A Power Attack Test System Based on Attack Topology
An attack test and electric power technology, which is applied in the transmission system, digital transmission system, electrical components, etc., can solve the problem of not being able to provide simulated attack samples
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The following description serves to disclose the invention to enable those skilled in the art to practice the invention. The preferred embodiments described below are given by way of example only, and other obvious modifications will occur to those skilled in the art. The basic principles of the invention defined in the following description may be applied to other embodiments, variations, improvements, equivalents, and other technical solutions without departing from the spirit and scope of the invention.
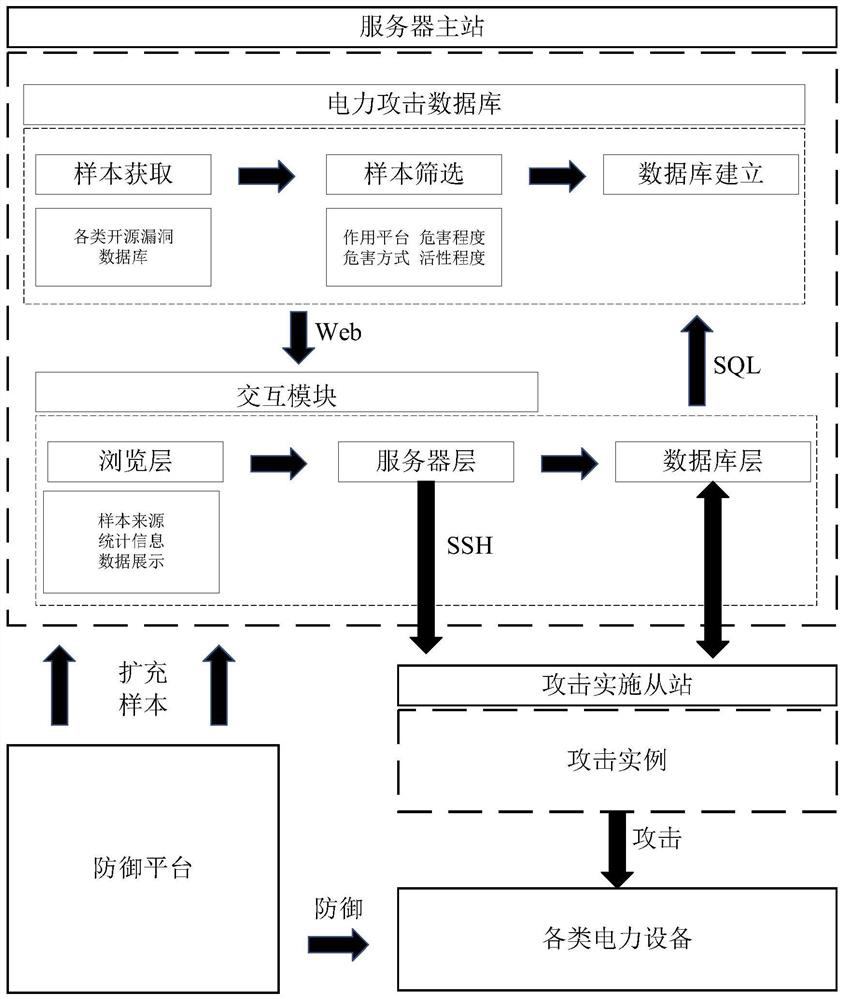
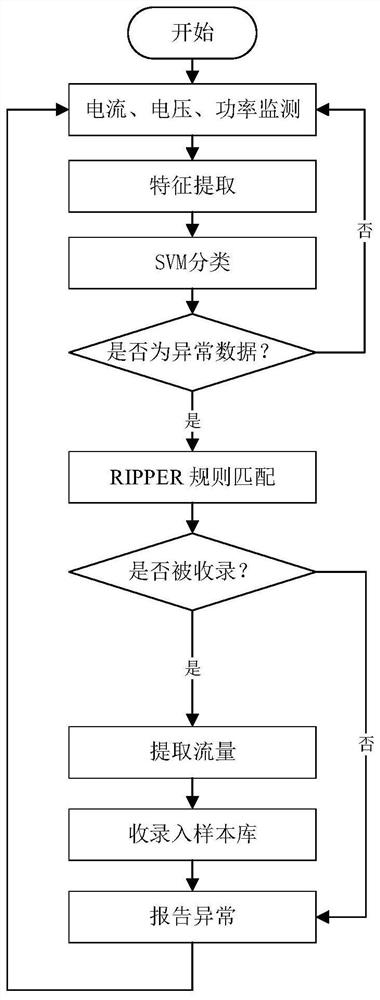
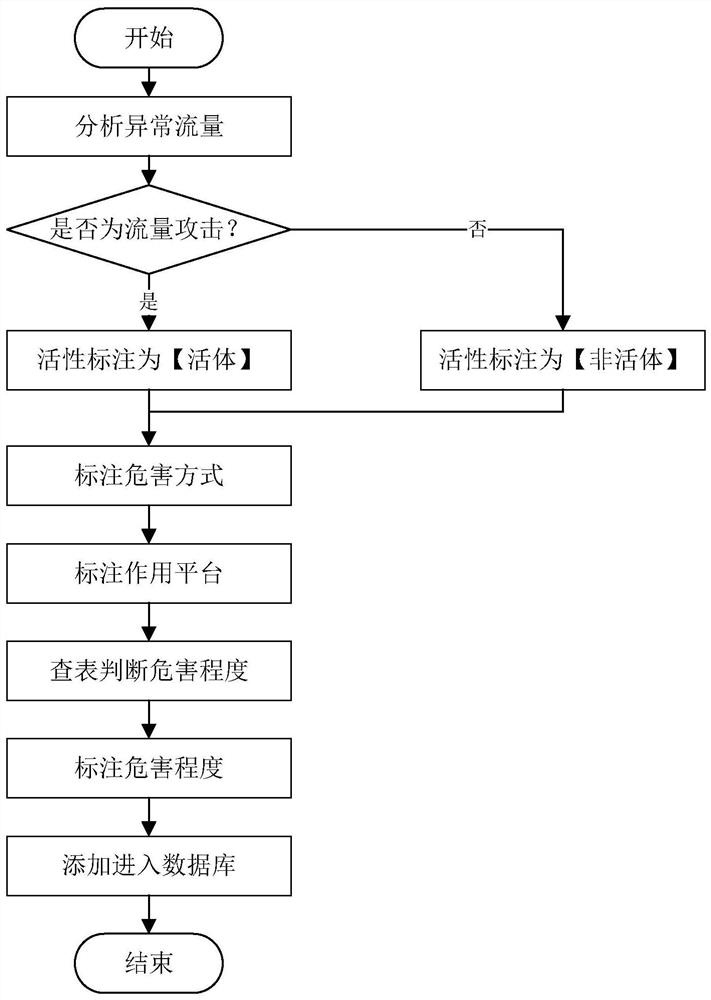
[0023] like figure 1 As shown, the construction process of the power attack test system of the present invention includes the following steps:
[0024] 1) Construction of power attack sample database:
[0025] ①Data acquisition: The data sources of the power attack sample database are divided into two types. One is basic data, the source of which is China's National Information Security Vulnerability Sharing Platform, National Information Security Vulnerability D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com