Face recognition method and device capable of protecting privacy
A technology to protect privacy and face recognition, applied in the computer field, can solve the problem of inability to access cloud servers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029]The following describes the solutions provided in this specification with reference to the drawings.
[0030]Before describing the solution provided in this specification, the following description of the inventive concept of this solution is provided:
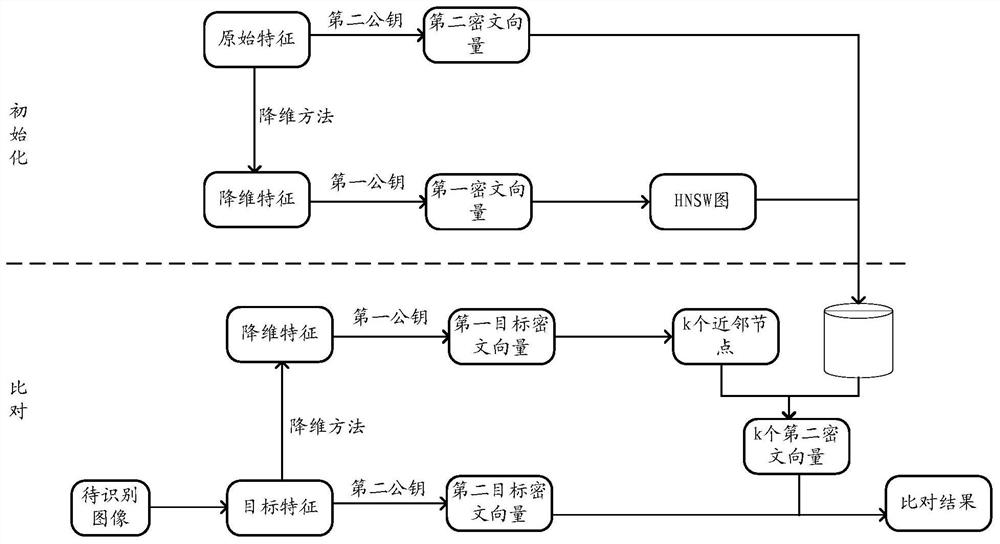
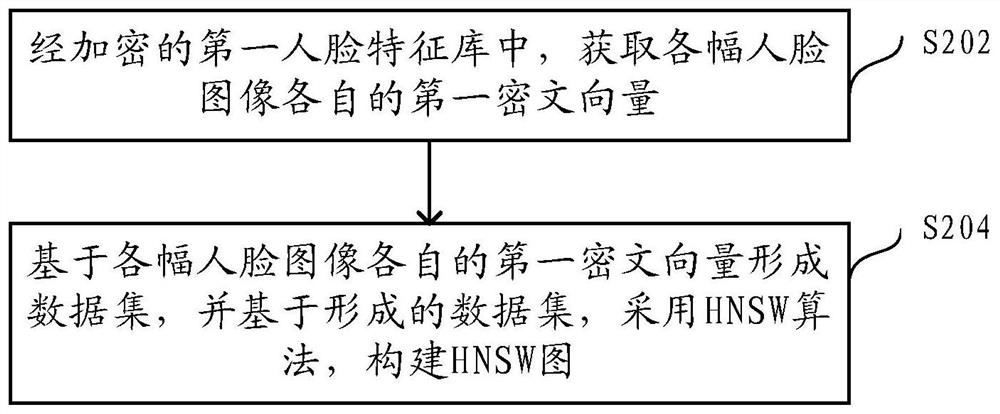
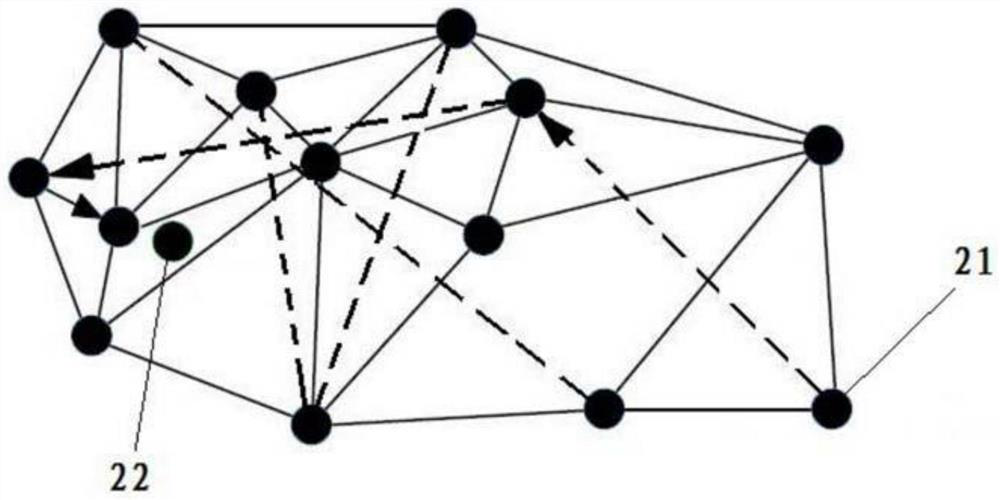
[0031]As mentioned earlier, current face recognition methods are generally not suitable for offline scenarios or weak network environments. In order to improve the universal applicability of the face recognition method, the inventor of this application proposes that the terminal alone executes a complete face recognition solution. That is, after the face image is collected on the terminal, the terminal extracts features from the collected face image, and compares the extracted features with the features of each face image in the face feature library (hereinafter referred to as face features) . The terminal here may be, for example, a mobile phone, a tablet computer, a personal computer, a wearable device, etc.
[0032]It should be unde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com