Regular sharing method and system for alliance chain encrypted data
A technology for encrypting data and alliances, applied in the field of alliance chains
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
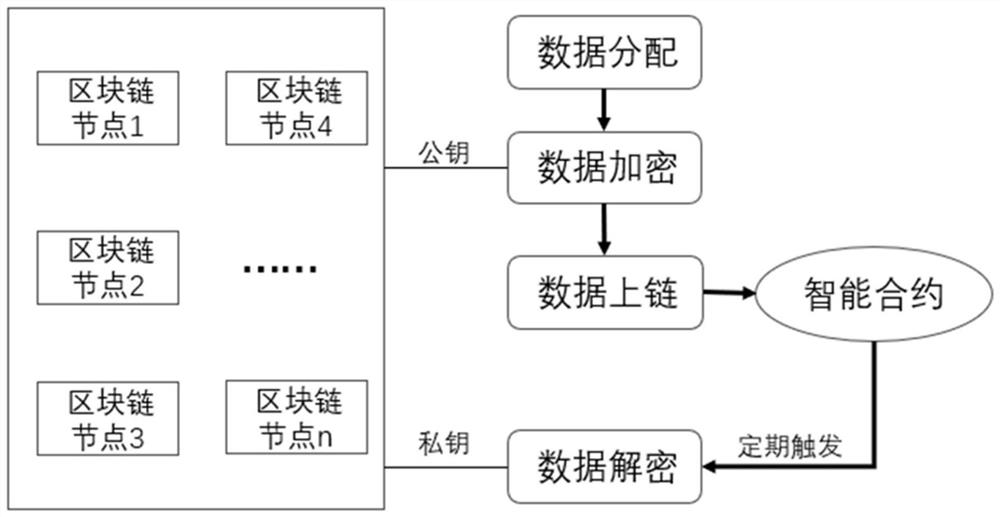
[0020] This embodiment discloses a method for regularly sharing encrypted data of an alliance chain, including the following steps:
[0021] Divide alliance chain nodes into alliance nodes and ordinary user nodes, and set the level of ordinary user nodes. The initial level of an ordinary user node is level 1, and the highest level is level 5. The number of times an ordinary user node completes a smart contract task exceeds the predetermined number, and the level increases by 1 level.
[0022] S1 k-level task users regularly publish tasks through ordinary user nodes. If the level k is greater than or equal to the set level corresponding to the task, the task user will be assigned public keys corresponding to 3k different ordinary user nodes.
[0023] The S2 task user encrypts and signs the complete data content, randomly scrambles the complete data, divides it into 3k parts, and sends them to 3k different ordinary users, and the 3k different ordinary users encrypt and sign the ...
Embodiment 2
[0039] Based on the same inventive concept, this embodiment discloses a regular sharing system for alliance chain encrypted data, including:
[0040] The data allocation module is used to make task users of level k regularly disclose tasks through ordinary user nodes. If the level k is greater than or equal to the set level corresponding to the task, assign public keys corresponding to 3k different ordinary user nodes to task users;
[0041]The data encryption module is used to enable the task user to encrypt and sign the complete data content, and randomly scramble the complete data, divide it into 3k parts, and send them to 3k different ordinary users, and the 3k different ordinary users will distribute them to encrypted and signed data;
[0042] The smart contract module is used to send all the encrypted data information in step S3 to the smart contract, and the task user sets the trigger time;
[0043] The decryption output module is used to regularly check whether the tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com