Industrial control system attack clue discovery system based on knowledge graph
A technology of knowledge graph and industrial control system, applied in the field of industrial control system attack clue discovery system, which can solve problems such as only detecting attacks and alarming, security incidents, inability to provide methods and consequences of attacks and handling opinions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
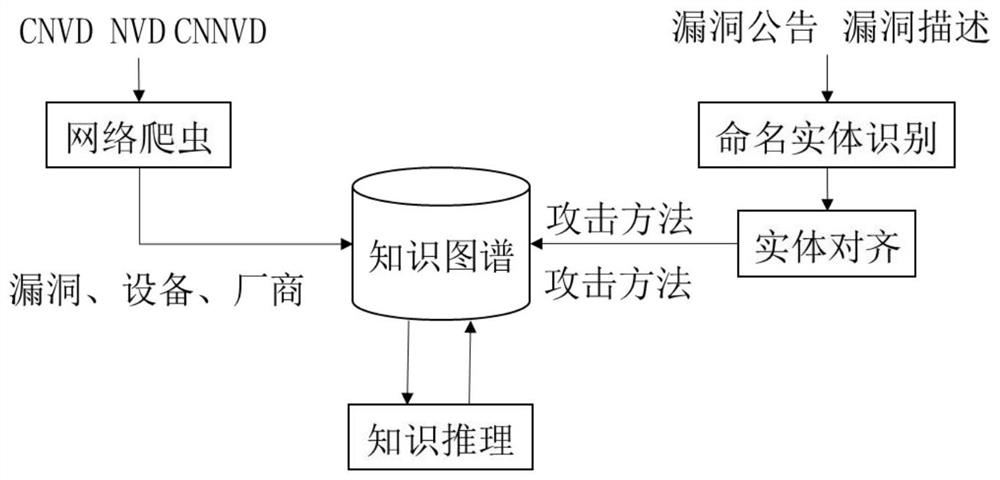
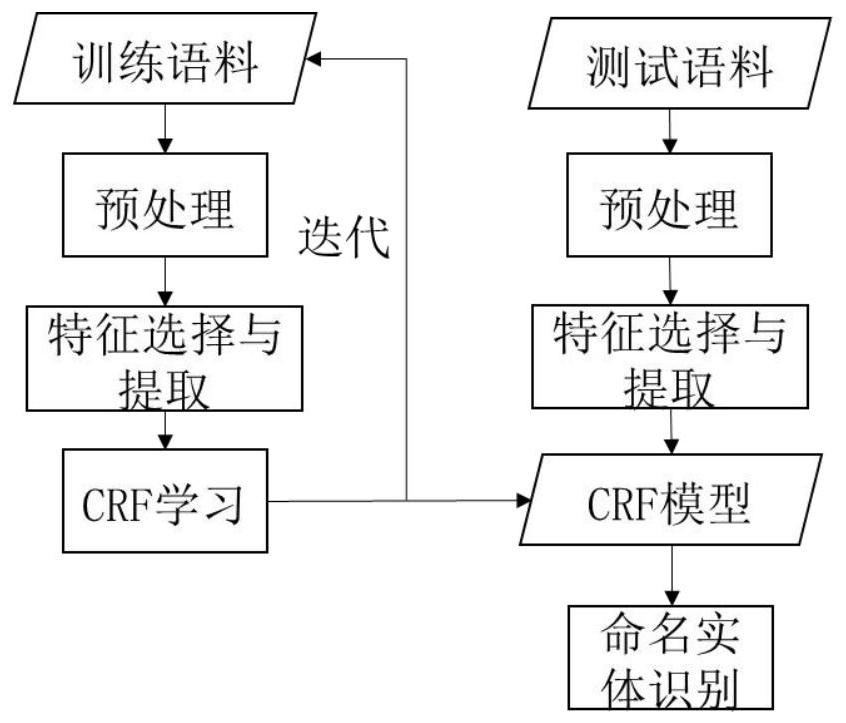
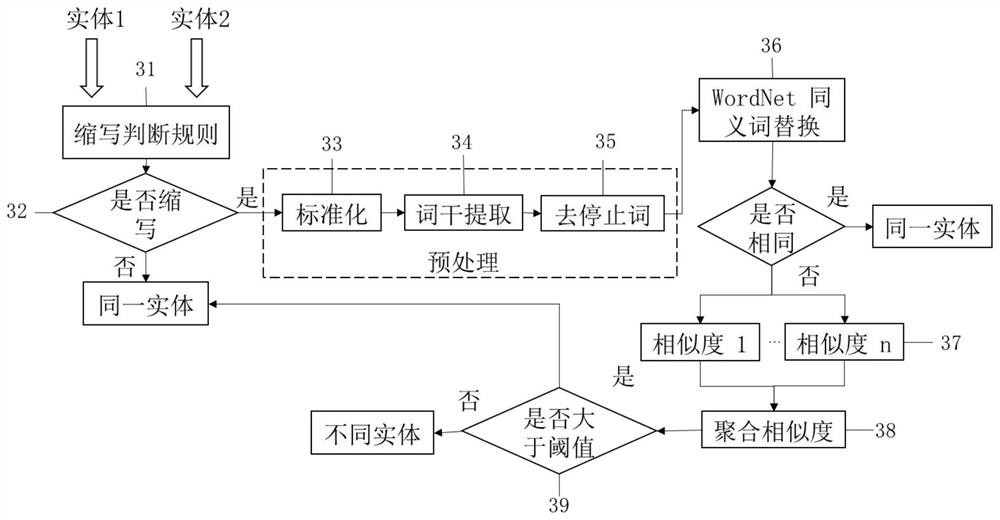
[0023] figure 1 is the overall structure diagram of the knowledge map construction of the present invention, such as figure 1 As shown, in order to obtain device information, vulnerability and manufacturer information, web crawlers are used to obtain and parse the web page information of each vulnerability database, and after merging and deduplication to form the knowledge graph of device, vulnerability and manufacturer entities, including vulnerability name, release date, threat level, Attributes such as CVE number, description, vulnerability patch, vulnerability type, and vulnerability reference. For unstructured vulnerability announcements and vulnerability descriptions, etc., use the named entity recognition extraction method and attack consequences based on linear chain conditional random fields. Entities extracted from multiple d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com