Image authenticity identification method
An image and authenticity technology, which is applied in the field of identification of deep fake images, can solve problems that rarely involve the identification of real and fake faces in intelligent directions, and achieve the effect of improving speed and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
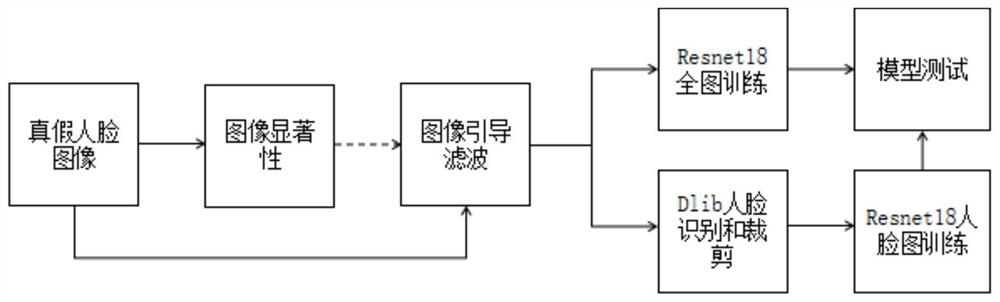
[0029] In order to make the technical solution of the present invention clearer, the present invention will be further elaborated below in conjunction with the accompanying drawings. The invention according to figure 1 The steps shown are implemented in detail:
[0030] The first step is to visualize the texture difference between real and fake images.
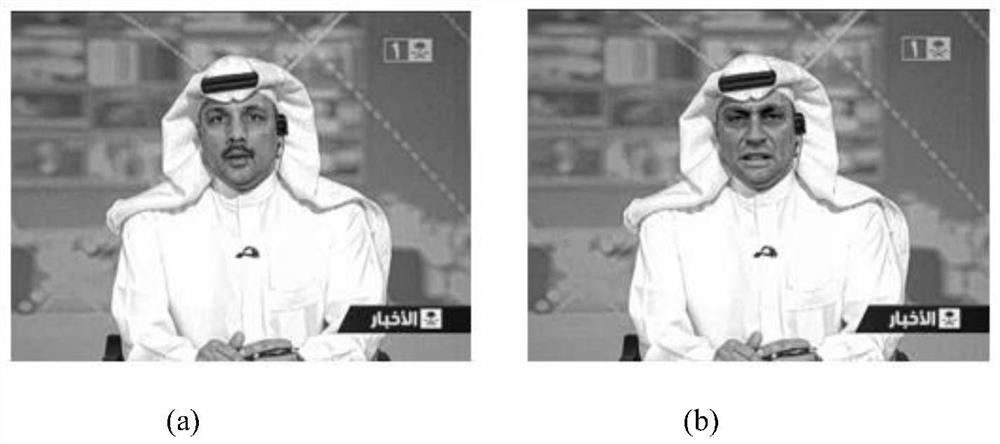
[0031] The image saliency method is used to process a large number of real face images and fake face images respectively, and the two types of face images are visualized to reveal the potential texture differences of face regions. In order to better grasp the texture information of the input image, the present invention uses superpixels as the minimum processing unit.
[0032] (3) Segment the original image through the simple linear iterative clustering (SLIC) algorithm to obtain superpixels, and calculate the contrast between each superpixel and the edge superpixels to obtain a salient image based on the background.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com