Privacy protection method for credit investigation system based on block chain
A privacy protection and blockchain technology, applied in the field of credit data security, can solve problems such as identity information leakage, achieve the effects of high efficiency of secure storage, short consumption time, and guarantee confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
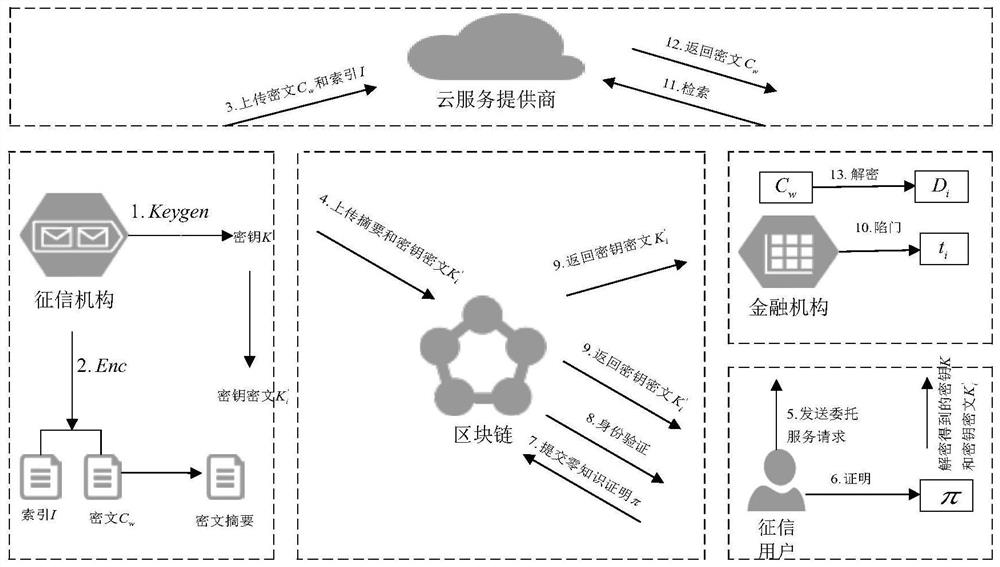
[0036] Such as figure 1 As shown, the embodiment of the present invention provides a privacy protection method for a blockchain-based credit reporting system, including five entities: credit reporting users, financial institutions, credit reporting agencies, blockchain, and cloud service providers;
[0037] Credit Reporting Agencies: The present invention assumes that credit reporting agencies are trusted. The credit reporting agency CI has a large number of user credit reporting reports, and can securely own, control and conditionally provide the personal credit reporting information of credit reporting users, and obtain relevant fees in the process.
[0038] Credit reporting users: credit reporting users are typical data consumers. They need to pass identity authentication and entrust financial institutions to inquire about relevant credit information.
