Method for realizing fingerprint card and fingerprint card
A fingerprint card and fingerprint technology, which is applied in the field of fingerprint cards and fingerprint cards, can solve the problems of easy peeping of PIN codes, cardholder information security risks, leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
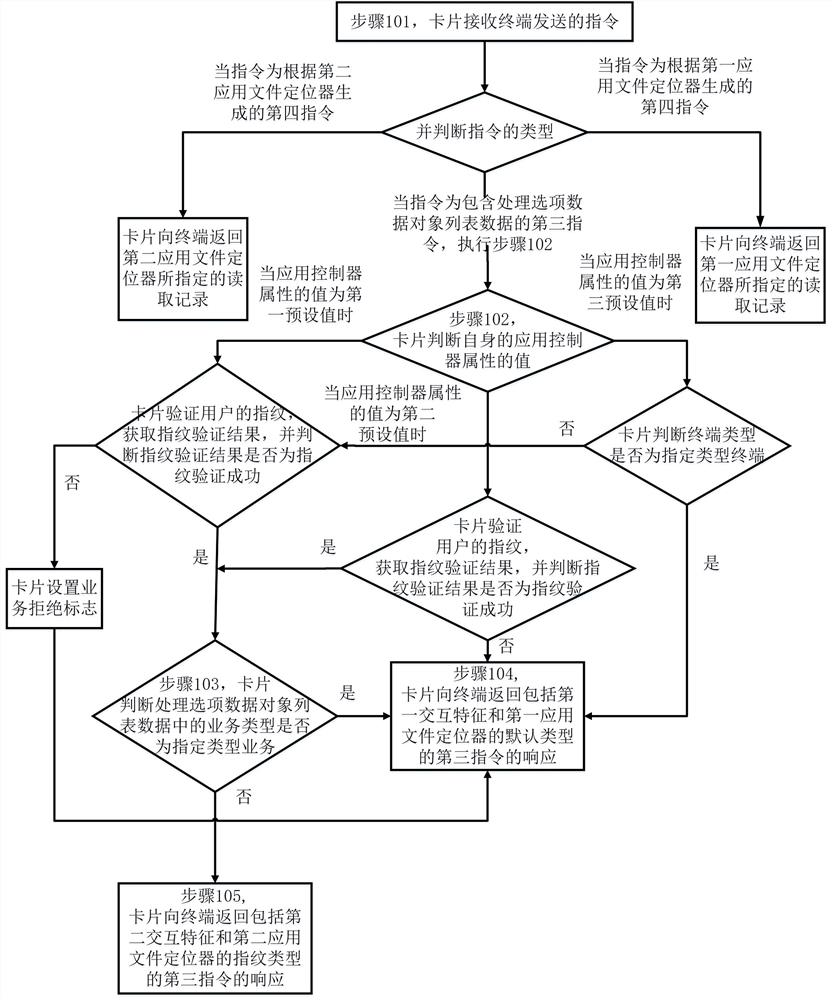
[0037] This embodiment provides a method for implementing a fingerprint card, such as figure 1 As shown, the method specifically includes:
[0038] Step 101, the card receives the instruction sent by the terminal, and judges the type of the instruction, and when the instruction is the third instruction including processing option data object list data, execute step 102;
[0039] Step 102, the card judges the value of its own application controller attribute,
[0040] When the value of the application controller attribute is the first preset value, the card verifies the user's fingerprint, obtains the fingerprint verification result, and judges whether the fingerprint verification result is a fingerprint verification success, if yes, execute step 103, if not, then the card setting Service rejection flag, go to step 104;
[0041] When the value of the application controller attribute is the second preset value, the card verifies the user's fingerprint, obtains the fingerprint ...
Embodiment 2
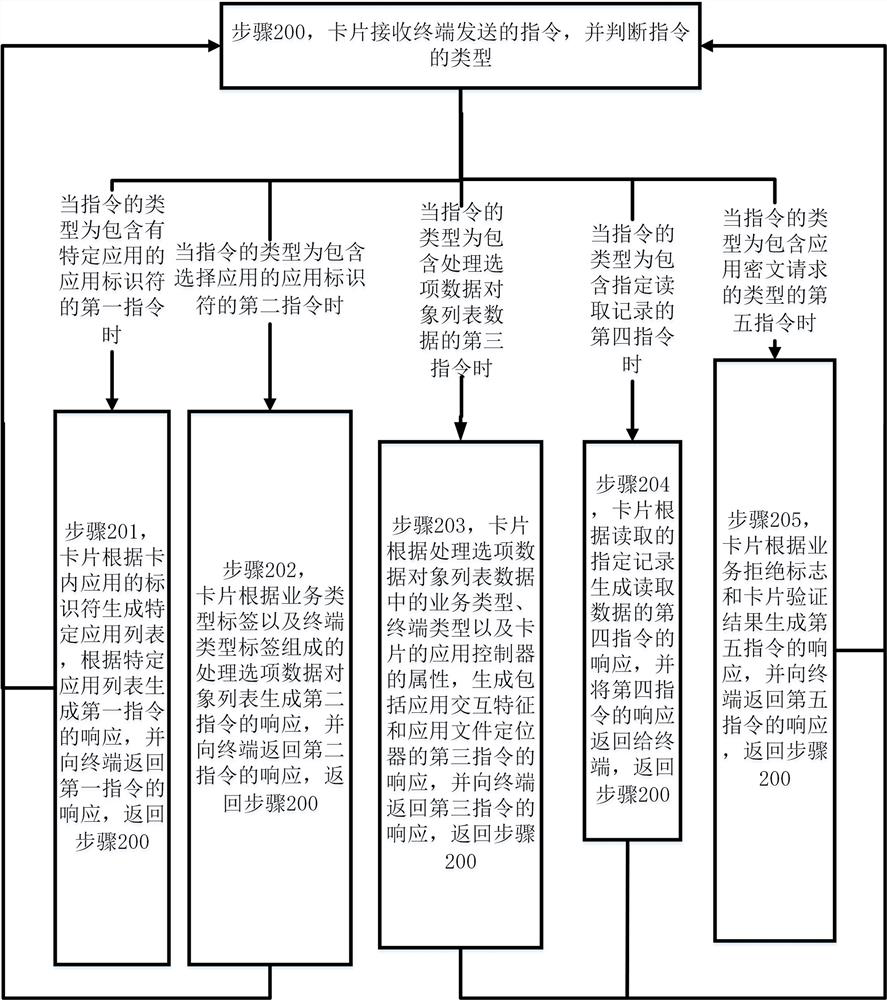
[0061] This embodiment provides a method for implementing a fingerprint card, such as figure 2 As shown, it specifically includes the following steps:
