Firmware vulnerability scanning system and method based on software gene
A vulnerability scanning and firmware technology, which is applied in the direction of instruments, electronic digital data processing, platform integrity maintenance, etc., can solve problems such as no solution proposed, low accuracy of vulnerability detection, poor applicability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
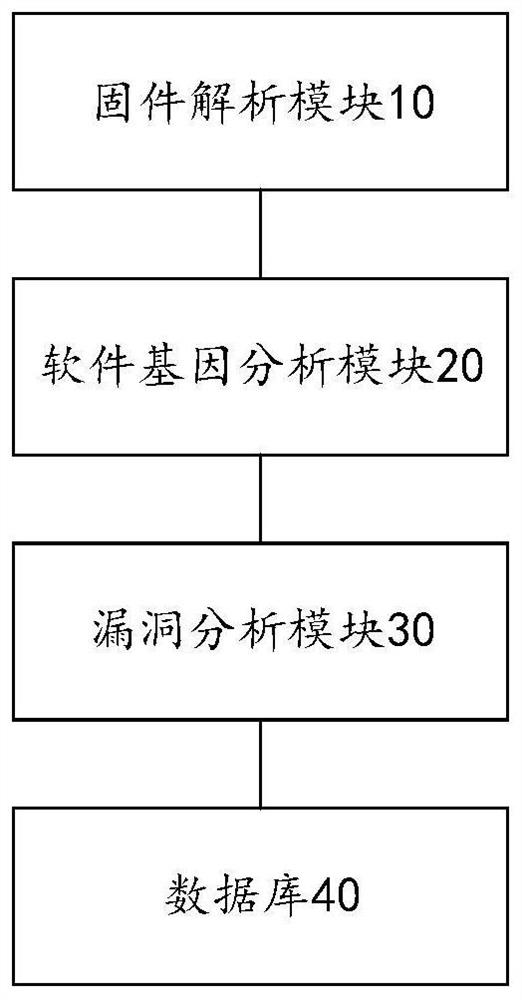
[0026] According to an embodiment of the present invention, an embodiment of a firmware vulnerability scanning system based on software genes is provided, figure 1 is a schematic diagram of a software gene-based firmware vulnerability scanning system according to an embodiment of the present invention, such as figure 1 As shown, the system includes: a firmware analysis module 10 , a software gene analysis module 20 and a vulnerability analysis module 30 .
[0027] The firmware parsing module 10 is configured to parse and extract the firmware file of the firmware to be scanned to obtain the data file of the firmware to be scanned;
[0028] It should be noted that the types of firmware to be scanned at least include: compressed firmware and target firmware, where the target firmware is a file in a file system whose file type is data.
[0029] Therefore, the firmware parsing module has parsers of different versions corresponding to different types of device firmware.
[0030] F...
Embodiment 2
[0054] The embodiment of the present invention also provides a software gene-based firmware vulnerability scanning method. The software gene-based firmware vulnerability scanning device described in the first embodiment above is used to execute the firmware vulnerability scanning method provided in the embodiment of the present invention, as follows It is a specific introduction of the software gene-based firmware vulnerability scanning method provided by the embodiment of the present invention.
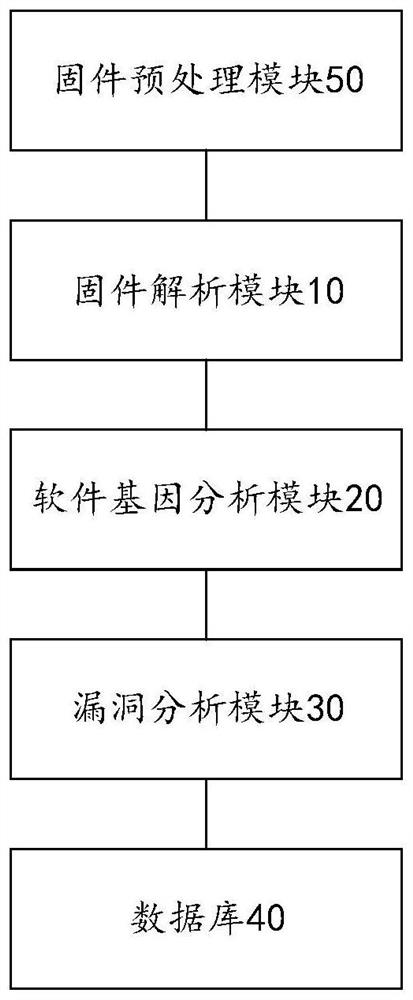
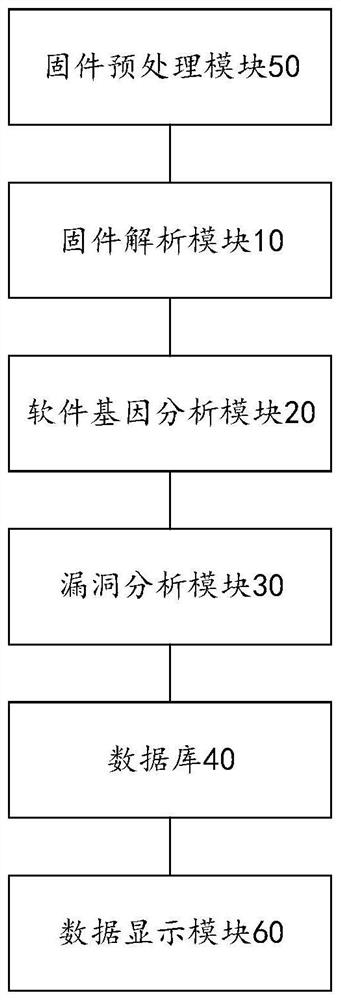
[0055] Such as Figure 4 as shown, Figure 4 It is a flowchart of the above-mentioned firmware vulnerability scanning method based on software genes, and the firmware vulnerability scanning method includes:
[0056] Step S102, obtaining the firmware to be scanned, and parsing and extracting the firmware file of the firmware to be scanned to obtain the data file of the firmware to be scanned;
[0057] Step S104, performing software gene extraction on the data file to obtain the soft...
Embodiment 3
[0061] An embodiment of the present invention also provides a computer-readable storage medium, on which a computer program is stored, and when the computer program is run by a processor, the steps of the method described in the second embodiment above are executed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com