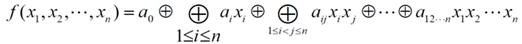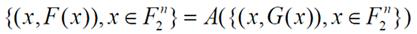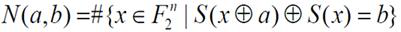S-box parameterization design method based on bit AND operation and storage medium
A parametric design and bit-based technology, applied to encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve problems such as large quantities, uncontrollable cipher properties, and occupation of storage resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] This embodiment provides a kind of S-box parametric design method based on bit-and operation, comprising the following steps:
[0062] CSH1: For the selected S-box size n, randomly select F 2 n-2 → F 2 The Boolean function f 1 , f 2 , f 1 , f 2 The algebraic degree is greater than or equal to 2 and its algebraic normal form does not contain 1-degree terms and constant terms; specifically, f 1 , f 2 Both include 2 U A non-zero Boolean function where U=2 n-2 -n+1;
[0063] CSH2: n-bit input data to S-box (x 0 ,x 1 ,x 2 ,...,x n-2 ,x n-1 ), traverse {0,1,…,2 in turn n -1} The n-bit binary vectors corresponding to all integer values {(0,0,0,…,0,0),(0,0,0,…,0,1),…,(1,1,1 ,…,1,1)}, an n-bit binary vector (x 0 ,x 1 ,x 2 ,...,x n-2 ,x n-1 ), first perform multiple rounds of n-branched generalized Feistel structure round transformation, and then perform nonlinear transformation, and perform bit combination on the operation results to obtain n The value o...
Embodiment 2
[0089] This embodiment is on the basis of embodiment 1:
[0090] For the current mainstream S-boxes in domestic and foreign cryptographic algorithms, set n=8, through the above-mentioned steps CSH1 to CSH3 in Embodiment 1, obtain the 8-bit S-box parameterization example commonly used in the actual algorithm, namely:
[0091] Denote the 8-bit input data of the S box as (x 0 ,x 1 ,x 2 ,x 3 ,x 4 ,x 5 ,x 6 ,x 7 ), the 8-bit output data of the S box is denoted as (y 0 ,y 1 ,y 2 ,y 3 ,y 4 ,y 5 ,y 6 ,y 7 ), the 14-bit variable control parameter is denoted as (CS 0 ,CS 1 ,CS 2 ,CS 3 ,CS 4 ,CS 5 ,CS 6 ,CS 7 ,CS 8 ,CS 9 ,CS 10 ,CS 11 ,CS 12 ,CS 13 ), the 8-bit intermediate variable is denoted as (t 0 ,t 1 ,t 2 ,t 3 ,t 4 ,t 5 ,t 6 ,t 7 ), the 2-bit intermediate variable is denoted as (T 0 , T 1 ), specifically including steps QCSH1 to QCSH3:
[0092] QCSH1: For the selected S-box specification n=8, randomly select F 2 6 → F 2 The Boolean function...
Embodiment 3
[0106] This embodiment is on the basis of embodiment 1:
[0107] Considering the resource lightweight requirements of the hardware implementation of the cryptographic algorithm of the resource-constrained device and the equivalent gate, this embodiment implements f in Embodiment 1 1 , f 2 Make the following qualifications: f 1 , f 2 The algebraic degree of is 2 and its algebraic normal form contains only 2 terms of degree 2. Utilize the method that this embodiment 1 provides to produce hardware to realize equivalent gate low 8 8 parameterized S-boxes, searched by computer programs, under the above-mentioned limited conditions, according to the design method in this embodiment 1, 52 new 8-bit lightweight S-boxes can be found, and their differential uniformity is not greater than 16. The linearity is not lower than 96.
[0108] One of the 52 types of 8-bit lightweight S-boxes is specifically given below, and a 5-bit parameter (CS0 ,CS 1 ,CS 2 ,CS 3 ,CS 4 ) control to g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com