Intelligent lock system
A lock and intelligent technology, applied in the field of locks, can solve the problems of difficulty in prevention, difficulty in guaranteeing, and accountability of employees, and achieve the effect of ensuring safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
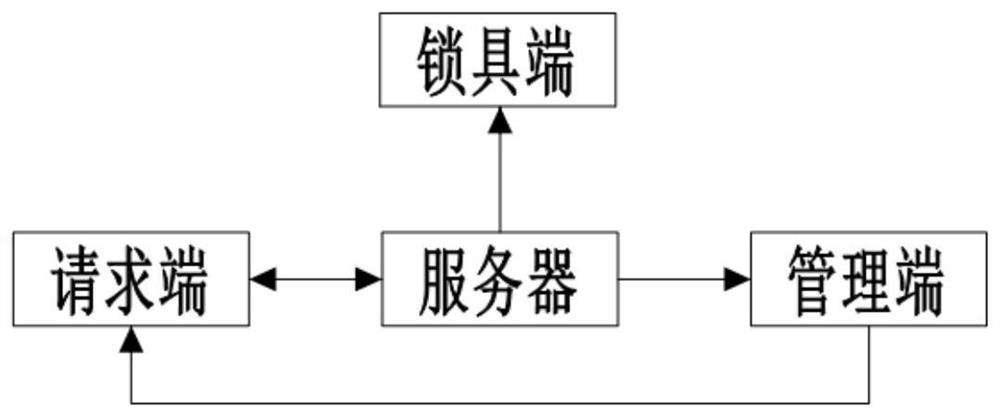
[0040] Such as figure 1 As shown, an intelligent lock system includes a lock end, a request end, a management end and a server. In this embodiment, the server is a Tencent Cloud server, the lock end is an electronic smart lock, and the lock end communicates with the server through broadband. communicate with the server.
[0041] The requesting end is used to send a door opening request to the server, and the door opening request includes the requester and the reason for the request.
[0042] The server is used to send a verification signal to the requesting end after receiving the door opening request; the requesting end is also used to send verification information to the server after receiving the verification signal. The verification information is fingerprint, finger vein or facial information. In this embodiment, the verification information is a fingerprint.
[0043] The server is also used to update the current password on the lock end after the verification informa...
Embodiment 2
[0051] Different from Embodiment 1, in this embodiment, the management terminal is also used for door opening authority management. In this way, the management personnel can manage the door opening authority of the personnel through the management terminal.
[0052]In addition, in this embodiment, the requesting end is also used for positioning; after the requesting end is verified, the server is also used to obtain the positioning information of the requesting end, and the coordinates of the lock end are pre-stored in the server. When the distance between the requesting end and the lock end is less than the preset When the distance, the server sends the first password to the requesting end. Through such a setting, the applicant can reduce the risk of losing the request end after obtaining the current password, resulting in the leakage of the current password.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com