Message sending method and device, message receiving method and device and equipment
A message sending and message receiving technology, applied in the field of Internet of Vehicles, can solve the problems of ASN.1 encoders such as inability to encode, wrong encoding, and transmission failure, and achieve the effects of reducing data transmission failure, improving security, and accurate encoding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
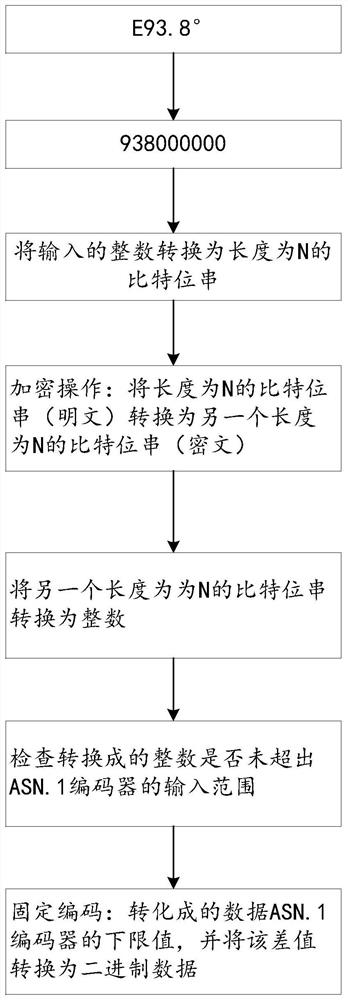
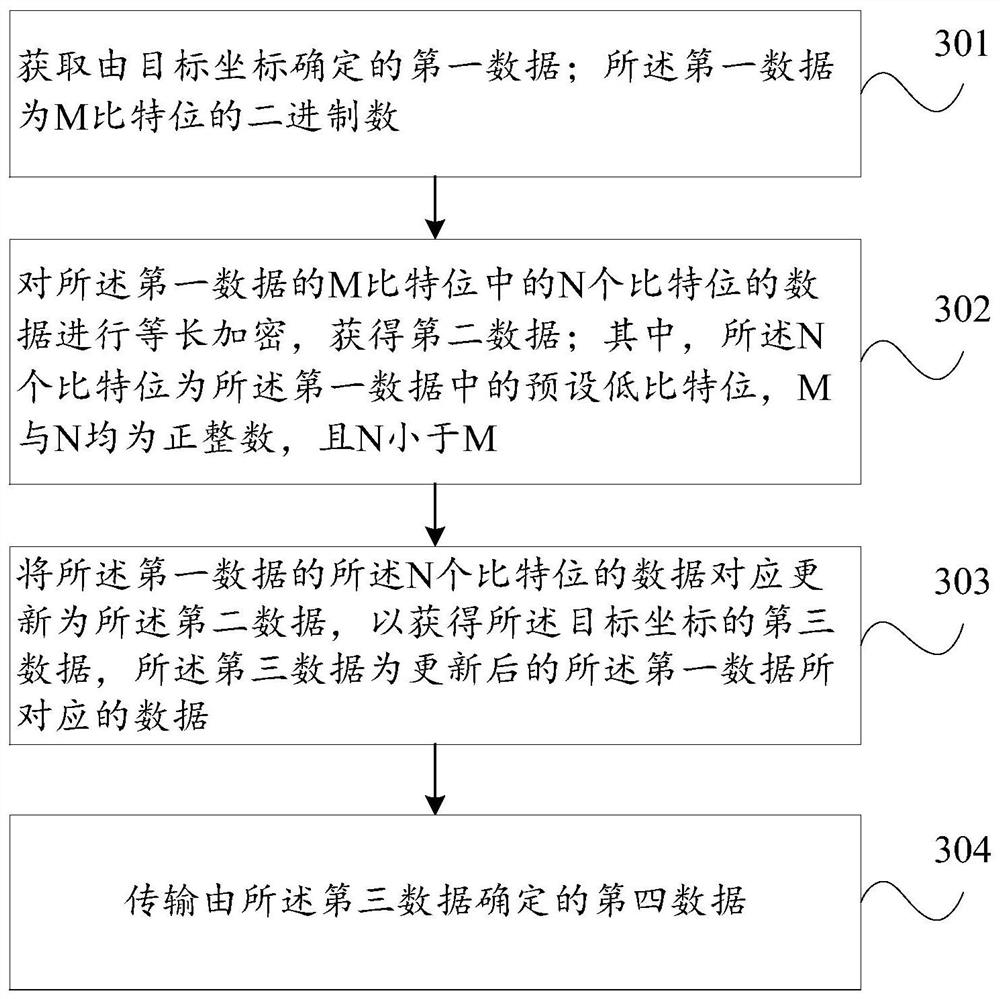
[0073] A) the latitude and longitude coordinate value of decimal system is converted into binary number;
[0074] B) Select and set the encryption bit of longitude and latitude coordinates. The encryption bit of longitude coordinate is selected from the low M1 bit of the longitude binary coordinate, and the encryption bit of latitude coordinate is selected from the low M2 of the latitude binary coordinate. The encryption bit can be continuous or discontinuous, and can be an entire byte It can also be a non-integer byte, and the number of encrypted bits for longitude coordinates is X1, and the number of encrypted bits for latitude coordinates is X2;
[0075] C) Encrypt the longitude and latitude encrypted bit data respectively, and return equal-length encrypted values, which are X1 bits and X2 bits respectively;
[0076] D) replace the X1 and X2 bit encrypted bit data in the original latitude and longitude binary coordinate value with the encrypted value;
[0077] E) Convert t...
