Traceability method and data packet marking device based on data packet marking
A technology for marking devices and data packets, which is applied in the field of network security and can solve the problems of unable to implement Internet access personnel and terminals.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
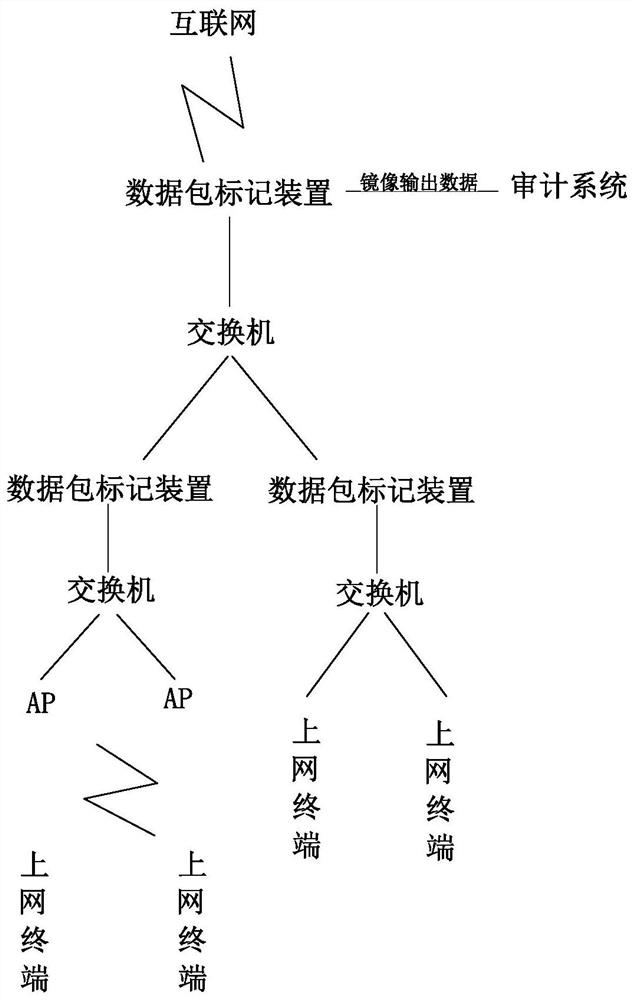
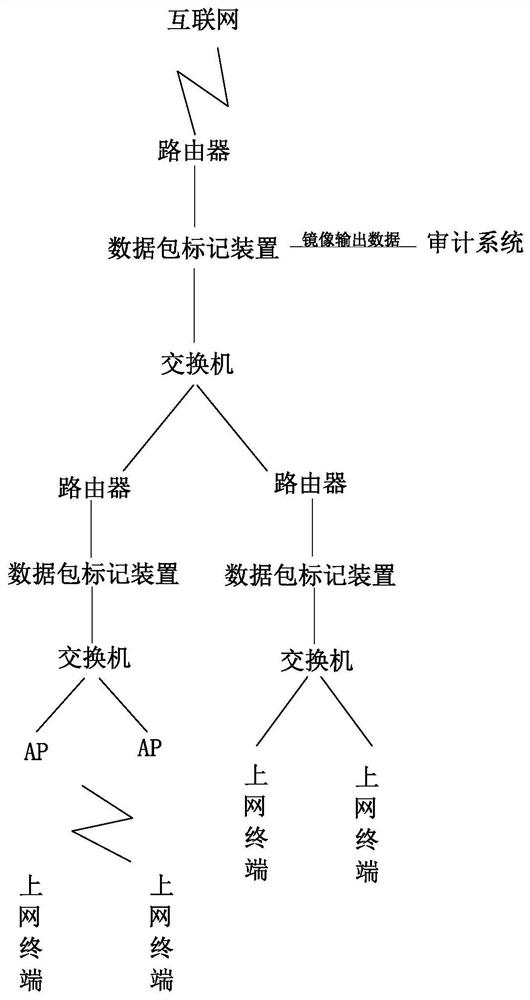
[0046] Such as Figure 1 to Figure 4 As shown, the data packet marking device includes a memory connected to a processor, the processor includes a data message input module and a data message output module, and the data message input module and the data message output module are connected to the data message traceability marking module, the data message A message address conversion module and a data message traceability mark removal module, the data message traceability mark module is connected with a data message mirroring module, and the data message mirroring module is connected to an audit system by communication;
[0047] Data message input module: used to access and process data messages;
[0048] Data message traceability marking module: used to perform traceability marking processing on the data message, and mark the traceability marking information at the end of the data message;
[0049] Data packet address translation module: used for network address translation of...
Embodiment 2
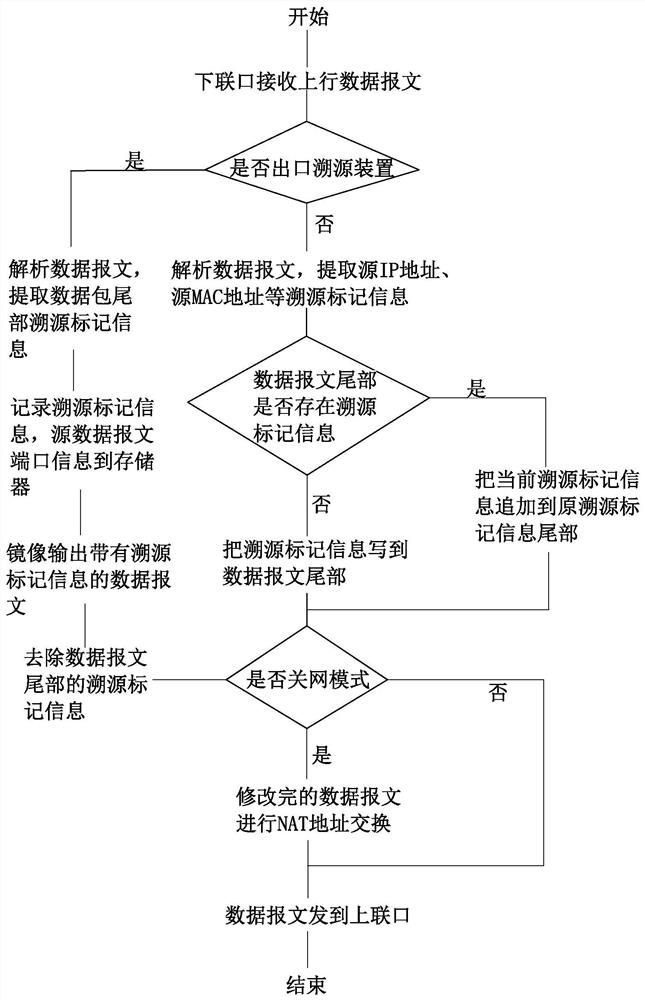
[0058] A traceability method based on packet marking, including the following steps:
[0059] Step 1, judging whether the data message is an uplink data message or a downlink data message, if it is an uplink data message, then enter step 2, if it is a downlink data message, then enter step 3;
[0060]Step 2. Processing of uplink data messages: receive uplink data messages to extract traceability information and mark them, record traceability mark information when data is exported, mirror data messages with traceability mark information to the audit system, forward and remove traceability marks information data packets to the upper network;
[0061] Step 3. Processing of the downlink data message: When receiving the downlink data message, query the traceability mark information record at the time of export, mark the obtained traceability mark information record at the end of the data message copied by the mirror, then output it to the audit system, and forward it Datagrams to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com