Electronic cigarette cartridge authentication method and device and electronic cigarette
An authentication method and pod technology, applied in tobacco and other directions, can solve the problems of unguaranteed security and high cost of authentication methods, and achieve the effects of high cost, low hardware resource consumption, and improved security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
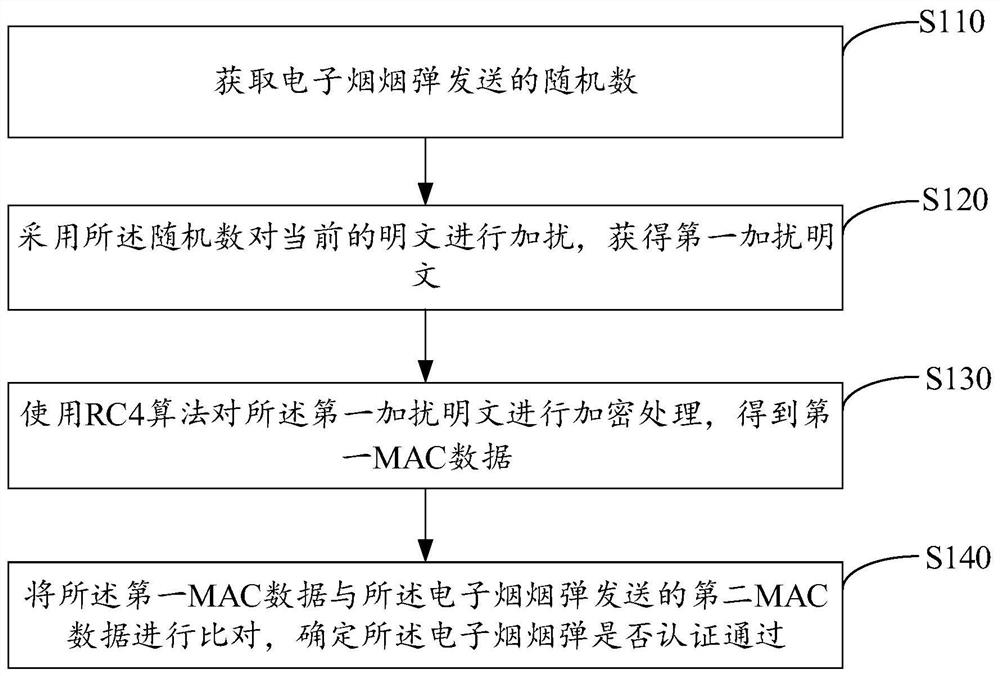
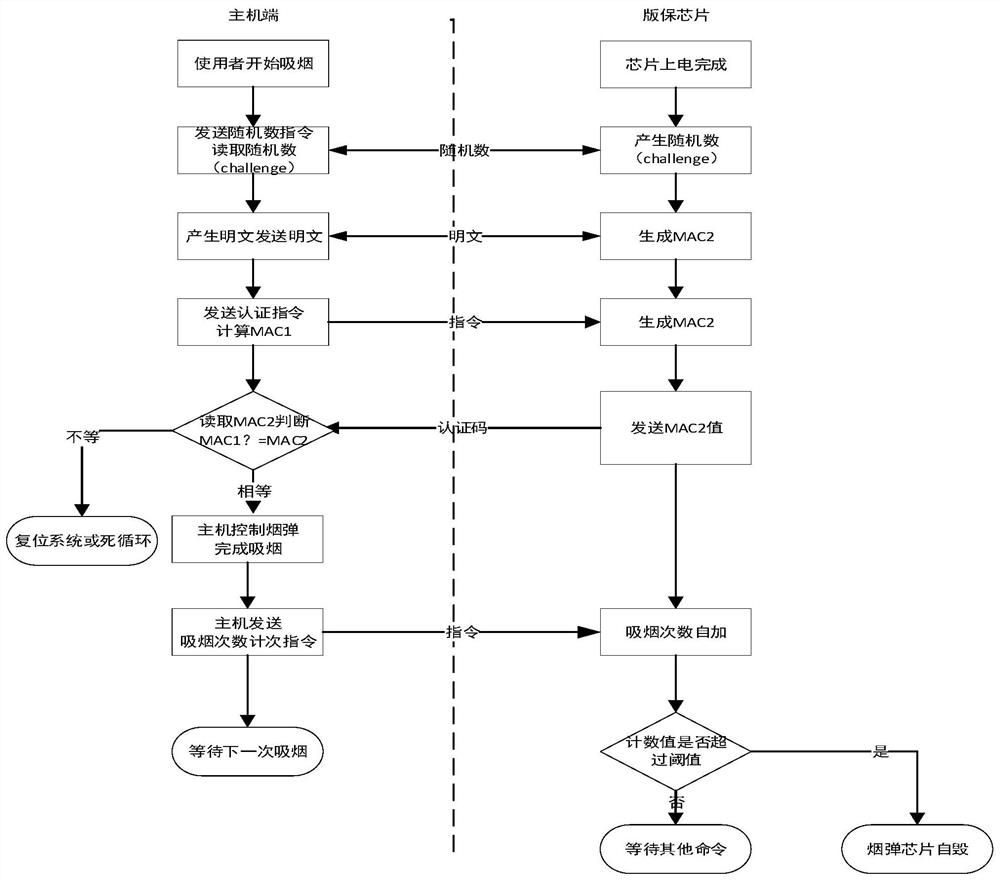
[0044] figure 1 It is a flow chart of realizing the authentication method of the electronic cigarette pod shown in the second embodiment. The authentication method for electronic cigarette cartridges shown in Embodiment 1 is applicable to electronic cigarette cartridges, for example, placed in the MCU of the electronic cigarette stick. For ease of description, only the parts related to the embodiments of the present invention are shown, and the details are as follows:
[0045] Step S110, obtaining the random number sent by the electronic cigarette pod.
