Linux system gateway. A gateway is required. Installing pf_ring on the gateway can capture all the data traffic of attacking honeypots in real time, and installing rdp replay on the gateway, that is, parsing the traffic packets captured by pf_ring in real time into rdp data and transmitting it to libfreerdp for screen drawing. The IP address of the gateway and the IP address of the Windows system host can be configured in the...
Embodiment 2
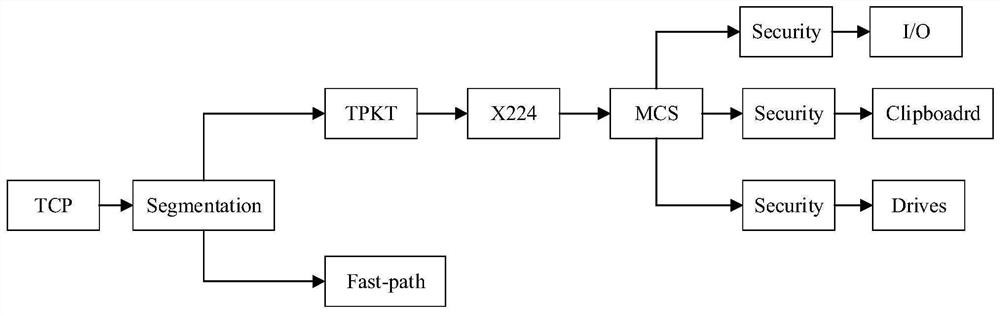
[0095] According to a specific embodiment of the present invention, as attached Figure 4 , when an attacker accesses a honeypot installed with a Windows operating system, he will first initiate a TCP connection establishment request to the honeypot, that is, a handshake TCP message containing the SYN flag bit. After receiving the message, the honeypot will reply with the SYN and The TCP message confirmed by the ACK is sent to the attacker. After receiving the ACK confirmation message, the attacker will reply the confirmation ACK to the honeypot. At this point, the TCP connection is established. The above interactive data will pass through the Linux gateway, and the Linux gateway will record it.
[0096] as attached Figure 5 , when the client attacks the windows system host, it is first connected to the windows system host by the above-mentioned TCP connection request through the remote desktop operation. At this time, the Linux gateway first opens the pf_ring by setting pfr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com