Visual malicious software detection device and method based on deep neural network
A deep neural network and malware technology, applied in the field of visual malware detection devices, can solve problems such as inability to expand data sets, loss of operational capabilities, difficult and unknown samples, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0112] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
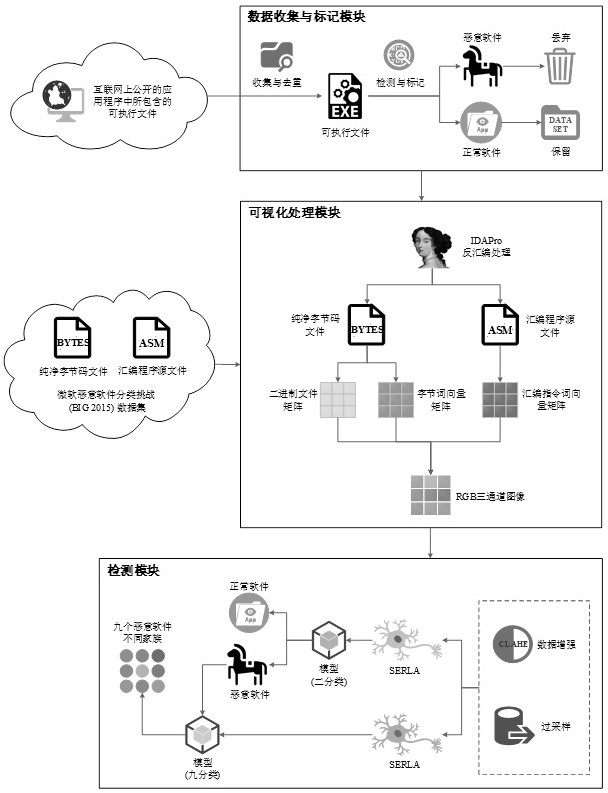
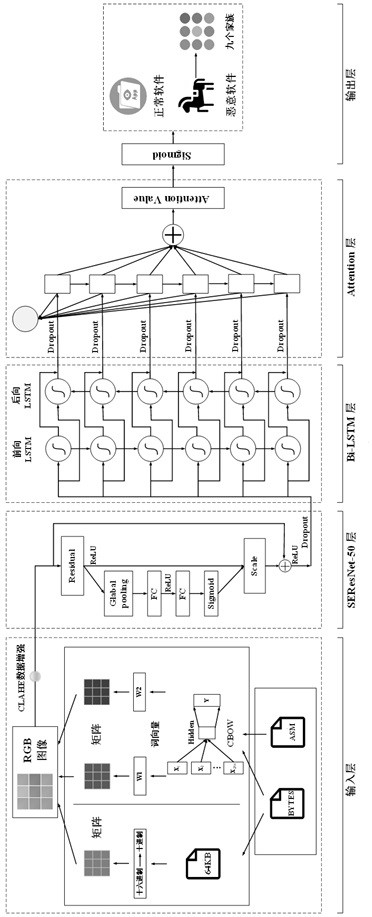
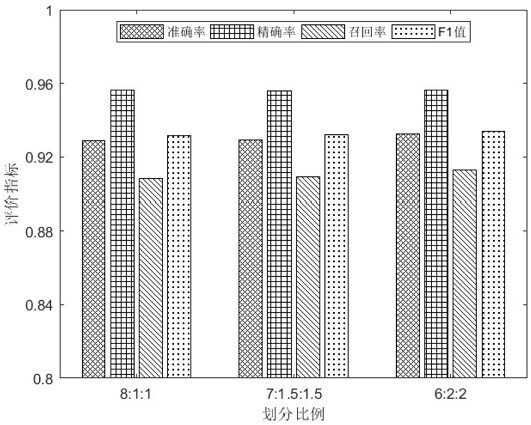
[0113] The present invention proposes a novel malware detection and classification device based on a deep neural network. Using disassembly technology to convert executable file samples into bytes files and asm files, using this method, the collected and marked normal software data set and the famous BIG 2015 malware data set were combined to obtain a balanced experimental data set. In order to effectively extract the high-dimensional features in the data samples, the visualization technology combined with data enhancement is used to further convert the samples into RGB three-channel images. A unique deep neural network classification architecture called SERLA (SEResNet50 + Bi-LSTM + Attention) is also proposed to improve the performance of detection methods. The model performance evaluation results show that the method of the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com