[0046] Step S120, using the random number to scramble the current plaintext to obtain a first scrambled plaintext.
[0047] Step S130, using the RC4 algorithm to encrypt the first scrambled plaintext to obtain first MAC data.
[0048] Step S140, comparing the first MAC data with the second MAC data sent by the electronic cigarette cartridge to determine whether the electronic cigarette cartridge is authenticated.
[0049] ...
Embodiment 2
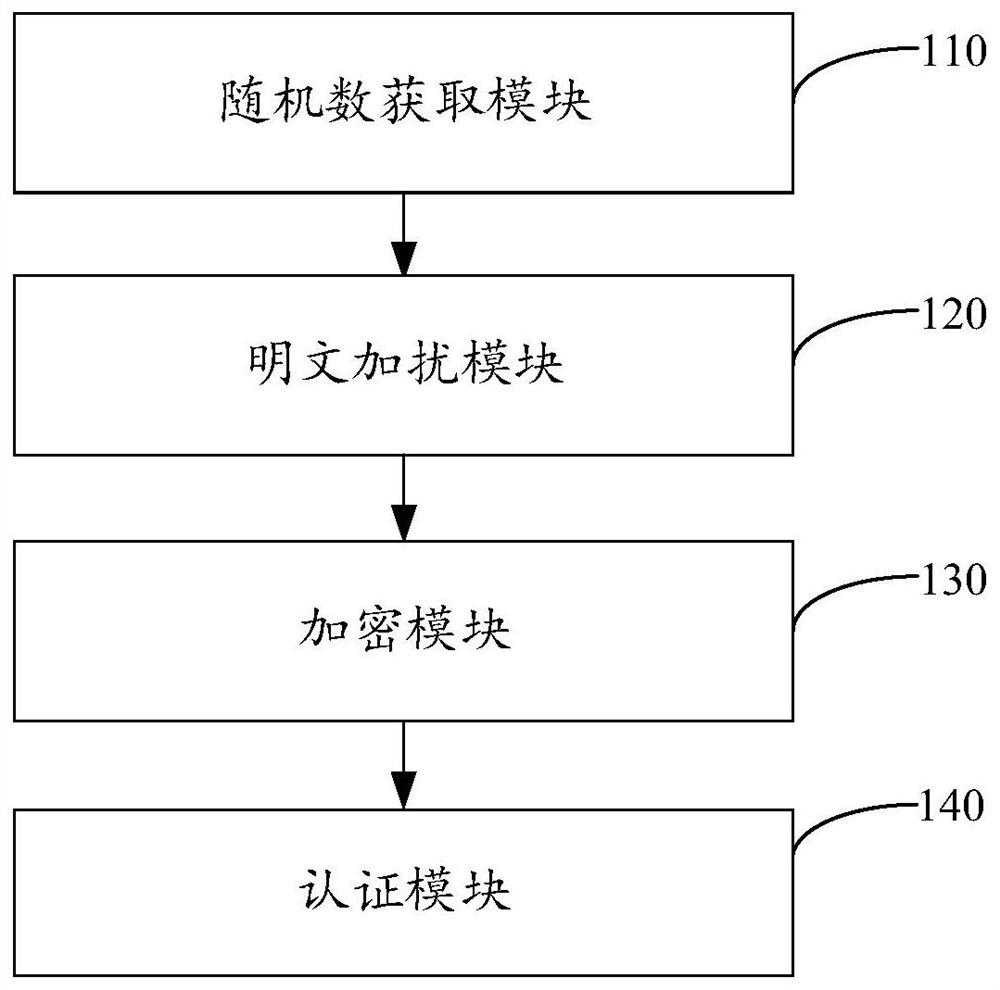
[0066] image 3 It shows a block diagram of the authentication device of the electronic cigarette pod provided by the second embodiment of the present invention. For the convenience of description, only the parts related to the embodiment of the present invention are shown, including:
[0067] A random number acquisition module 110, configured to acquire the random number sent by the electronic cigarette pod;
[0068] A plaintext scrambling module 120, configured to use the random number to scramble the current plaintext to obtain a first scrambled plaintext;
[0069] An encryption module 130, configured to encrypt the first scrambled plaintext using the RC4 algorithm to obtain first MAC data;
[0070] The authentication module 140 is configured to compare the first MAC data with the second MAC data sent by the electronic cigarette cartridge, and determine whether the electronic cigarette cartridge is authenticated.
[0071] In the embodiment of the present invention, each m...
Embodiment 3
[0073] Embodiment 3 provides an electronic cigarette, which performs all or part of the steps shown in Embodiment 1 above. The e-cigarette includes:
[0074] at least one processor; and
[0075] a memory communicatively coupled to the at least one processor; wherein,
[0076] The memory stores instructions executable by the at least one processor, and the instructions are executed by the at least one processor, so that the at least one processor can execute the method described in any of the above exemplary embodiments. method.
[0077] The specific manner in which the processor in the device in this embodiment performs operations has been described in detail in the embodiment of the authentication method for the e-cigarette cartridge, and will not be described in detail here.
[0078] Optionally, in this embodiment, a storage medium is also provided. The storage medium is a computer-readable storage medium, for example, a temporary or non-transitory computer-readable stora...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com