example 2
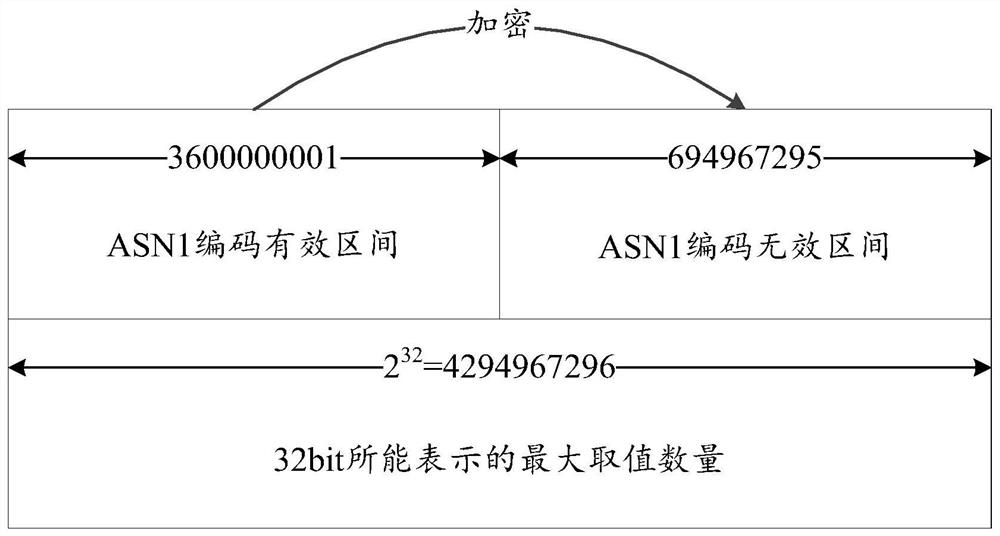
[0080]A) Preprocessing the latitude and longitude coordinates, subtracting the minimum value of the effective range of coordinates stipulated by the ASN.1 UPER encoding rule, to obtain the decimal number corresponding to the first data; is a binary number, the difference between the two is the first data; among them, the minimum value of longitude is -1799999999, and the minimum value of latitude is -900000000;
[0081] B) Select and set the longitude and latitude coordinate encryption bits after preprocessing, the longitude coordinate encryption bits are selected from the low M1 bits of the longitude binary coordinates, the latitude coordinate encryption bits are selected from the latitude binary coordinates low M2 bits, the encryption bits can be continuous or discontinuous, and can be It can be an integer byte or a non-integral byte. Note that the number of encrypted bits for longitude coordinates is X1, and the number of encrypted bits for latitude coordinates is X2;
[00...
example 3
[0092] A) ASN.1UPER encoding is performed on the decimal latitude and longitude coordinates;
[0093] B) Set the longitude and latitude coordinate encryption bit, the longitude coordinate encryption bit is selected from the low M1 bit of the longitude data segment in the ASN.1 code stream, the latitude coordinate encryption bit is selected from the low M2 of the latitude and latitude data segment in the ASN.1 code stream, the encryption bit It can be continuous or discontinuous, and it can be an integer byte or a non-integral byte. Note that the number of encrypted bits for longitude coordinates is X1, and the number of encrypted bits for latitude coordinates is X2;
[0094] C) Encrypt the longitude and latitude encrypted bit data respectively, and return the encrypted data of equal length, which are X1 bits and X2 bits respectively;
[0095] D) Replace the X1 and X2 encrypted bit data of the longitude and latitude data segment in the ASN.1 code stream with the encrypted data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com