Trusted cloud-based large-scale computing service configuration method and system
A technology for computing services and configuration methods, applied in computing, program control design, program control devices, etc., can solve the problem of high cost of trusted computing resources, and achieve the effect of improving utilization and realizing trusted computing services.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] The purpose of this embodiment is to provide a large-scale computing service configuration method based on trusted cloud.
[0035] Such as figure 2 As shown, a large-scale computing service configuration method based on trusted cloud, including:
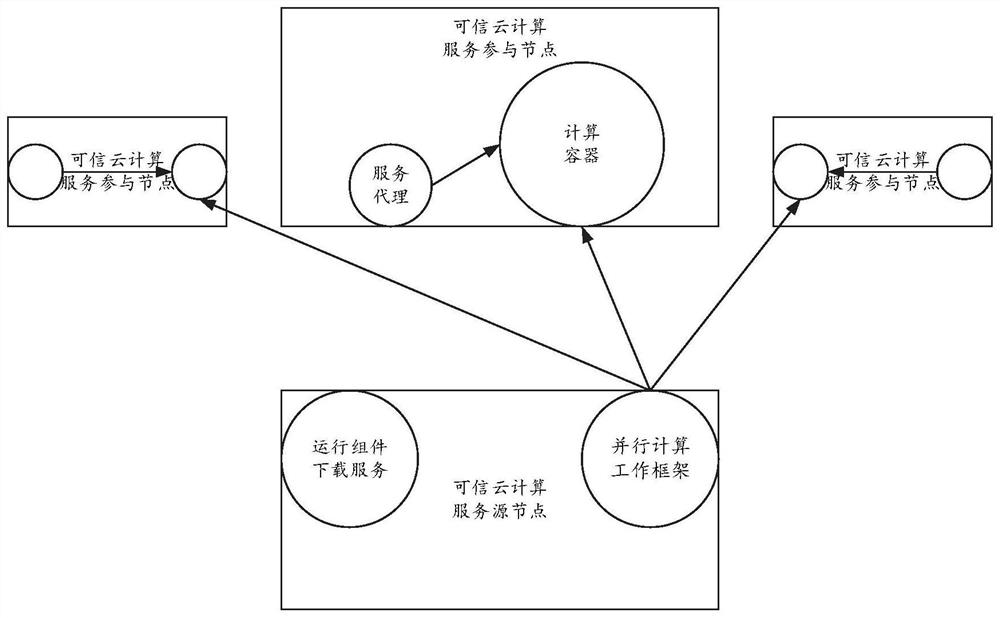
[0036] A computing service network is defined in advance, the computing service network includes several computing nodes, and a trusted computing node is set in the computing nodes as a source node of computing services;
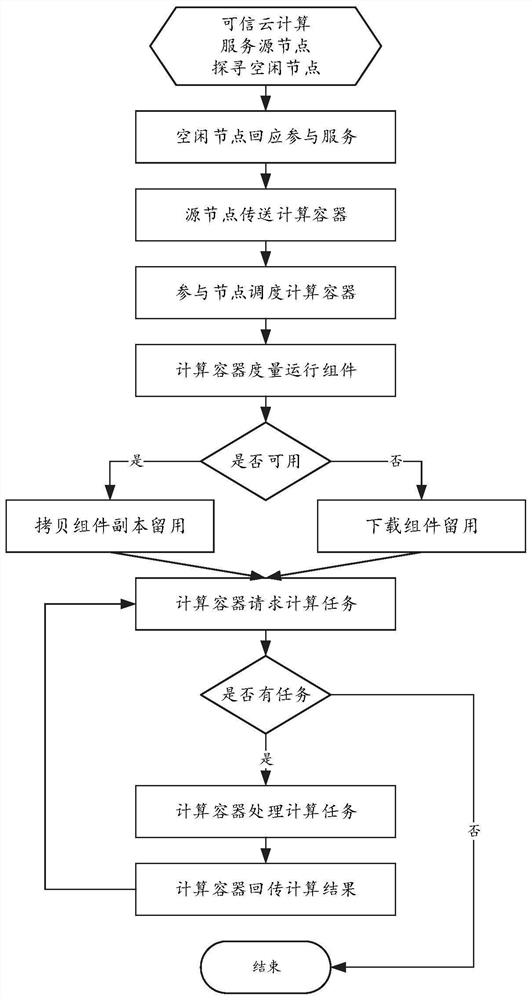
[0037] The source node queries idle computing nodes and transmits computing containers to them;
[0038] After the idle computing node receives the computing container, it starts the computing container through the virtual root of trust; the source node and all the computing containers that have been started form a flexibly scalable trusted cloud;
[0039] Based on the parallel computing working framework, the source node decomposes the computing task into several subtasks, assigns the subtasks to the com...
Embodiment 2
[0047] The purpose of this embodiment is to provide a large-scale computing service system based on a trusted cloud.
[0048] A trusted cloud-based large-scale computing service configuration system, including:
[0049] The computing service network determination module is configured to predefine a computing service network, the computing service network includes several computing nodes, and a trusted computing node is set in the computing nodes as a source node of computing services;
[0050] The trusted cloud building module is configured such that the source node queries an idle computing node and transmits a computing container to it; after receiving the computing container, the idle computing node starts the computing container through a virtual trusted root; the source node and All started-up computing containers form a flexible and scalable trusted cloud;
[0051] The task computing module is configured such that the source node decomposes the computing task into sever...
Embodiment 3
[0053] The purpose of this embodiment is to provide an electronic device.
[0054] An electronic device, including a memory, a processor, and a computer program stored and run on the memory, when the processor executes the program, the method for configuring a trusted cloud-based large-scale computing service is implemented, including:
[0055] A computing service network is defined in advance, the computing service network includes several computing nodes, and a trusted computing node is set in the computing nodes as a source node of computing services;
[0056] The source node queries idle computing nodes and transmits computing containers to them;
[0057] After the idle computing node receives the computing container, it starts the computing container through the virtual root of trust; the source node and all the computing containers that have been started form a flexibly scalable trusted cloud;
[0058] Based on the parallel computing working framework, the source node d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com