Network endpoint slicing method and system based on Kubernetes container
A network and endpoint technology, applied in the field of operation control of software applications, can solve problems such as performance degradation, inability to efficiently read/update a single endpoint, etc., and achieve the effects of improving performance, improving scalability, and reducing traffic load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
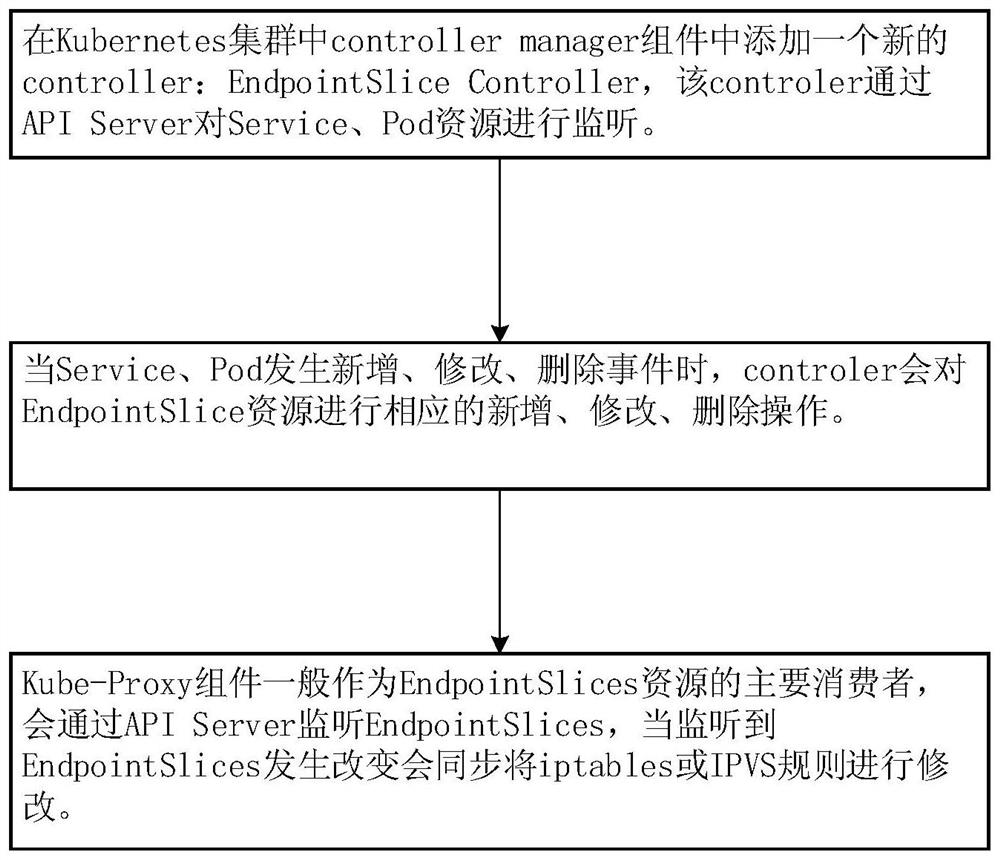
[0028] Such as figure 1 and figure 2 As shown, a method for slicing network endpoints based on Kubernetes containers in this embodiment, the Kubernetes cluster loads and runs several modules, and the corresponding relationship between the new EndpointSlice resource and other resources and some restrictions are as follows:
[0029] 1. A service can be mapped to N endpoint slices.
[0030] 2. An endpoint slice contains a maximum of 100 network endpoints (endpoints) by default, and the maximum number can be modified through the configuration in the controllermanager.
[0031] 3. The number of endpoint slice resources is also limited by the resource quota of the namespace, which can protect the Kubernetes control plane and prevent malicious users from attacking the APIServer by creating a service that selects all container groups.