[0062] In step 200, the card receives the instruction sent by the terminal, and judges the type of the instruction. When the type of the instruction is the first instruction containing the application identifier of a specific application, perform step 201; when the type of the instruction is the application identifier containing the selected application when the type of the instruction is the third instruction containing the processing option data object list data, execute step 203; when the type of the instruction is the fourth instruction containing the specified read record, execute Step 204; when the type of the instruction is the fifth instruction including the type of application ciphertext request, execute step 205;
[0063] Step 201, the card generates a specific application list according to the identifier of the ap...
Embodiment 3
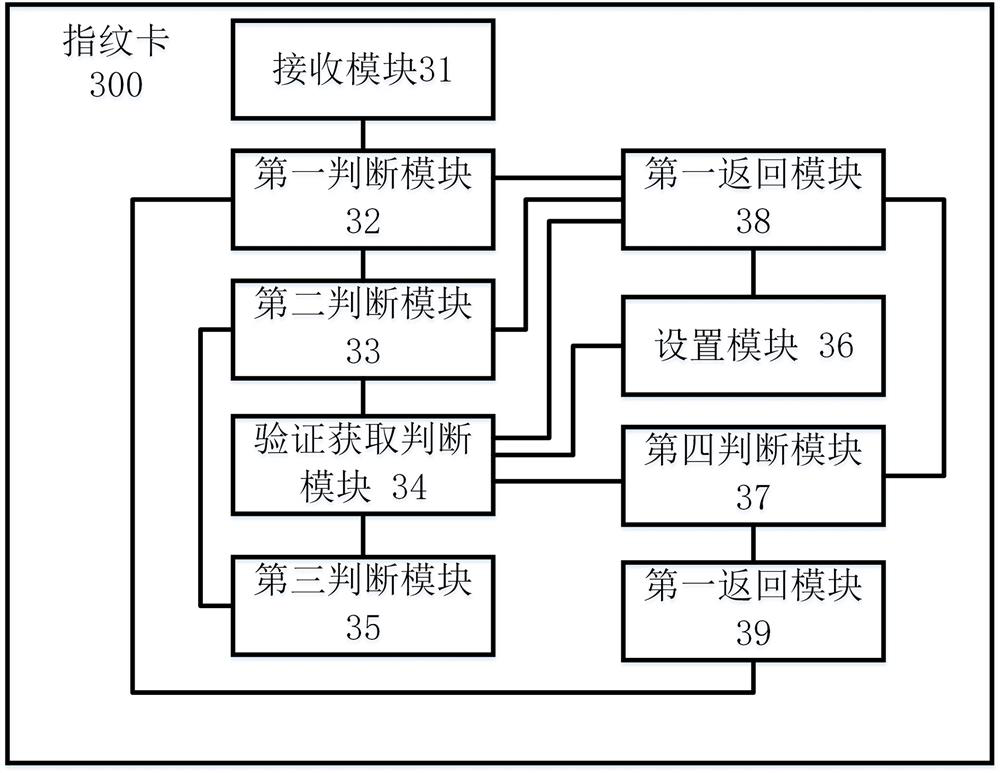
[0174] This embodiment provides a fingerprint card 300, such as image 3 shown, including:
[0175] A receiving module 31, configured to receive an instruction sent by the terminal;
[0176] The first judging module 32 is used to judge the type of instruction received by the receiving module 31;
[0177] The second judging module 33 is used for judging the value of the application controller property of the fingerprint card itself when the type of the first judging module 32 judging instruction is the third instruction including processing option data object list data;
[0178] Verification and acquisition judgment module 34, used for when the second judgment module 33 judges that the value of the application controller attribute of the fingerprint card itself is the first preset value, verify the user's fingerprint, obtain the fingerprint verification result, and judge whether the fingerprint verification result is Fingerprint verification is successful;
[0179] It is als...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com