[0039] Blockchain: The smart contract in the blockchain BC can verify the identity of credit reporting users, and the bl...
Embodiment 2
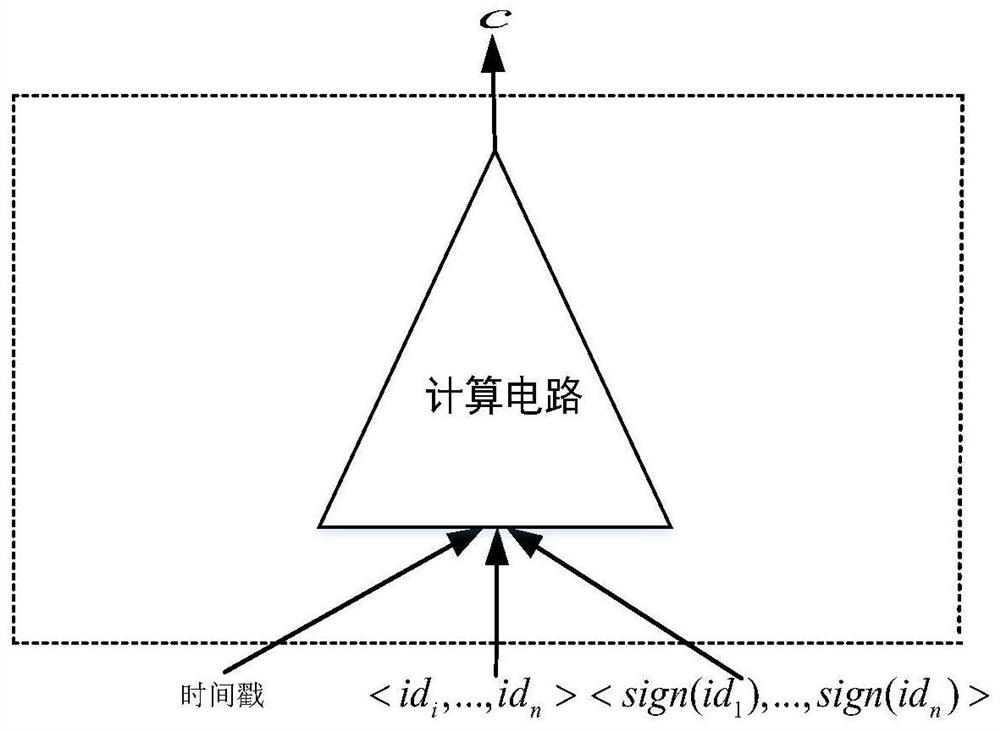
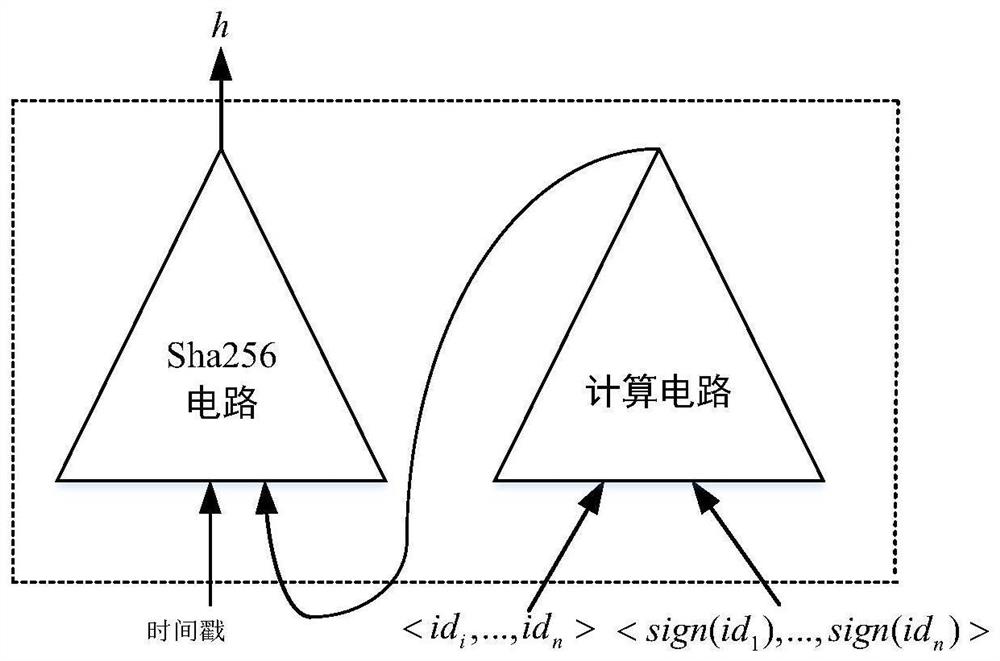
[0054] The following is the credit user u i As an example, the privacy protection method of the credit reporting system based on the blockchain of the present invention will be described in detail. This solution is based on technologies such as blockchain, smart contracts, searchable symmetric encryption technology, and zero-knowledge proof zkSNARKs to realize credit reporting in the credit reporting system. User identity authentication and secure sharing of credit information data. The method comprises the steps of:
[0055] Step 1 System initialization
[0056] Step 1.1: Initialize and generate p, G p ; Among them, p is a large prime number, G p yes the only subgroup of
[0057] Step 1.2: Select generator g∈G p ,random number Security parameter λ and hash function
[0058] Step 1.3: Set credit reference user u i The public key is PK i , the private key is SK i ;
[0059] Step 1.4: The credit bureau CI selects the security parameter k, and uses the probabilist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com