[0032] The method of network endpoint slicing includes the following:
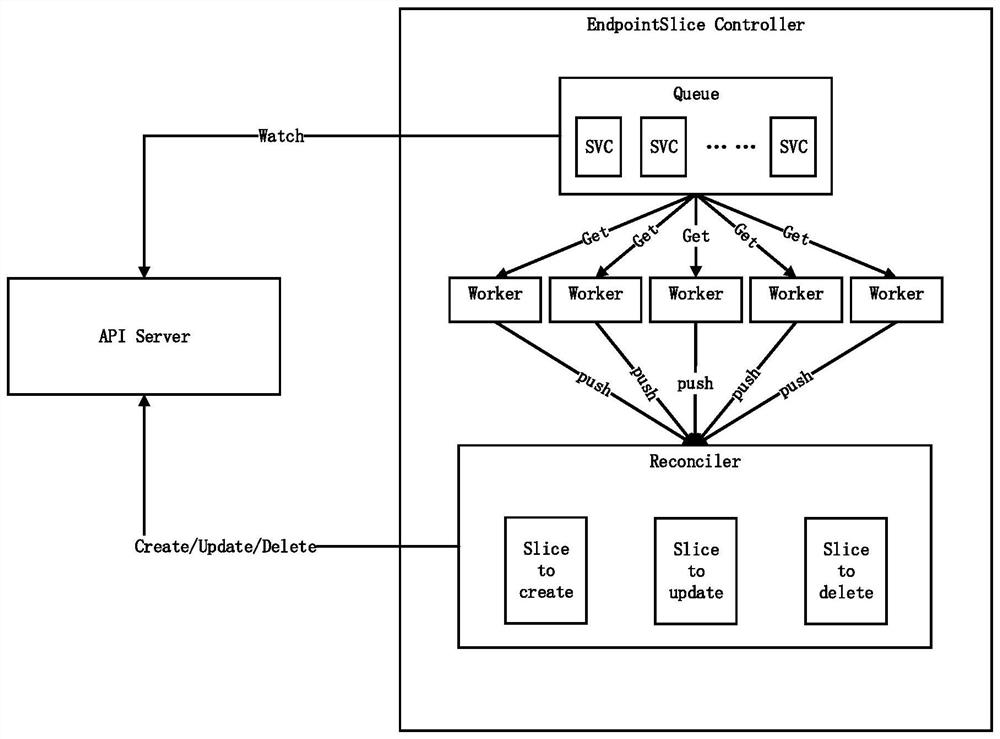
[0033] Step S1, an EndpointSliceController is configured in the controller...
Embodiment 2
[0056] Based on the above-mentioned embodiment 1, a system for slicing network endpoints based on Kubernetes containers in this embodiment will be described below. For detailed description and other examples, please refer to the description of the above-mentioned embodiment 1.
[0057] A system for slicing network endpoints based on Kubernetes containers in this embodiment includes the following content:
[0058] Configuration module: used to configure an EndpointSlice Controller in the controller manager component of the Kubernetes cluster. When the EndpointSlice Controller starts, it monitors Service and Pod resources through the API Server;
[0059] Monitoring operation module: used for EndpointSlice Controller to monitor the occurrence of new, modified or deleted events of Service or Pod, and perform corresponding new, modified or deleted operations on EndpointSlice resources;
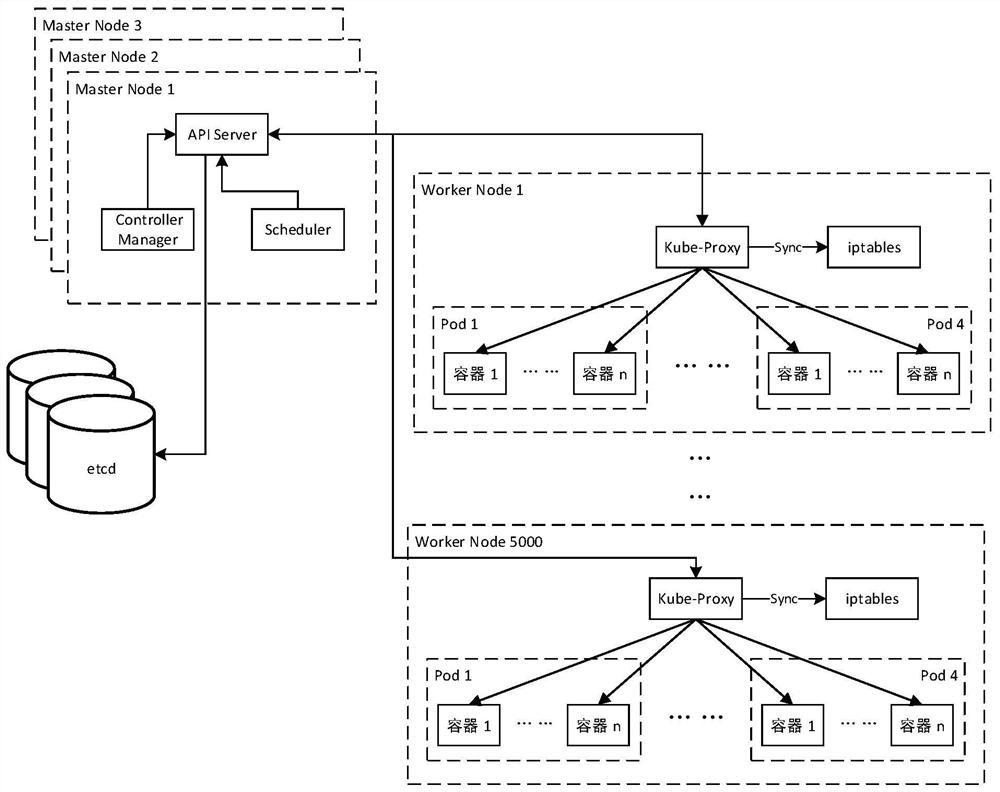
[0060] Update rule module: It is used for the Kube-Proxy component to monitor the addition, mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com